Hardware Security for Multi IPs Protection Based on Orthogonal Obfuscation
-
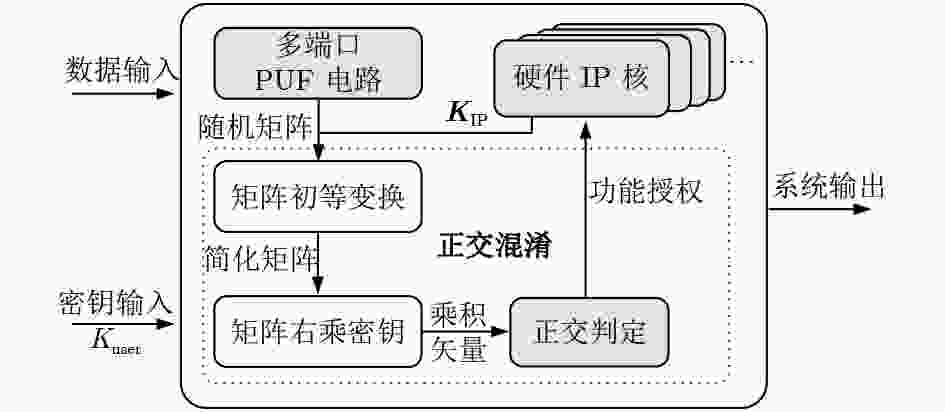
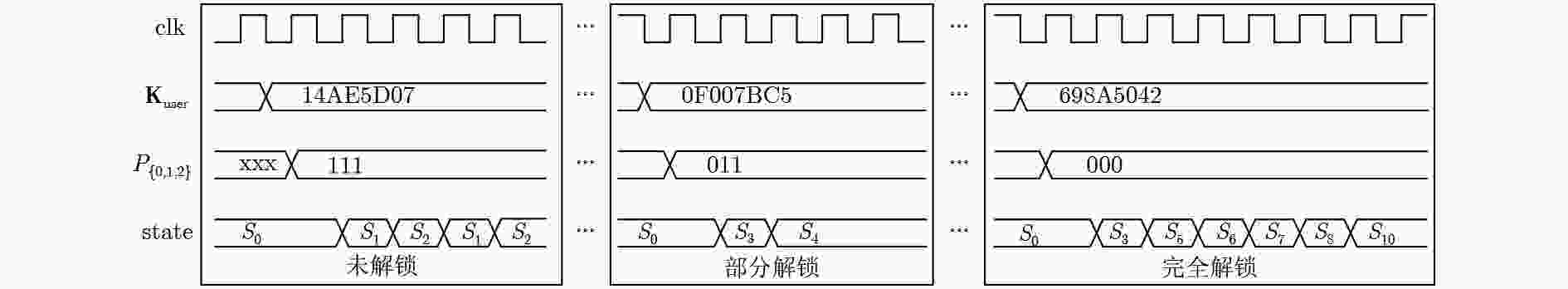
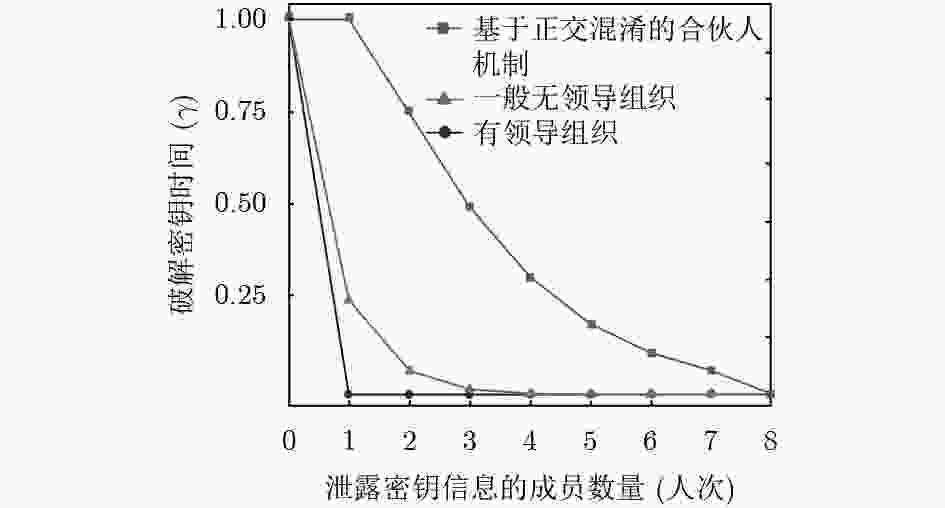
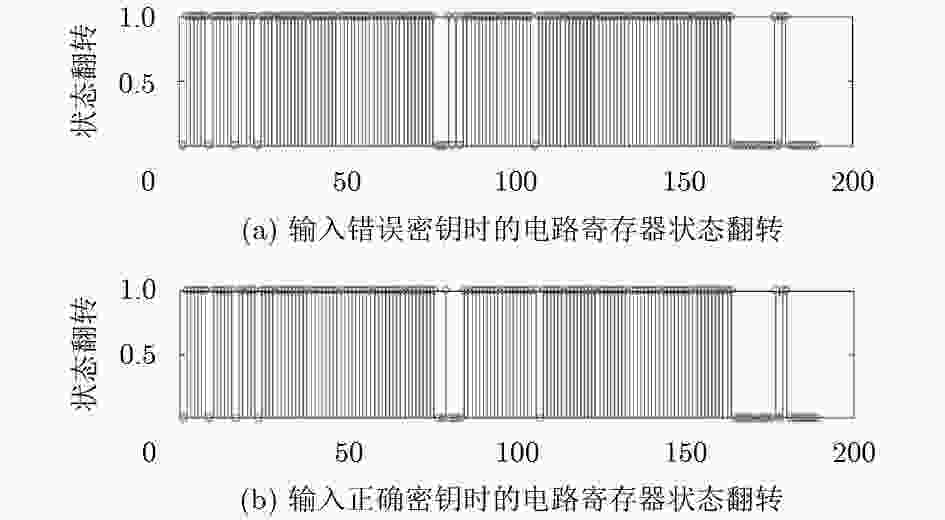
摘要: 为了解决集成电路设计中多方合作的成员信息泄漏问题,该文提出一种基于正交混淆的多硬件IP核安全防护方案。该方案首先利用正交混淆矩阵产生正交密钥数据,结合硬件特征的物理不可克隆函数(PUF)电路,产生多硬件IP核的混淆密钥;然后,在正交混淆状态机的基础上,实现多硬件IP核的正交混淆安全防护算法;最后,利用ISCAS-85基准电路和密码算法,验证正交混淆方法的有效性。在台湾积体电路制造股份有限公司(TSMC) 65 nm工艺下测试正交混淆的多硬件IP核方案,正确密钥和错误密钥下的Toggle翻转率小于5%,在较大规模的测试电路中面积和功耗开销占比小于2%。实验结果表明,采用正交混淆的方式能够提高多硬件IP核的安全性,可以有效防御成员信息泄漏、状态翻转率分析等攻击。Abstract: In order to solve the problem of member information leakage in multi-party cooperative design of integrated circuits, a orthogonal obfuscation scheme of multi-hardware IPs core security protection is proposed. Firstly, the orthogonal obfuscation matrix generates orthogonal key data, and the obfuscated key of the hardware IP core is designed with the physical feature of the Physical Unclonable Function (PUF) circuit. Then the security of multiple hardware IP cores is realized by the orthogonal obfuscation state machine. Finally, the validity of orthogonal aliasing is verified using the ISCAS-85 circuit and cryptographic algorithm. The multi-hardware IP core orthogonal obfuscation scheme is tested under Taiwan Semiconductor Manufacturing Company (TSMC) 65 nm process, the difference of Toggle flip rate between the correct key and the wrong key is less than 5%, and the area and power consumption of the larger test circuit are less than 2%. The experimental results show that orthogonal obfuscation can improve the security of multi-hardware IP cores, and can effectively defend against member information leakage and state flip rate analysis attacks.
-
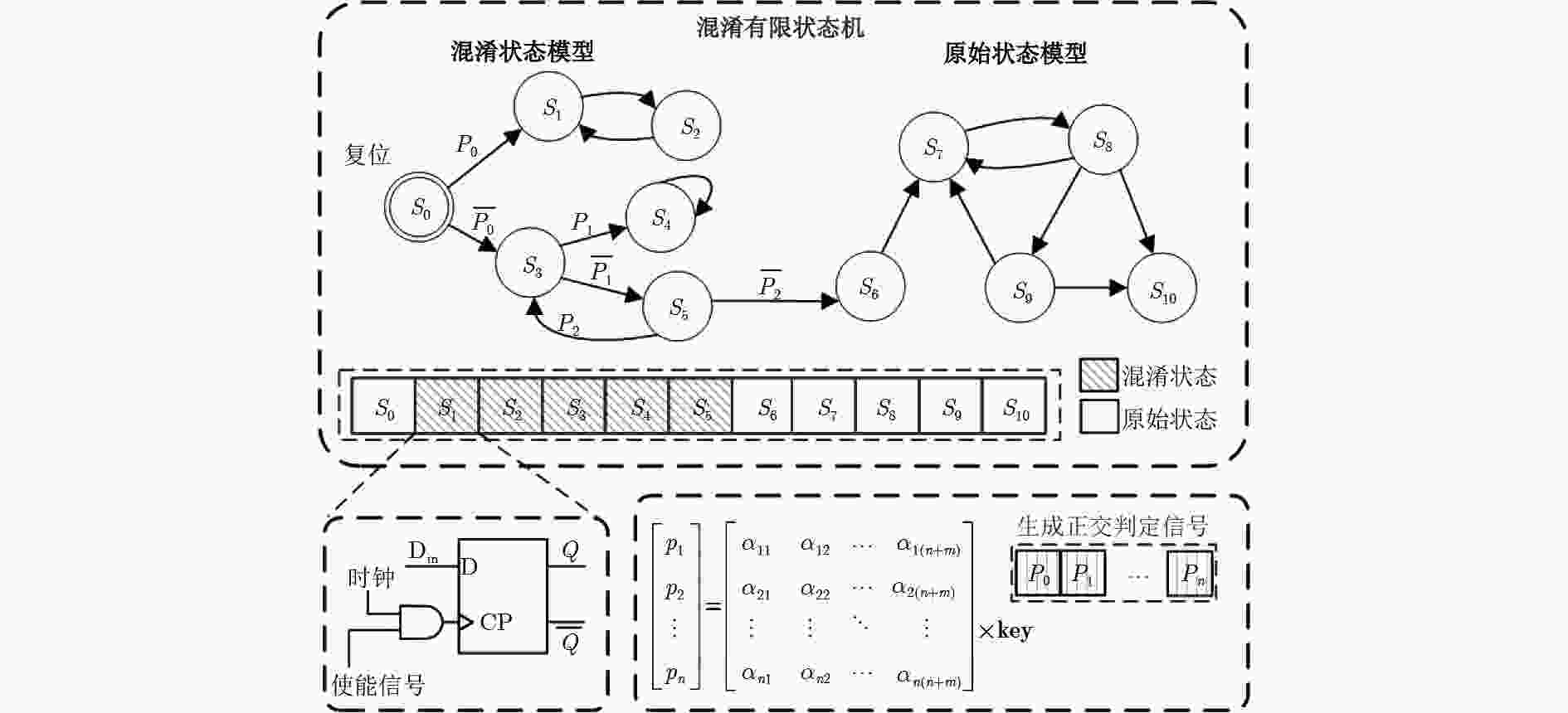
表 1 正交混淆算法伪代码
正交混淆算法 输入:Kuser 输出:{p1,p2,···,pn} (1) 初始化正交模块 (2) 重置功能IP核 (3) 对各功能IP核分配权重 (4) for i←0 to N-1 for j←i+1 to N-1 { do vector_j←vector_j-(vector_j[i]/vector_i[i])×
vector_i} (5) for i←0 to N-1 for j←i+1 to N-1 { do vector_i←vector_i-(vector_i[N-i]/vector_j[N-i])×
vector_j} (6) 矩阵O←{vector_1,vector_2,···,vector_N}T (7) 向量p←O×Kuser 表 2 基准电路中硬件开销情况
基准电路
面积(μm2)测试模块
面积(μm2)混淆面积
开销(μm2)面积开销
占比(%)基准电路
功耗(mW)测试模块
功耗(mW)混淆功耗
开销(mW)功耗开销
占比(%)混淆模块
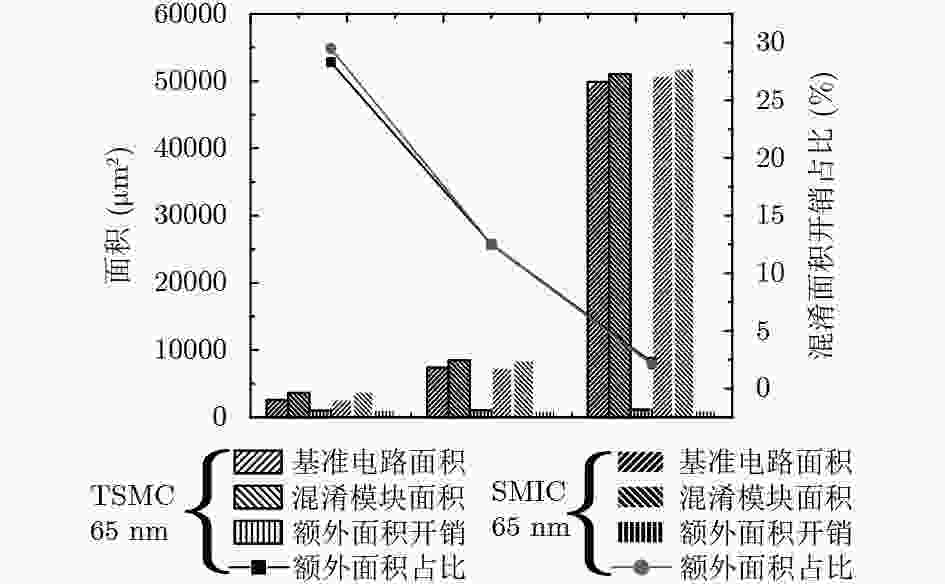
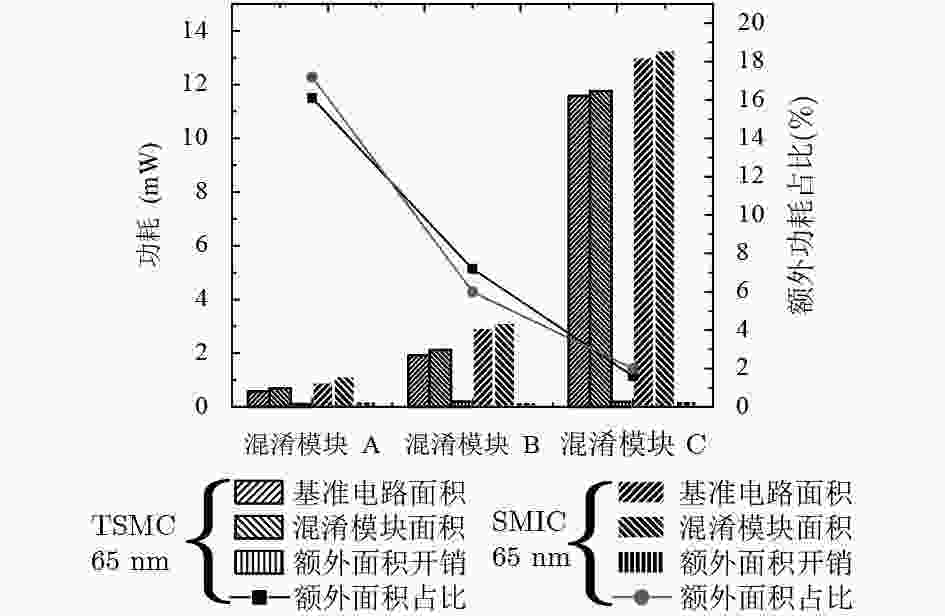
延时(ns)A1 6457.68 7391.68 934.00 12.60 0.3129 0.4392 0.1263 28.80 1.12 A1+A2 16851.96 17866.12 1014.16 5.70 3.3928 3.5517 0.1589 4.50 1.12 A1+A2+A3 32561.64 33618.80 1057.16 3.10 7.5221 7.7017 0.1796 2.30 1.15 A1+A2+A3+A4 49888.08 51038.76 1150.68 2.30 11.5796 11.7626 0.1830 1.60 1.20 注:表中A1, A2, A3和A4分别表示密码算法TDEA, SEED_3clk, MISTY1_3clk和AES中的EncCore部分。 文献 混淆方法 工艺(mm) 基准电路 面积(μm2) 功耗(mW) 速度(GHz) 混淆IP核数量 MILA 文献[8] 状态映射混淆 65 AES-ENC 25983.00 0.7558 – 单个 是 文献[9] DUP 65 SEED_3clk 17506.08 3.2171 1.38 单个 是 文献[10] ISO 65 SEED_3clk 17450.64 3.2830 1.72 单个 是 文献[11] HARPOON 65 S38584 22995.40 6.3883 1.14 单个 是 文献[12] Dynamic State-Deflection 65 S38584 21835.00 6.9262 0.86 单个 是 本文 正交混淆 65 SEED_3clk 17114.60 3.2815 0.98 多个 否 AES-ENC 17326.44 4.0575 0.95 否 s38584 20159.00 6.7456 0.83 否 -
FYRBIAK M, ROKICKI S, BISSANTZ N, et al. Hybrid obfuscation to protect against disclosure attacks on embedded microprocessors[J]. IEEE Transactions on Computers, 2018, 67(3): 307–321. doi: 10.1109/TC.2017.2649520 JAEHA K and PARK K T. EE6: Can artificial intelligence replace my job? The dawn of a new IC industry with AI[C]. 2018 IEEE International Solid-State Circuits Conference, San Francisco, USA, 2018: 531–533. WERNER M, UNTERLUGGAUER T, SCHAFFENRATH D, et al. Sponge-based control-flow protection for IoT devices[C]. 2018 IEEE European Symposium on Security and Privacy, London, UK, 2018: 214–226. 许天燊. 万物互联驱动IC产业创新与合作[J]. 软件和集成电路, 2015(6): 16–20.XU Tianshen. All things interconnection drives innovation and cooperation in IC industry[J]. Software and Integrated Circuits, 2015(6): 16–20. HONG C, KIM S H, KIM J H, et al. A linear-mode LiDAR sensor using a multi-channel CMOS transimpedance amplifier array[J]. IEEE Sensors Journal, 2018, 18(17): 7032–7040. doi: 10.1109/JSEN.2018.2852794 BUSE D S, SOMMER C, and DRESSLER F. Demo abstract: Integrating a driving simulator with city-scale VANET simulation for the development of next generation ADAS systems[C]. The IEEE INFOCOM 2018 - IEEE Conference on Computer Communications Workshops, Honolulu, USA, 2018: 1–2. VIJAYAKUMAR A, PATIL V C, HOLCOMB D E, et al. Physical design obfuscation of hardware: A comprehensive Investigation of device and logic-level techniques[J]. IEEE Transactions on Information Forensics and Security, 2017, 12(1): 64–77. doi: 10.1109/TIFS.2016.2601067 张跃军, 潘钊, 汪鹏君, 等. 基于状态映射的AES算法硬件混淆设计[J]. 电子与信息学报, 2018, 40(3): 750–757. doi: 10.11999/JEIT170556ZHANG Yuejun, PAN Zhao, WANG Pengjun, et al. Design of hardware obfuscation AES based on state deflection strategy[J]. Journal of Electronics &Information Technology, 2018, 40(3): 750–757. doi: 10.11999/JEIT170556 KOUSHANFAR F. Provably secure active IC metering techniques for piracy avoidance and digital rights management[J]. IEEE Transactions on Information Forensics and Security, 2012, 7(1): 51–63. doi: 10.1109/TIFS.2011.2163307 CHAKRABORTY R S and BHUNIA S. RTL hardware IP protection using key-based control and data flow obfuscation[C]. International Conference on VLSI Design, Bangalore, India, 2010: 405–410. CHAKRABORTY R S and BHUNIA S. HARPOON: An obfuscation-based soc design methodology for hardware protection[J]. IEEE Transactions on Computer-Aided Design of Integrated Circuits and Systems, 2009, 28(10): 1493–1502. doi: 10.1109/TCAD.2009.2028166 DOFE J and YU Qiaoyan. Novel dynamic state-deflection method for gate-level design obfuscation[J]. IEEE Transactions on Computer-Aided Design of Integrated Circuits and Systems, 2018, 37(2): 273–285. doi: 10.1109/TCAD.2017.2697960 CANETTI R, ROTHBLUM G N, and VARIA M. Theory of Cryptography[M]. Berlin, Heidelberg: Springer, 2010: 72–89. CAO Yuan, ZHANG Le, CHANG C H, et al. A low-power hybrid RO PUF with improved thermal stability for lightweight applications[J]. IEEE Transactions on Computer-Aided Design of Integrated Circuits and Systems, 2015, 34(7): 1143–1147. doi: 10.1109/TCAD.2015.2424955 ZHANG Jiliang, LIN Yaping, LYU Yongqiang, et al. A PUF-FSM binding scheme for FPGA IP protection and pay-per-device licensing[J]. IEEE Transactions on Information Forensics and Security, 2015, 10(6): 1137–1150. doi: 10.1109/TIFS.2015.2400413 张元达. 有限群构造[M]. 北京: 科学出版社, 1982: 203–206.ZHANG Yuanda. Finite Group Construction[M]. Beijing: Science Press, 1982: 203–206. LAO Yingjie and PARHI K K. Statistical analysis of MUX-based physical unclonable functions[J]. IEEE Transactions on Computer-Aided Design of Integrated Circuits and Systems, 2014, 33(5): 649–662. doi: 10.1109/TCAD.2013.2296525 BOŠNJAK L, SREŠ J, and BRUMEN B. Brute-force and dictionary attack on hashed real-world passwords[C]. The 41st International Convention on Information and Communication Technology, Electronics and Microelectronics, Opatija, Croatia, 2018: 1161–1166. -





 下载:
下载:



 下载:
下载:
