|
DOFE J, FREY J, and YU Qiaoyu. Hardware security assurance in emerging IoT applications[C]. 2016 IEEE International Symposium on Circuits and Systems, Montreal, Canada, 2016: 2050–2053.
|
|
SUMATHI G, SRIVANI L, MURTHY D T, et al. A review on HT attacks in PLD and ASIC designs with potential defence solutions[J]. IETE Technical Review, 2018, 35(1): 64–77. doi: 10.1080/02564602.2016.1246385
|
|
CHAKRABORTY R S, WOLFF F, PAUL S, et al. MERO: A statistical approach for hardware Trojan detection[C]. The 11th International Workshop on Cryptographic Hardware and Embedded Systems, Switzerland, 2009: 396–410.
|
|
SAHA S, CHAKRABORTY R S, NUTHAKKI S S, et al. Improved test pattern generation for hardware Trojan detection using genetic algorithm and Boolean satisfiability[C]. The 17th International Workshop on Cryptographic Hardware and Embedded Systems, Saint-Malo, France, 2015: 577–596.
|
|
LESPERANCE N, KULKARNI S, CHENG K T, et al. Hardware Trojan detection using exhaustive testing of k-bit subspaces[C]. The 20th Asia and South Pacific Design Automation Conference, Chiba, Japan, 2015: 755–760.
|
|
XUE Mingfu, HU Aiqun, and LI Guyue. Detecting hardware Trojan through heuristic partition and activity driven test pattern generation[C]. 2014 Communications Security Conference, Beijing, China, 2014: 1–6.
|
|
AGRAWAL D, BAKTIR S, KARAKOYUNLU D, et al. Trojan detection using IC fingerprinting[C]. 2007 IEEE Symposium on Security and Privacy, Berkeley, USA, 2007: 296–310.
|
|
HE Jiaji, ZHAO Yiqiang, GUO Xiaolong, et al. Hardware Trojan detection through chip-free electromagnetic side-channel statistical analysis[J]. IEEE Transactions on Very Large Scale Integration (VLSI) Systems, 2017, 25(10): 2939–2948. doi: 10.1109/TVLSI.2017.2727985
|
|
XIAO Kan, ZHANG Xuehui, and TEHRANIPOOR M. A clock sweeping technique for detecting hardware trojans impacting circuits delay[J]. IEEE Design & Test, 2013, 30(2): 26–34. doi: 10.1109/MDAT.2013.2249555
|
|
薛明富, 王箭, 胡爱群. 自适应优化的二元分类型硬件木马检测方法[J]. 计算机学报, 2018, 41(2): 439–451. doi: 10.11897/SP.J.1016.2018.00439XUE Mingfu, WANG Jian, and HU Aiqun. Adaptive optimization of two-class classification-based hardware Trojan detection method[J]. Chinese Journal of Computers, 2018, 41(2): 439–451. doi: 10.11897/SP.J.1016.2018.00439
|
|
骆扬, 王亚楠. 物理型硬件木马失效机理及检测方法[J]. 物理学报, 2016, 65(11): 110602. doi: 10.7498/APS.65.110602LUO Yang and WANG Yanan. Physical hardware trojan failure analysis and detection method[J]. Acta Physica Sinica, 2016, 65(11): 110602. doi: 10.7498/APS.65.110602
|
|
张鹏, 王新成, 周庆. 基于投影寻踪分析的芯片硬件木马检测[J]. 通信学报, 2013, 34(4): 122–126. doi: 10.3969/J.ISSN.1000-436x.2013.04.014ZHANG Peng, WANG Xincheng, and ZHOU Qing. Hardware Trojans detection based on projection pursuit[J]. Journal on Communications, 2013, 34(4): 122–126. doi: 10.3969/J.ISSN.1000-436x.2013.04.014
|
|
李雄伟, 王晓晗, 张阳, 等. 一种基于核最大间距准则的硬件木马检测新方法[J]. 电子学报, 2017, 45(3): 656–661. doi: 10.3969/J.ISSN.0372-2112.2017.03.023LI Xiongwei, WANG Xiaohan, ZHANG Yang, et al. A new hardware Trojan detection method based on kernel maximum margin criterion[J]. Acta Electronica Sinica, 2017, 45(3): 656–661. doi: 10.3969/J.ISSN.0372-2112.2017.03.023
|
|
赵毅强, 刘沈丰, 何家骥, 等. 基于自组织竞争神经网络的硬件木马检测方法[J]. 华中科技大学学报: 自然科学版, 2016, 44(2): 51–55. doi: 10.13245/J.HUST.160211ZHAO Yiqiang, LIU Shenfeng, HE Jiaji, et al. Hardware Trojan detection technology based on self-organizing competition neural network[J]. Journal of Huazhong University of Science and Technology:Natural Science Edition, 2016, 44(2): 51–55. doi: 10.13245/J.HUST.160211
|
|
YAN Shuicheng, XU Dong, ZHANG Benyu, et al. Graph embedding and extensions: A general framework for dimensionality reduction[J]. IEEE Transactions on Pattern Analysis and Machine Intelligence, 2007, 29(1): 40–51. doi: 10.1109/TPAMI.2007.250598
|
|
何进荣, 丁立新, 崔梦天, 等. 基于矩阵指数变换的边界Fisher分析[J]. 计算机学报, 2014, 37(10): 2196–2205.HE Jinrong, DING Lixin, CUI Mengtian, et al. Marginal Fisher analysis based on matrix exponential transformation[J]. Chinese Journal of Computers, 2014, 37(10): 2196–2205.
|
|
李艳霞, 柴毅, 胡友强, 等. 不平衡数据分类方法综述[J]. 控制与决策, 2019, 34(4): 673–688. doi: 10.13195/J.KZYJC.2018.0865LI Yanxia, CHAI Yi, HU Youqiang, et al. Review of imbalanced data classification methods[J]. Control and Decision, 2019, 34(4): 673–688. doi: 10.13195/J.KZYJC.2018.0865
|





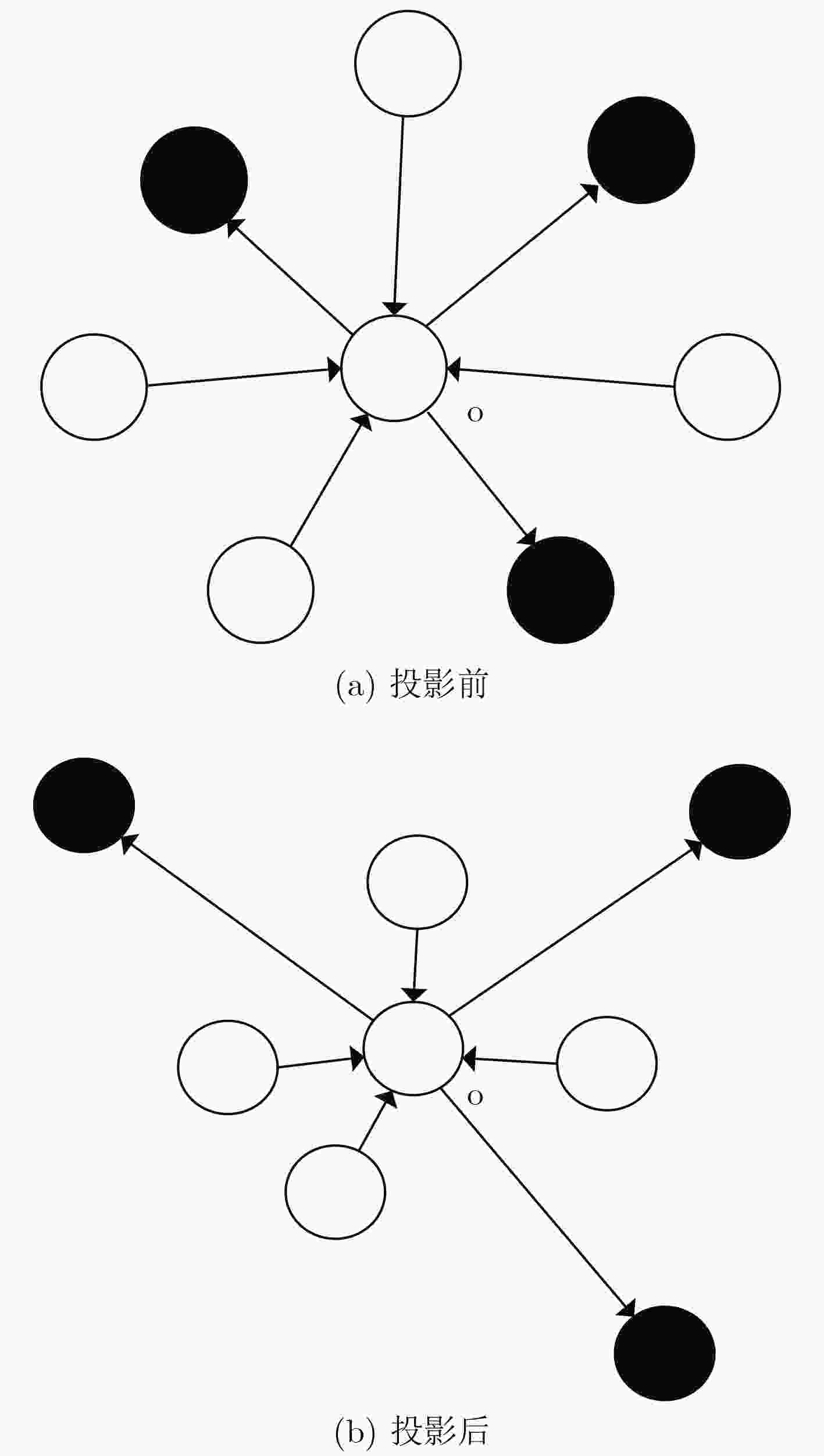
 下载:
下载:
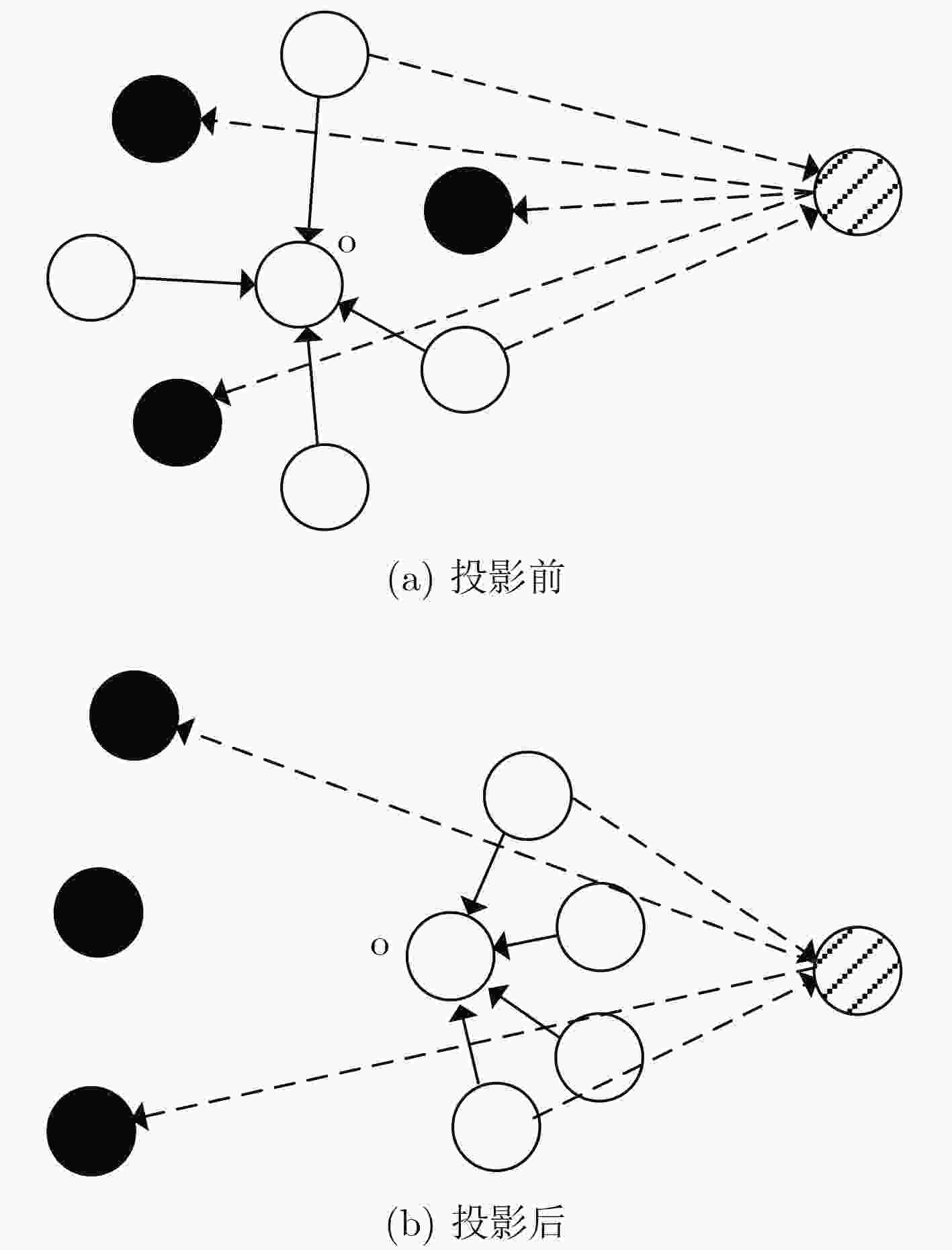
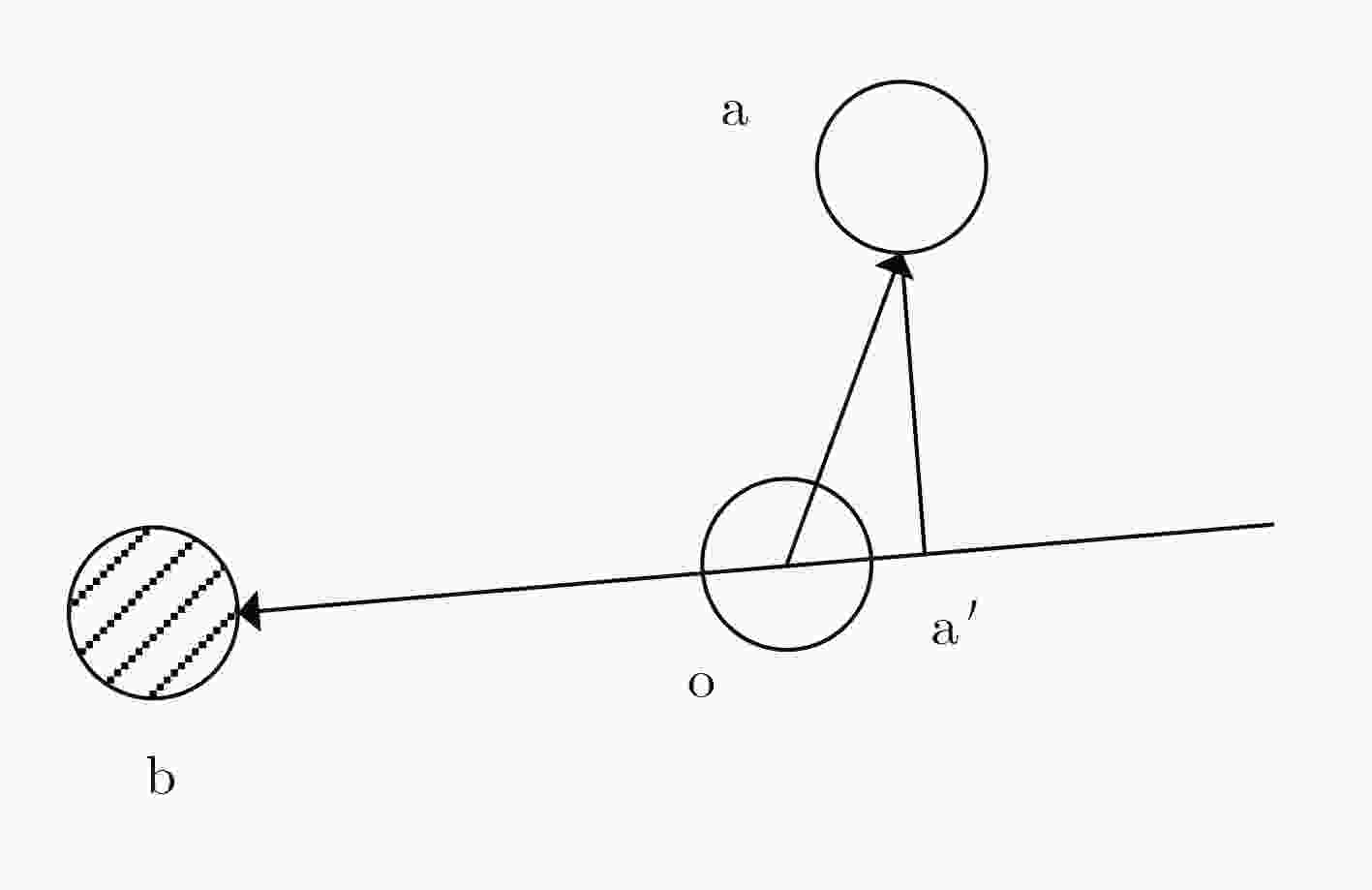
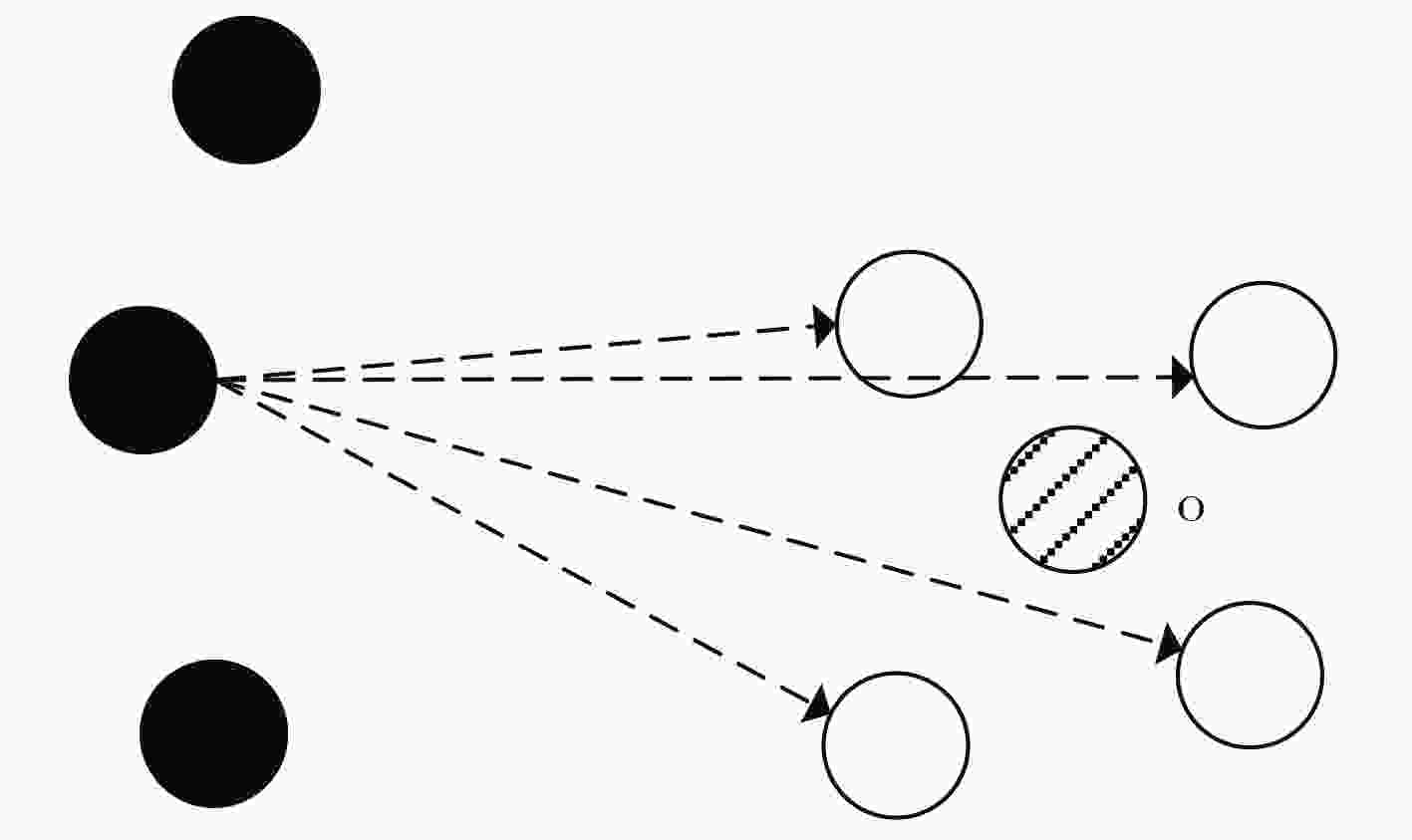
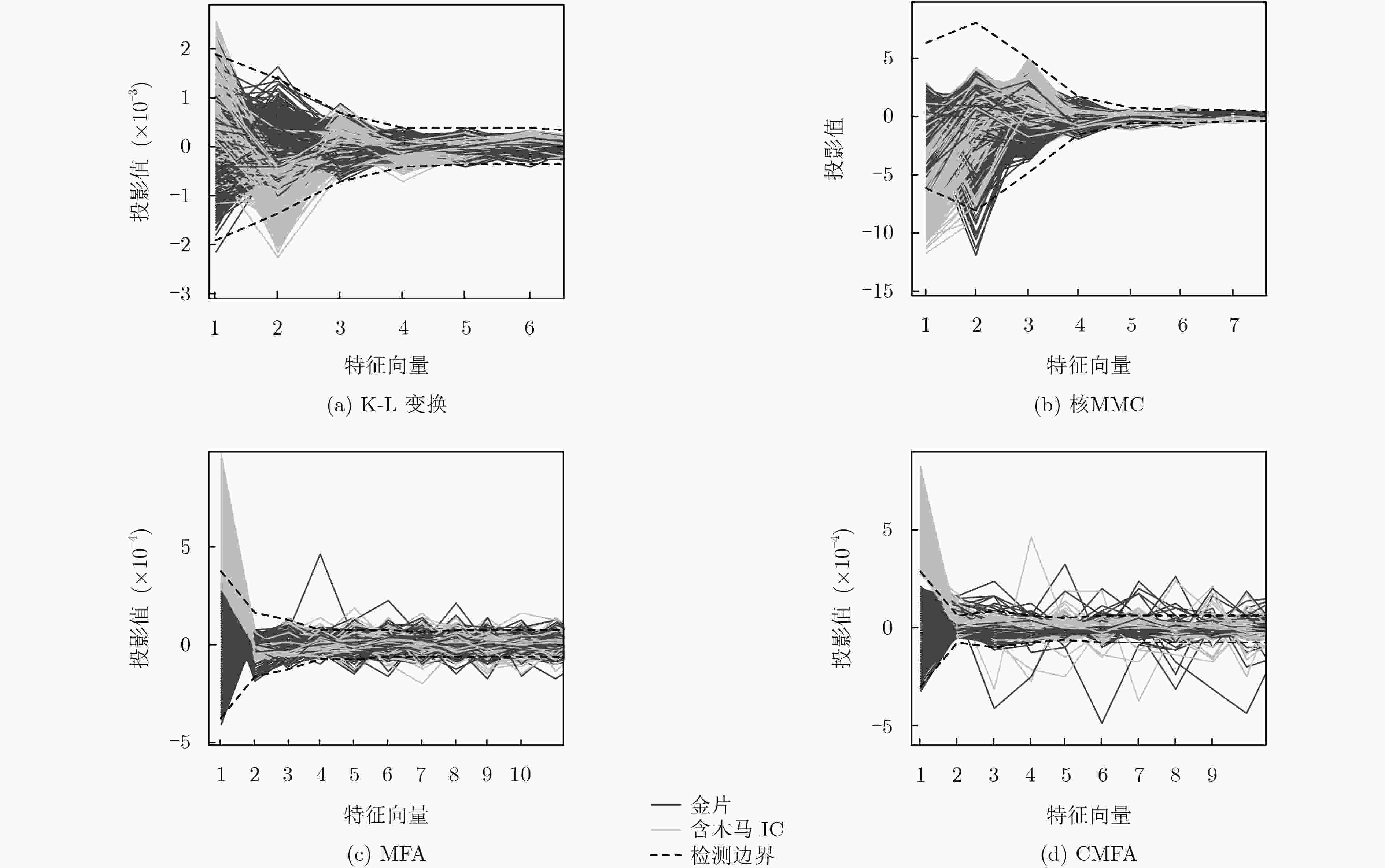
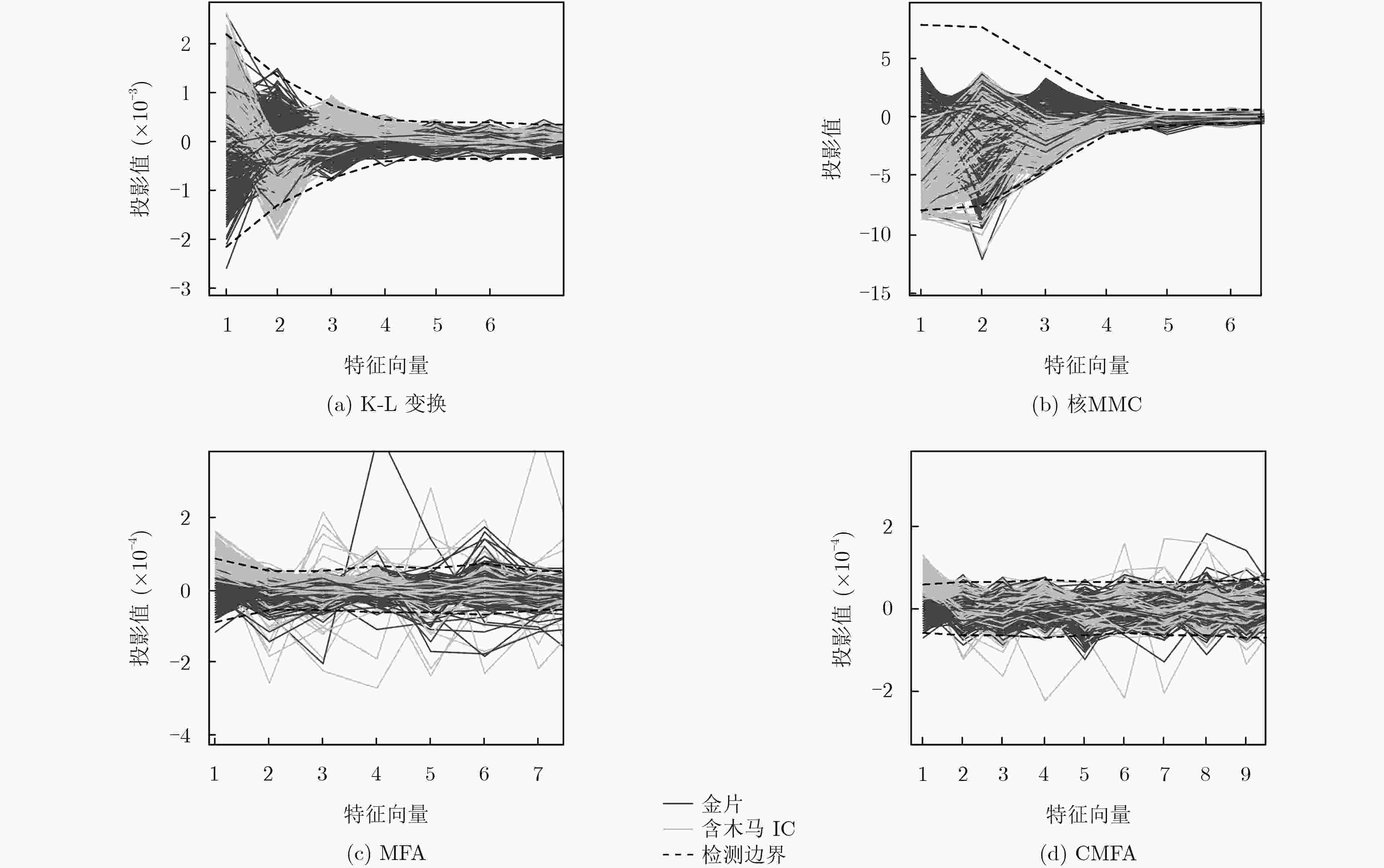
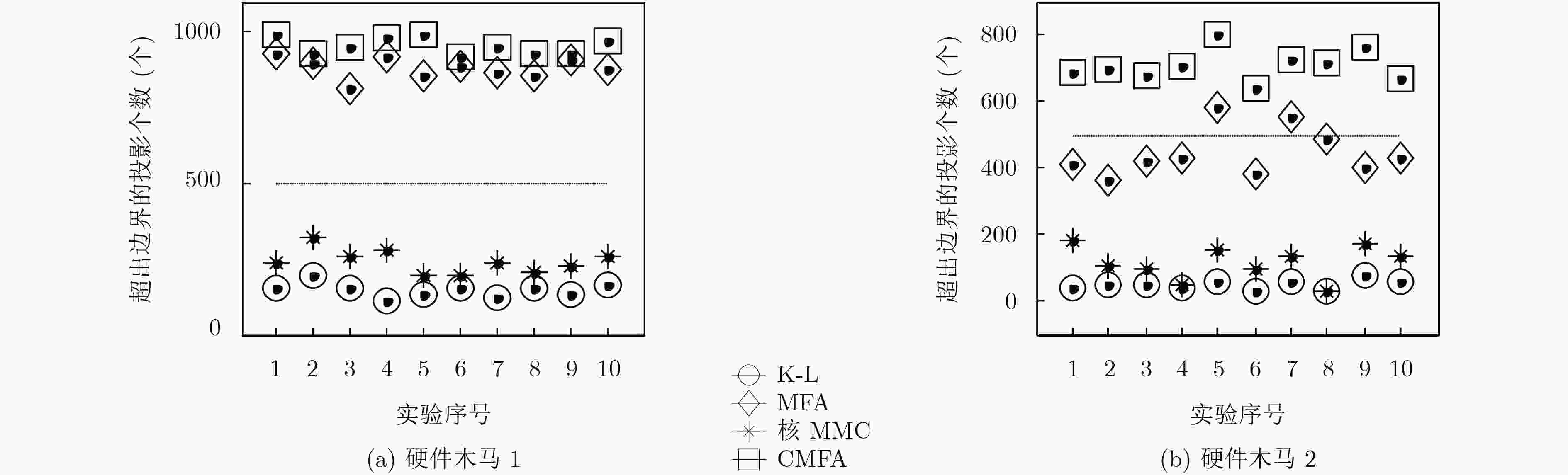


 下载:
下载:
