Research on Network Dynamic Threat Analysis Technology Based on Attribute Attack Graph
-
摘要: 该文首先利用属性攻击图理论构建了网络动态威胁分析属性攻击图(DT-AAG)模型,该模型在全面刻画系统漏洞和网络服务导致的威胁转移关系的基础上,结合通用漏洞评分标准(CVSS)和贝叶斯概率转移计算方法设计了威胁转移概率度量算法;其次基于构建的DT-AAG模型,利用威胁与漏洞、服务间的关联关系,设计了动态威胁属性攻击图生成算法(DT-AAG-A),并针对生成的属性攻击图存在的威胁传递环路问题,设计了环路消解机制;最后通过实验验证了该模型和算法的有效性。Abstract: Firstly, a network Dynamic Threat Attribute Attack Graph (DT-AAG) analysis model is constructed by using Attribute Attack Graph theory. On the basis of the comprehensive description of system vulnerability and network service-induced threat transfer relationship, a threat transfer probability measurement algorithm is designed in combination with Common Vulerability Scoring System (CVSS) vulnerability evaluation criteria and Bayesian probability transfer method. Secondly, based on the model, a Dynamic Threat Attribute Attack Graph generation Algorithm (DT-AAG-A) is designed by using the relationship between the threat and the vulnerability as well as the service. What’s more, to solve the problem that threat transfer loop existing in the generated attribute attack graph, the loop digestion mechanism is designed. Finally, the effectiveness of the proposed model and algorithm is verified by experiments.
-
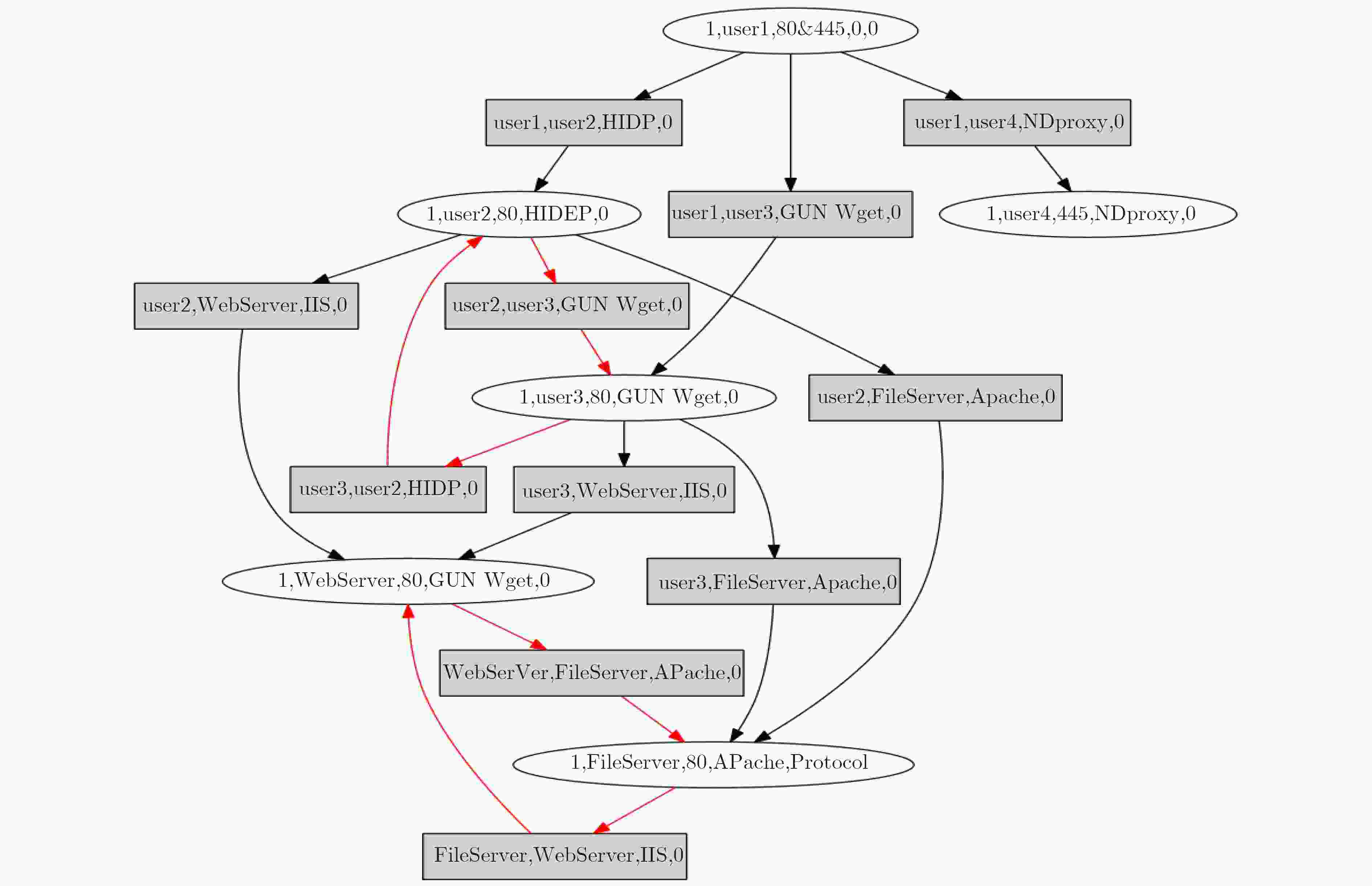
图 7 文献[8]实验图
表 1 DT-AAG-A生成算法
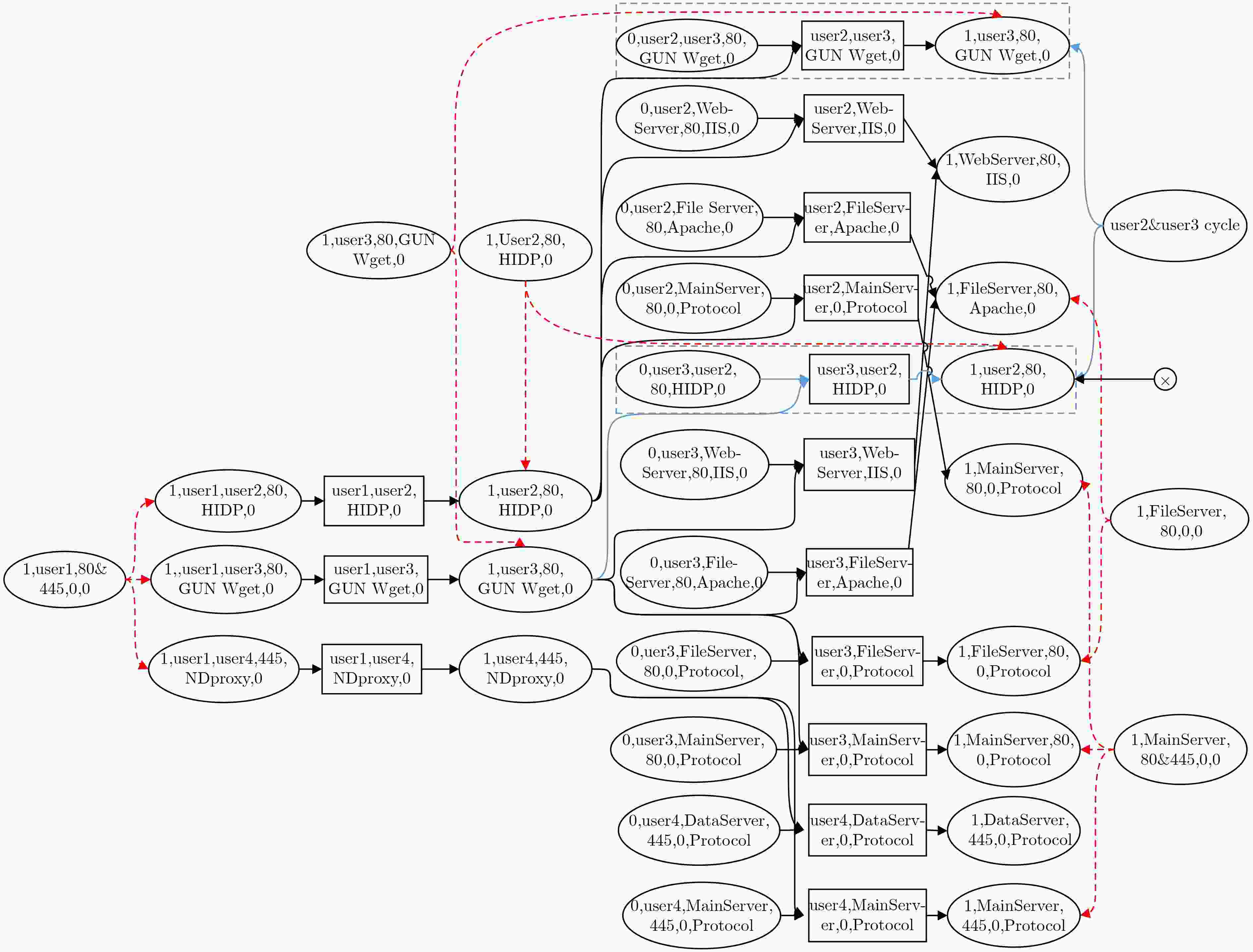
输入:DT-AAG-PL 输出:DT-AAG (1) DT-AAG-PL$ \ne \varnothing $; /* DT-AAG-PL数据库不为空 */ (2) DT-AAG${\rm{ = }}\varnothing $; /* 设置DT-AAG初始值为空 */ (3) $t,i \in $DT-AAG-PL (4) For each $t = [{\rm{I}}{{\rm{D}}_t},{\rm{IPpreCo}}{{\rm{n}}_t},{\rm{IPpostCo}}{{\rm{n}}_t}]$ (5) DO { /* 任取DT-AAG-PL中一个元素 */ (6) SearchIDIPpre (DT-AAG-PL) } (7) For rest $j \in$DT-AAG-PL DO { /* 搜索匹配DT-AAG-PL中剩余元素*/ (8) SearchIDIPpre (DT-AAG-PL, ${\rm{DT {\tiny{-}} AAG}}$); /* 范围为DT-AAG-PL 和${\rm{DT {\tiny{-}} AAG}}$ */ } (9) If DT-AAG-PL$= \varnothing${ /* 当DT-AAG-PL中所有元素都被移动 */ (10) Return DT-AAG; } (11) SearchIDIPpre (DT-AAG-PL) { (12) If ${\rm{I}}{{\rm{D}}_t} = {\rm{I}}{{\rm{D}}_i}\& \& {\rm{IPpostCo}}{{\rm{n}}_t} = {\rm{IPpostCo}}{{\rm{n}}_i}$; /* 根据ID和IP搜索匹配 */ (13) {$a = t \to i$; Put a to ${\rm{DT - AAG}}$;} /* 将匹配到的元素移到${\rm{DT {\tiny{-}} AAG}}$ */ (14) else (15) {$a = t$; Put a to ${\rm{DT {\tiny{-}} AAG}}$;} /* 将未匹配的元素移到${\rm{DT {\tiny{-}}AAG}}$中 */ } 表 2 主机与服务器存在的漏洞和协议信息表
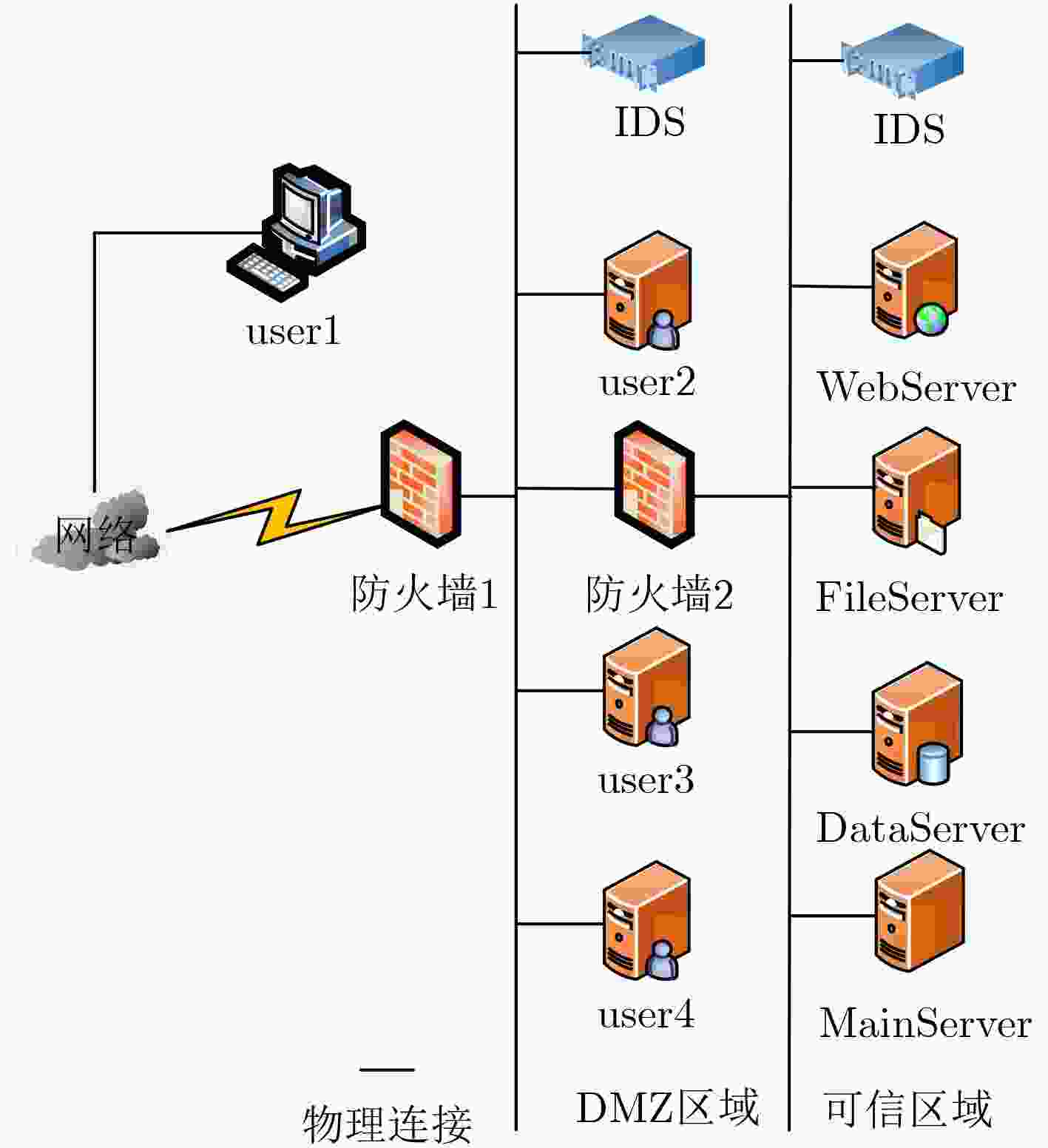
Host/Server Protocol/Vulnerability Port user1 – 80/445 user2 HIDP 80 user3 GUN Wget 80 user4 NDproxy 445 WebServer IIS 80 FileServer Protocol with user3/Apache 80 DataServer Protocol with user4 445 MainServer Protocol with user2&user3&user4 80&445 表 3 漏洞信息表
Vulnerability ExpSco+ImpSco CVE Num. HIDP 7.0 CVE-2018-8169 GUN Wget 8.8 CVE-2016-4971 NDproxy 7.2 CVE-2013-5065 IIS 7.8 CVE-2015-7597 Apache 7.5 CVE-2018-8015 表 4 攻击路径和威胁转移概率表
攻击路径 a$ \to $d$ \to $i a$ \to $d$ \to $j a$ \to $d$ \to $k a$ \to $d$ \to $l a$ \to $e a$ \to $f a$ \to $g b$ \to $j b$ \to $k b$ \to $l c$ \to $m c$ \to $n 转移概率 0.38 0.30 0.49 0.49 0.44 0.34 0.56 0.53 0.88 0.88 0.58 0.58 -
PHILLIPS C and SWILER L P. A graph-based system for network-vulnerability analysis[C]. The 1998 Workshop on New Security Paradigms, Charlottesville, Virginia, USA, 1998; 71–79. SWILER L P, PHILLIPS C, ELLIS D, et al. Computer-attack graph generation tool[C]. DARPA Information Survivability Conference and Exposition II, DISCEX’01, Anaheim, CA, USA, 2001, 2: 307–321. INGOLS K, CHU M, LIPPMANN R, et al. Modeling modern network attacks and countermeasures using attack graphs[C]. 2009 Annual Computer Security Applications Conference, Honolulu, Hawaii, USA, 2009: 117–126. 黄永洪, 吴一凡, 杨豪璞, 等. 基于攻击图的APT脆弱节点评估方法[J]. 重庆邮电大学学报(自然科学版), 2017, 29(4): 535–541. doi: 10.3979/j.issn.1673-825X.2017.04.017HUANG Yonghong, WU Yifan, YANG Haopu, et al. Graph-based vulnerability assessment for APT attack[J]. Journal of Chongqing University of Posts and Telecommunications (Natural Science Edition) , 2017, 29(4): 535–541. doi: 10.3979/j.issn.1673-825X.2017.04.017 LEE J, MOON D, KIM I, et al. A semantic approach to improving machine readability of a large-scale attack graph[J]. The Journal of Supercomputing, 2018: 1–18. doi: 10.1007/s11227-018-2394-6 胡浩, 刘玉岭, 张红旗, 等. 基于吸收Markov链的网络入侵路径预测方法[J]. 计算机研究与发展, 2018, 55(4): 831–845. doi: 10.7544/issn1000-1239.2018.20170087HU Hao, LIU Yuling, ZHANG Hongqi, et al. Route prediction method for network intrusion using absorbing markov Chain[J]. Journal of Computer Research and Development, 2018, 55(4): 831–845. doi: 10.7544/issn1000-1239.2018.20170087 HU Hao, LIU Yuling, ZHANG Hongqi, et al. Security metric methods for network multistep attacks using AMC and big data correlation analysis[J]. Security and Communication Networks, 2018, 2018: 57871012. doi: 10.1155/2018/5787102 吴迪, 连一峰, 陈恺, 等. 一种基于攻击图的安全威胁识别和分析方法[J]. 计算机学报, 2012, 35(9): 1938–1950. doi: 10.3724/SP.J.1016.2012.01938WU Di, LIAN Yifeng, CHEN Kai, et al. A security threats identification and analysis method based on attack graph[J]. Chinese Journal of Computers, 2012, 35(9): 1938–1950. doi: 10.3724/SP.J.1016.2012.01938 HOMER J, ZHANG Su, OU Xinming, et al. Aggregating vulnerability metrics in enterprise networks using attack graphs[J]. Journal of Computer Security, 2013, 21(4): 561–597. doi: 10.3233/JCS-130475 王会梅, 鲜明, 王国玉. 基于扩展网络攻击图的网络攻击策略生成算法[J]. 电子与信息学报, 2011, 33(12): 3015–3021. doi: 10.3724/SP.J.1146.2011.00414WANG Huimei, XIAN Ming, and WANG Guoyu. A network attack decision-making algorithm based on the extended attack graph[J]. Journal of Electronics &Information Technology, 2011, 33(12): 3015–3021. doi: 10.3724/SP.J.1146.2011.00414 WANG Huan, CHEN Zhanfang, ZHAO Jianping, et al. A vulnerability assessment method in industrial internet of things based on attack graph and maximum flow[J]. IEEE Access, 2018, 6: 8599–8609. doi: 10.1109/ACCESS.2018.2805690 张海霞, 苏璞睿, 冯登国. 基于攻击能力增长的网络安全分析模型[J]. 计算机研究与发展, 2007, 44(12): 2012–2019.ZHANG Haixia, SU Purui, and FENG Dengguo. A network security analysis model based on the increase in attack ability[J]. Journal of Computer Research and Development, 2007, 44(12): 2012–2019. SINGH U K, JOSHI C, and GAUD N. Information security assessment by quantifying risk level of network vulnerabilities[J]. International Journal of Computer Applications, 2016, 156(2): 37–44. doi: 10.5120/ijca2016912375 胡浩, 叶润国, 张红旗, 等. 面向漏洞生命周期的安全风险度量方法[J]. 软件学报, 2018, 29(5): 1213–1229. doi: 10.13328/j.cnki.jos.005507HU Hao, YE Runguo, ZHANG Hongqi, et al. Vulnerability life cycle oriented security risk metric method[J]. Journal of Software, 2018, 29(5): 1213–1229. doi: 10.13328/j.cnki.jos.005507 陈锋, 张怡, 苏金树, 等. 攻击图的两种形式化分析[J]. 软件学报, 2010, 21(4): 838–848. doi: 10.3724/SP.J.1001.2010.03584CHEN Feng, ZHANG Yi, SU Jinshu, et al. Two formal analyses of attack graphs[J]. Journal of Software, 2010, 21(4): 838–848. doi: 10.3724/SP.J.1001.2010.03584 叶子维, 郭渊博, 王宸东, 等. 攻击图技术应用研究综述[J]. 通信学报, 2017, 38(11): 121–132. doi: 10.11959/j.issn.1000-436x.2017213YE Ziwei, GUO Yuanbo, WANG Chendong, et al. Survey on application of attack graph technology[J]. Journal on Communications, 2017, 38(11): 121–132. doi: 10.11959/j.issn.1000-436x.2017213 CVSS v3.0 specification document[EB/OL]. https://www.first.org/cvss/specification-document, 2018. CVE. Common vulnerabilities and exposures[EB/OL]. http://cve.mitre.org/, 2018. NIST. National vulnerability database[EB/OL]. https://nvd.nist.gov/, 2018. -





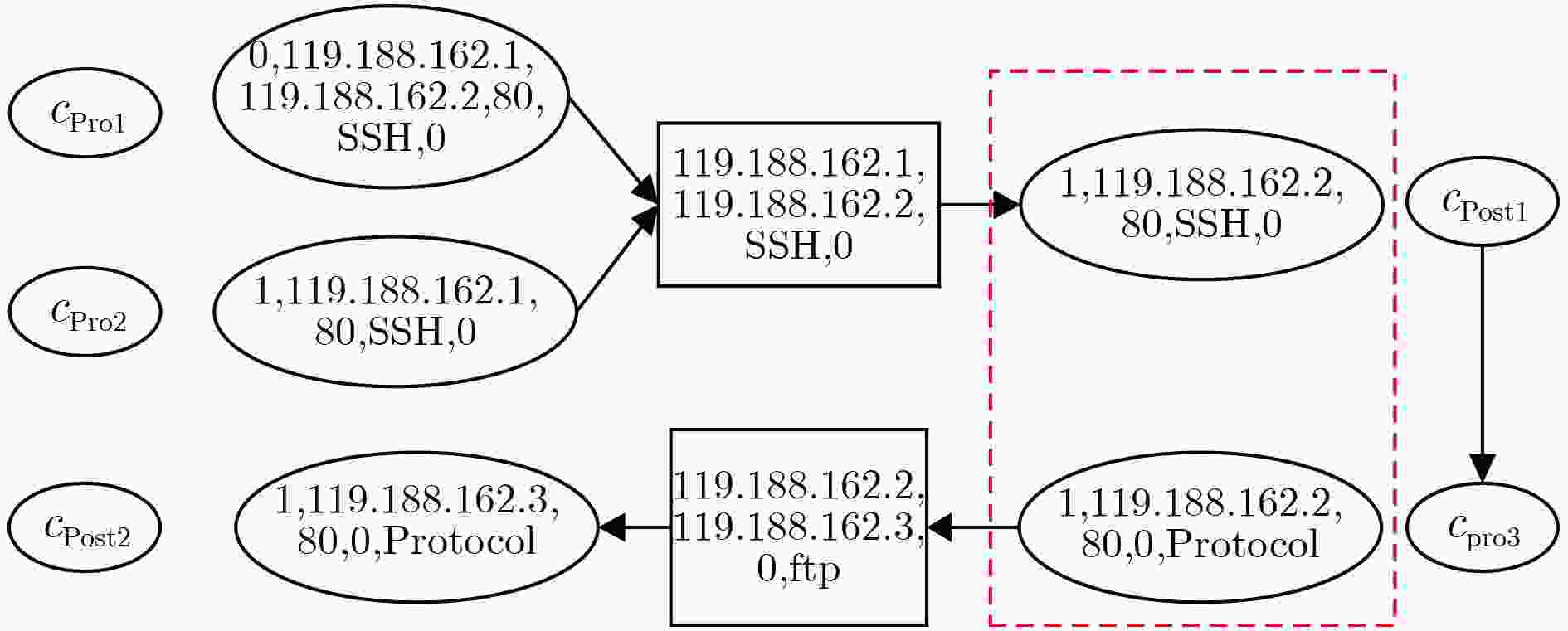
 下载:
下载:
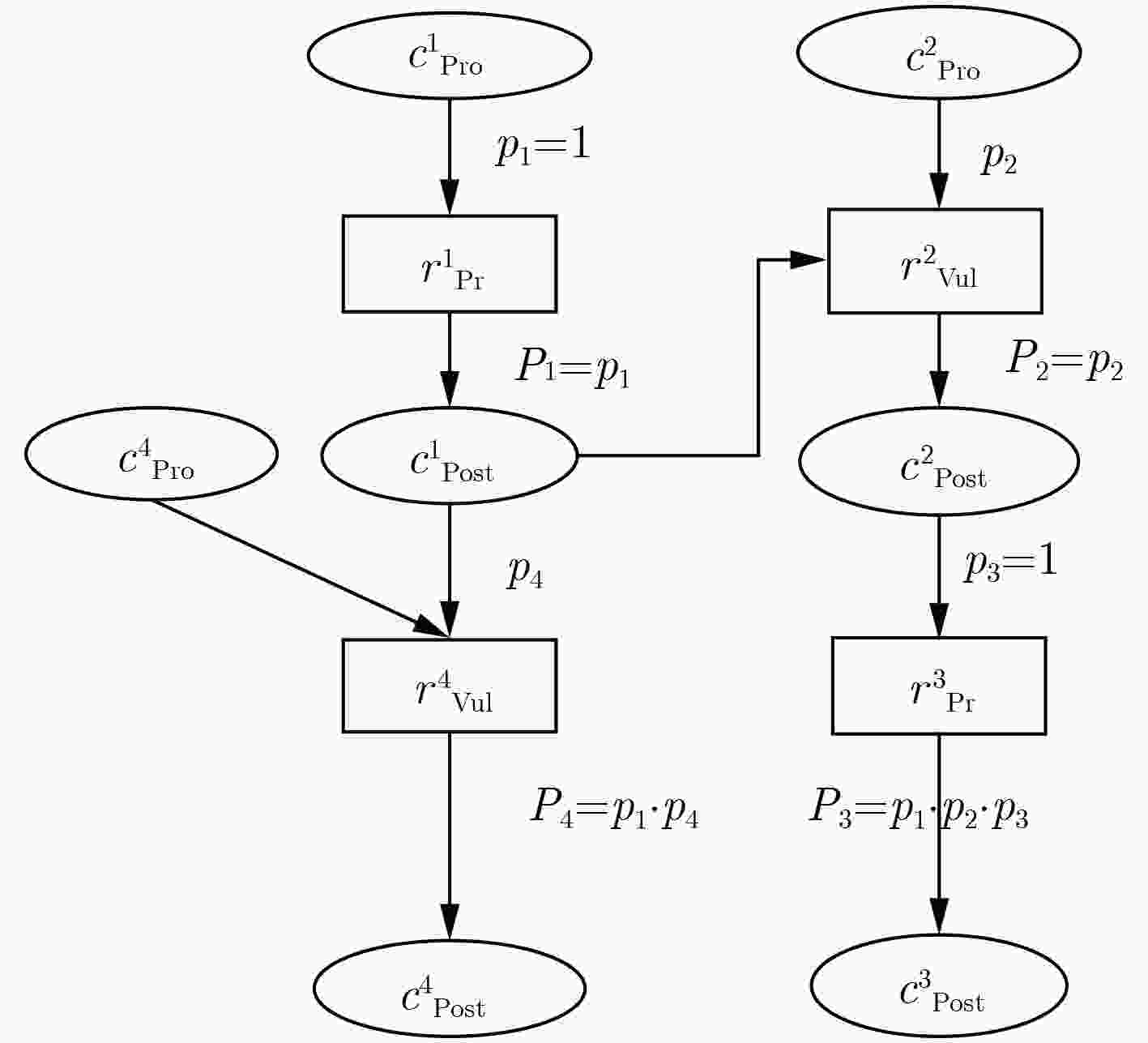
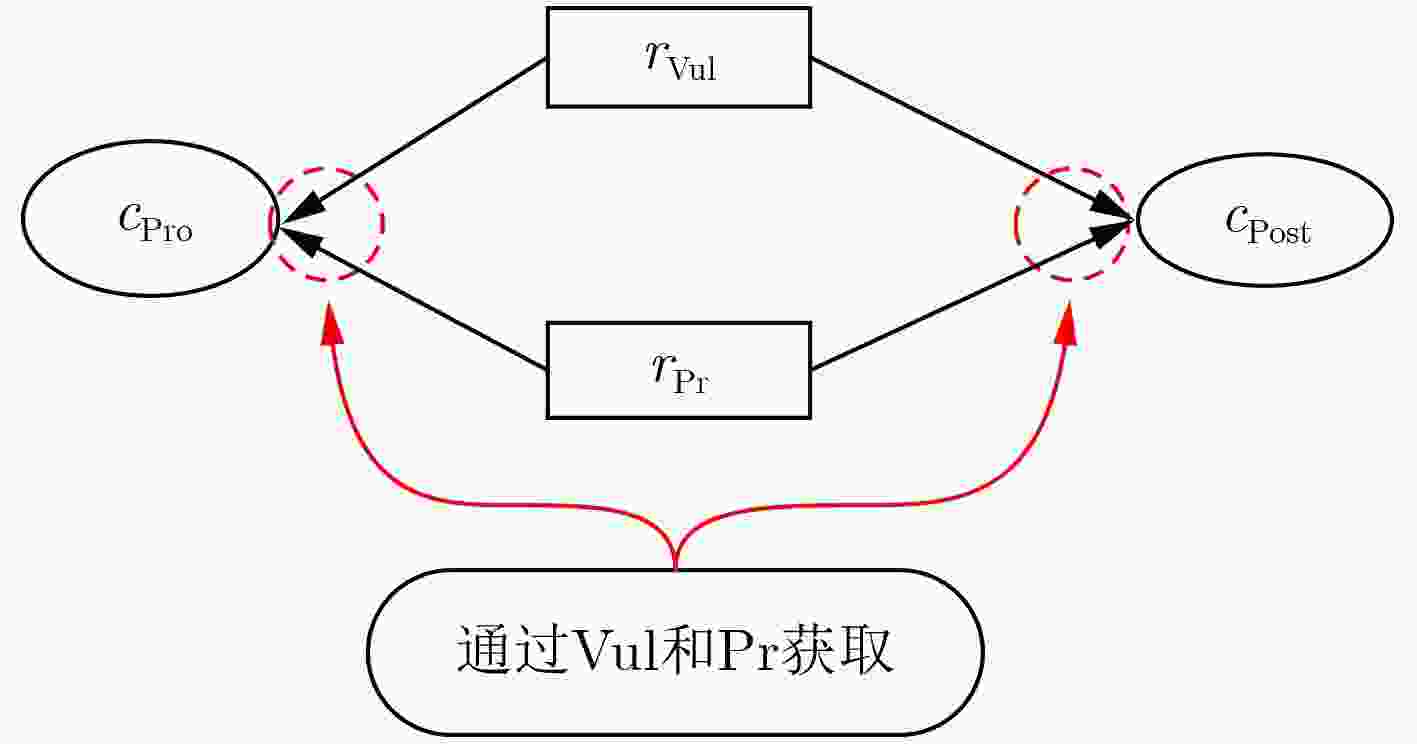
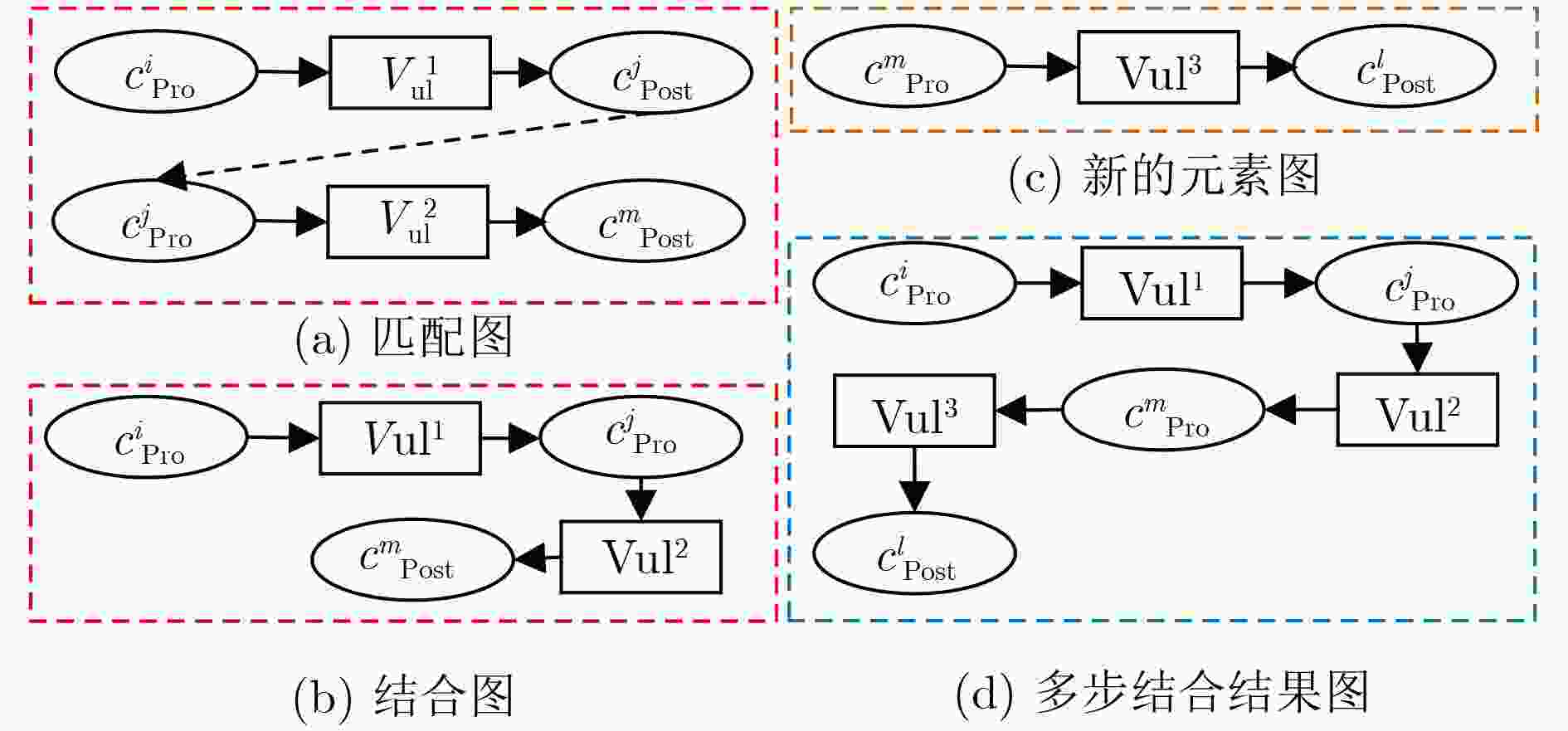


 下载:
下载:
