Partial Blind Signcryption Scheme in CLPKC-to-TPKI Heterogeneous Environment
-
摘要: 该文提出在无证书公钥密码体制(CLPKC)和传统公共密钥基础设施体制(TPKI)下部分盲签密方案的形式化定义,并在此基础上提出一个在CLPKC-TPKI环境下具有双线性对的部分盲签密方案。依据随机预言模型,计算Diffie-Hellman困难问题(CDHP)和修改逆计算Diffie-Hellman困难问题(MICDHP)假设,使得方案在异构环境下满足不可伪造性、机密性、部分盲性、不可跟踪性、不可否认性等性质。最后和相关方案进行了比较分析,该文方案在增加了盲性同时并未显著增加计算量的开销。
-
关键词:
- 异构签密 /
- 部分盲签密 /
- 修改逆计算Diffie-Hellman困难问题
Abstract: The definition and security models of partial blind signcryption scheme in heterogeneous environment between CertificateLess Public Key Cryptography (CLPKC)and Traditional Public Key Infrastructure (TPKI) are proposed, and a construction by using the bilinear pairing is proposed. Under the random oracle model, based on the assumptions of Computational Diffie-Hellman Problem(CDHP) and Modifying Inverse Computational Diffie-Hellman(MICDHP), the scheme is proved to meet the requirment of the unforgeability, confidentiality, partial blindness, and untraceability, undeniability. Finally, compared with the related scheme, the scheme increases the blindness and does not significantly increase the computational cost. -
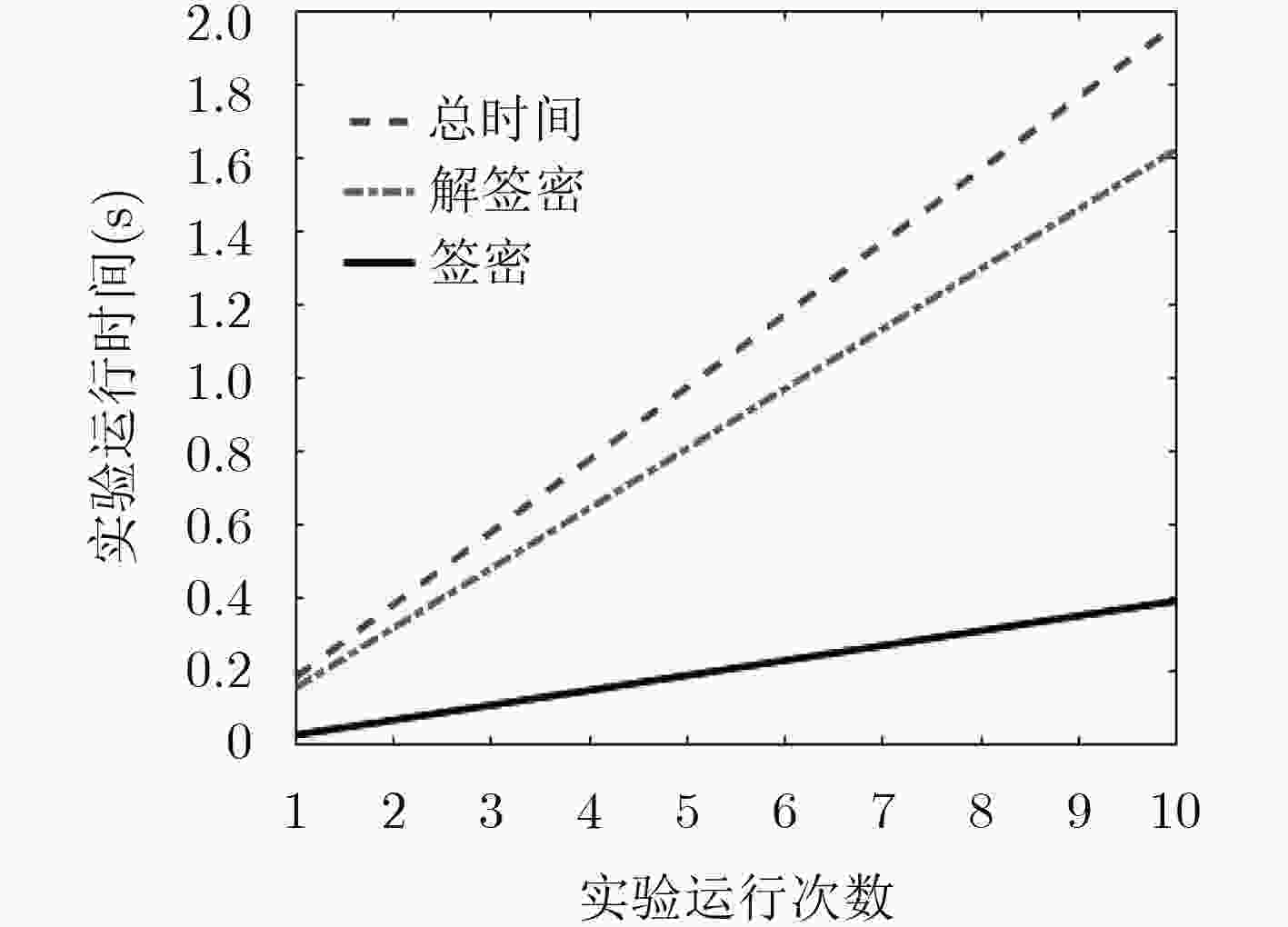
表 1 计算复杂度
方案 签密 解签密 系统参数 盲性 文献[15] 2E+P E+3P 不同 满足 本文 0E+0P 0E+2P 不同 满足 -
HU Xiaoming, LIU Yan, XU Huajie, et al. Analysis and improvement of certificateless signature and proxy re-signature schemes[C]. 2015 IEEE Advanced Information Technology, Electronic and Automation Control Conference, Chongqing, China, 2015: 166–170. doi: 10.1109/IAEAC.2015.7428540. JIANG M M, HU Y P, WANG B C, et al. Lattice‐based multi‐use unidirectional proxy re‐encryption[J]. Security and Communication Networks, 2015, 8(18): 3796–3803. doi: 10.1002/sec.1300 邓宇乔, 杜明辉, 尤再来, 等. 一种基于标准模型的盲代理重签名方案[J]. 电子与信息学报, 2010, 32(5): 1219–1223. doi: 10.3724/SP.J.1146.2009.00754DENG Yuqiao, DU Minghui, YOU Zailai, et al. A blind proxy re-signatures scheme based on standard model[J]. Journal of Electronics &Information Technology, 2010, 32(5): 1219–1223. doi: 10.3724/SP.J.1146.2009.00754 刘哲, 刘建伟, 伍前红, 等. 车载网络中安全有效分布式的假名生成[J]. 通信学报, 2015, 36(11): 33–40. doi: 10.11959/j.issn.1000-436x.2015253LIU Zhe, LIU Jianwei, WU Qianhong, et al. Secure and efficient distributed pseudonym generation in VANET[J]. Journal on Communications, 2015, 36(11): 33–40. doi: 10.11959/j.issn.1000-436x.2015253 李建民, 俞惠芳, 赵晨. UC安全的自认证盲签密协议[J]. 计算机科学与探索, 2017, 11(6): 932–940. doi: 10.3778/j.issn.1673-9418.1605047LI Jianmin, YU Huifang, and ZHAO Chen. Self-certified blind signcryption protocol with UC security[J]. Journal of Frontiers of Computer Science and Technology, 2017, 11(6): 932–940. doi: 10.3778/j.issn.1673-9418.1605047 傅晓彤, 陈思, 张宁. 基于代理的密码货币支付系统[J]. 通信学报, 2017, 38(7): 199–206. doi: 10.11959/j.issn.1000-436x.2017121FU Xiaotong, CHEN Si, and ZHANG Ning. Proxy-cryptocurrency payment system[J]. Journal on Communications, 2017, 38(7): 199–206. doi: 10.11959/j.issn.1000-436x.2017121 SUN Yinxia and LI Hui. Efficient signcryption between TPKC and IDPKC and its multi-receiver construction[J]. Science China Information Sciences, 2010, 53(3): 557–566. doi: 10.1007/s11432-010-0061-5 HUANG Qiang, WONG D S, and YANG Guomin. Heterogeneous signcryption with key privacy[J]. The Computer Journal, 2011, 54(4): 525–536. doi: 10.1093/comjnl/bxq095 张玉磊, 张灵刚, 张永洁, 等. 匿名CLPKC-TPKI异构签密方案[J]. 电子学报, 2016, 44(10): 2432–2439. doi: 10.3969/j.issn.0372-2112.2016.10.022ZHANG Yulei, ZHANG Linggang, ZHANG Yongjie, et al. CLPKC-to-TPKI heterogeneous signcryption scheme with anonymity[J]. Acta Electronica Sinica, 2016, 44(10): 2432–2439. doi: 10.3969/j.issn.0372-2112.2016.10.022 冯涛, 彭伟, 马建峰. 安全的无可信PKG的部分盲签名方案[J]. 通信学报, 2010, 31(1): 128–134. doi: 10.3969/j.issn.1000-436X.2010.01.020FENG Tao, PENG Wei, and MA Jianfeng. Provably secure partially blind signature without trusted PKG[J]. Journal on Communications, 2010, 31(1): 128–134. doi: 10.3969/j.issn.1000-436X.2010.01.020 杨小东, 陈春霖, 杨平, 等. 可证安全的部分盲代理重签名方案[J]. 通信学报, 2018, 39(2): 65–72. doi: 10.11959/j.issn.1000-436x.2018014YAGN Xiaodong, CHEN Chunlin, YANG Ping, et al. Partially blind proxy re-signature scheme with proven security[J]. Journal on Communications, 2018, 39(2): 65–72. doi: 10.11959/j.issn.1000-436x.2018014 BARBOSA M and FARSHIM P. Certificateless signcryption[C]. 2008 ACM Symposium on Information, Computer and Communications Security, Tokyo, Japan, 2008: 369–372. 彭巧, 田有亮. 基于多线性Diffie-Hellman问题的秘密共享方案[J]. 电子学报, 2017, 45(1): 200–205. doi: 10.3969/j.issn.0372-2112.2017.01.027PENG Qiao and TIAN Youliang. A secret sharing scheme based on multilinear Diffie-Hellman problem[J]. Acta Electronica Sinica, 2017, 45(1): 200–205. doi: 10.3969/j.issn.0372-2112.2017.01.027 POINTCHEVAL D and STERN J. Security arguments for digital signatures and blind signatures[J]. Journal of Cryptology, 2000, 13(3): 361–396. doi: 10.1007/s001450010003 牛淑芬, 杨喜艳, 王彩芬, 等. 基于异构密码系统的混合盲签密方案[J]. 计算机工程, 2018, 44(8): 151–154, 160. doi: 10.19678/j.issn.1000-3428.0047898NIU Shufen, YANG Xiyan, WANG Caifen, et al. Hybrid blind signcryption scheme based on heterogeneous cryptosystem[J]. Computer Engineering, 2018, 44(8): 151–154, 160. doi: 10.19678/j.issn.1000-3428.0047898 -





 下载:
下载:


 下载:
下载:
