Heterogeneity Quantization Method of Cyberspace Security System Based on Dissimilar Redundancy Structure
-
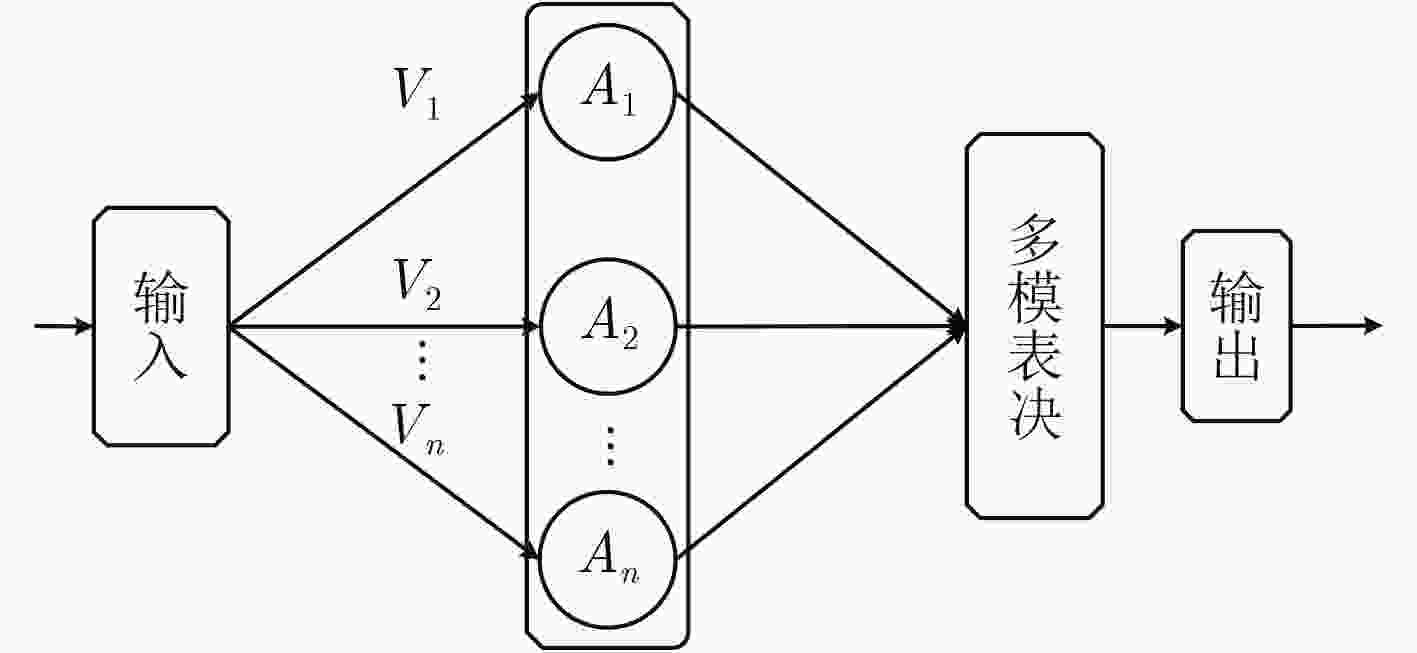
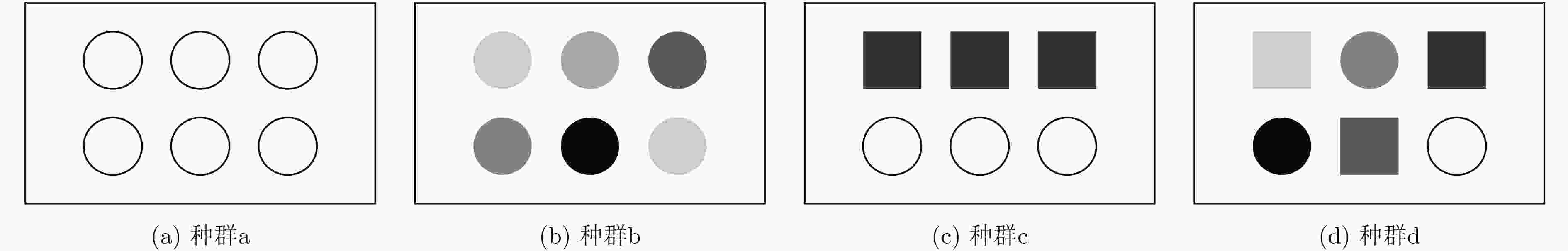
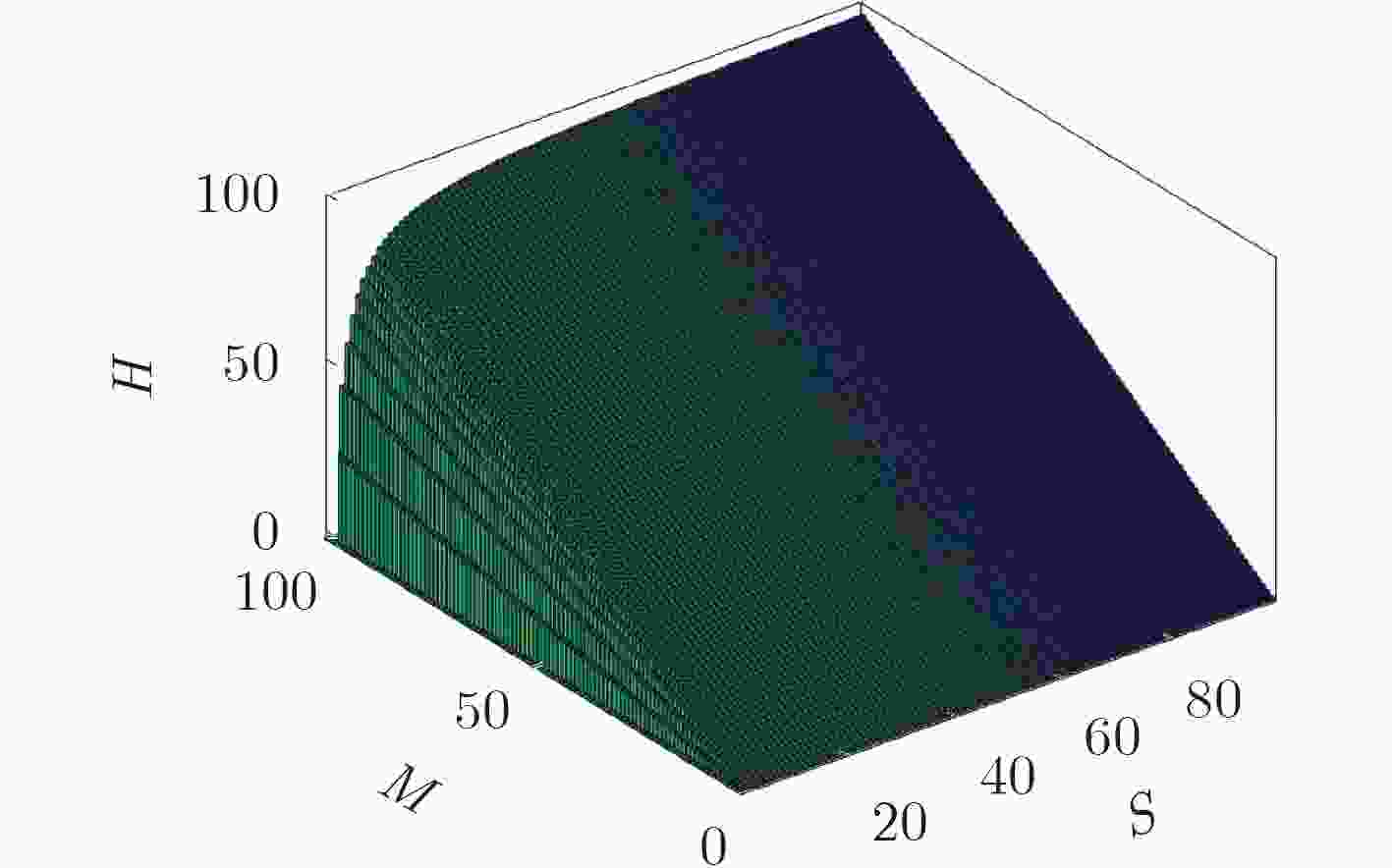
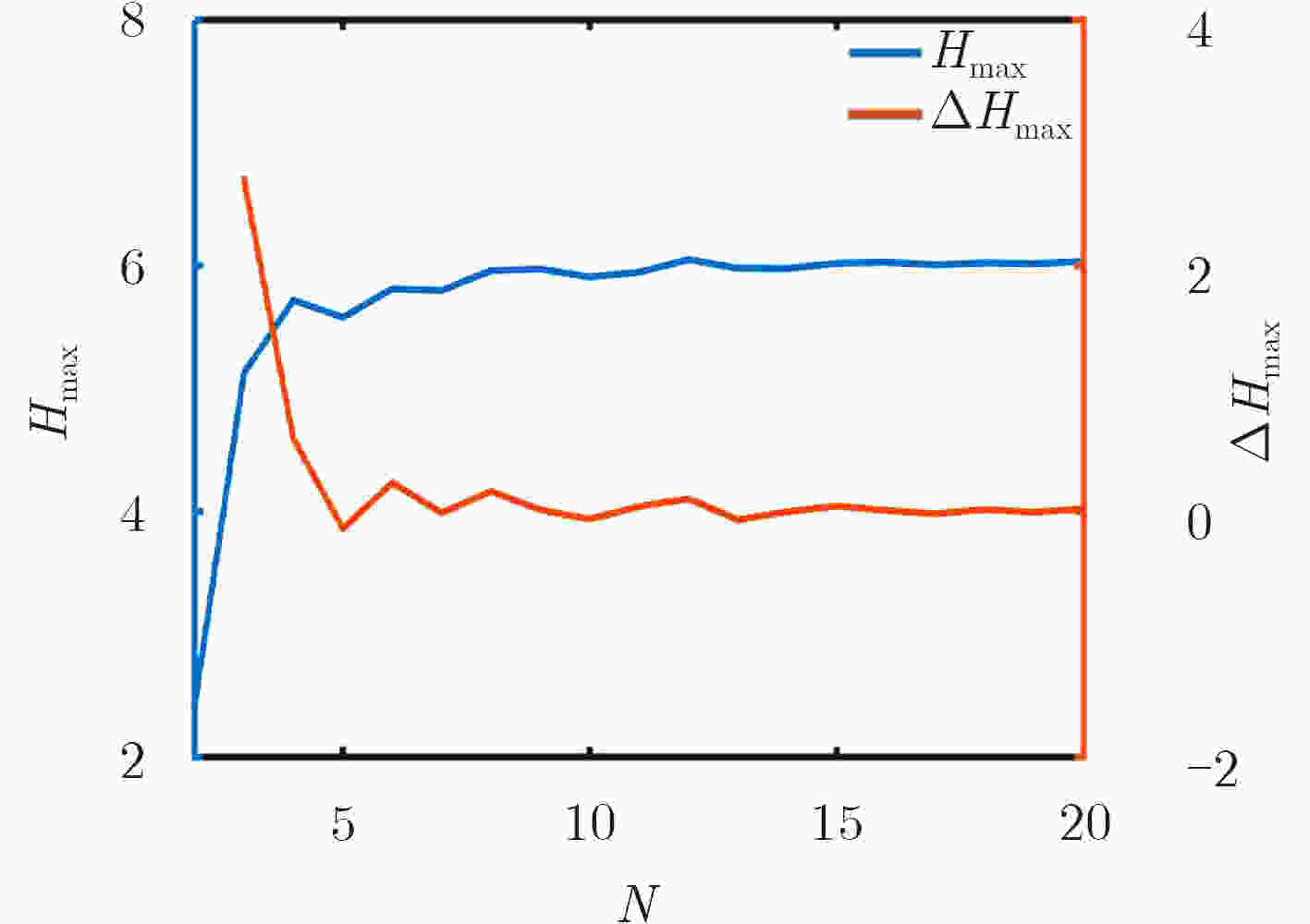
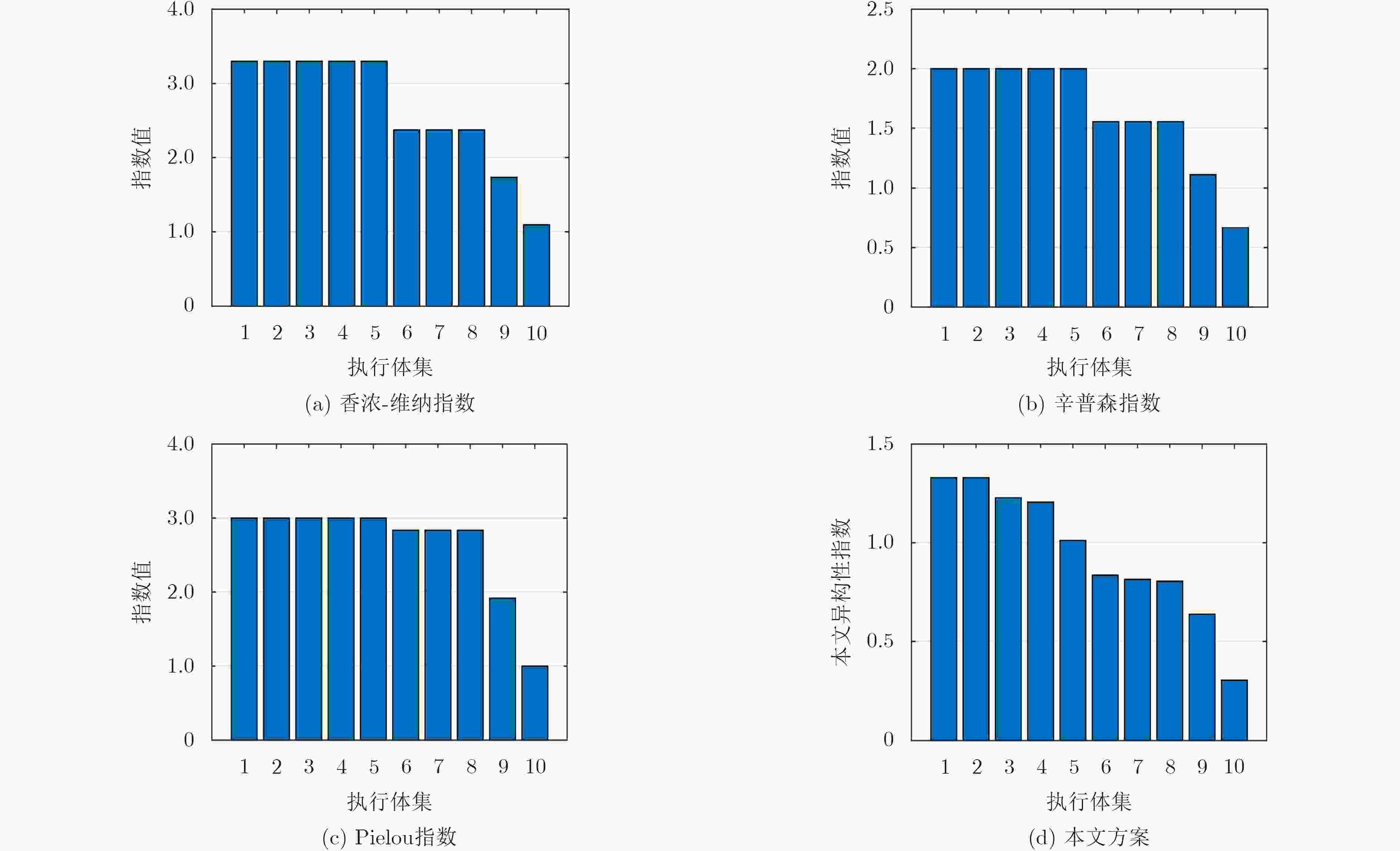
摘要: 基于非相似余度架构(DRS)的网络空间安全技术是一种主动防御技术,其利用非相似性、冗余性等特性阻断或者扰乱网络攻击,以提高系统的可靠性和安全性。该文在研究异构性是如何提高系统的安全性的基础上,指出对异构性进行量化评估的重要性,将DRS的异构性定义为其执行体集的复杂性与差异性,并依此提出一种量化异构性的方法。实验结果表明,该方法可以将10个执行体集分为9类,而香浓-维纳指数、辛普森指数和Pielou指数只能分为4类。在理论上为DRS异构性量化评估提供了一种新方法,并为工程实现DRS系统提供了指导。Abstract: The Dissimilar Redundancy Structure (DRS) based cyberspace security technology is an active defense technology, which uses features such as dissimilarity and redundancy to block or disrupt network attacks to improve system reliability and security. By analyzing how heterogeneity can improve the security of the system, the importance of quantification of heterogeneity is pointed out and the heterogeneity of DRS is defined as the complexity and disparity of its execution set. A new method which is suitable for quantitative heterogeneity is also proposed. The experimental results show that this method can divide 10 execution sets into 9 categories, while the Shannon-Wiener index, Simpson index and Pielou index can only divide into 4 categories. This paper provides a new method to quantify the heterogeneity of DRS in theory, and provides guidance for engineering DRS systems.
-
Key words:
- Cyberspace security /
- Vulnerability /
- Dissimilar redundancy /
- Heterogeneity /
- Quantification method
-
表 1 执行体集表
编号 软件栈 编号 软件栈 1 Ubuntu 12.04+Apache 2.4.0+Mysql 5.7.18 6 Ubuntu 12.04+Apache 2.4.0+Mysql 5.7.18 Windows Server 2003+IIS 6.0+SQL Server 2012 SP2 Windows Server 2008+Apache 2.4.0+Oracle 11.2.0.3 RedHat 7+Nginx 1.12.0+Oracle 11.2.0.3 RedHat 7+Nginx 1.12.0+Mysql 5.7.18 2 Ubuntu 12.04+Apache 2.4.0+Oracle 11.2.0.3 7 Ubuntu 12.04+Apache 2.4.0+Mysql 5.7.18 Windows Server 2012+IIS 7.0+SQL Server 2012 SP2 Debian 7.0+Apache 2.4.0+Mysql 5.7.18 RedHat 7+Nginx 1.12.0+Mysql 5.7.18 RedHat 7+Nginx 1.12.0+Oracle 11.2.0.3 3 Debian 7.0+Nginx 1.12.0+Mysql 5.7.18 8 Ubuntu 12.04+Nginx 1.12.0+Mysql 5.7.18 Windows Server 2016+Lighttpd 1.4.48+SQL Server 2016 Windows Server 2016+Lighttpd 1.4.48+SQL Server 2016 Windows 7+Apache 2.4.0+SQL Server 2014 SP2 Windows 7+Nginx 1.12.0+Mysql 5.7.18 4 Ubuntu 12.04+Nginx 1.12.0+Mysql 5.7.18 9 Ubuntu 12.04+Apache 2.4.0+Oracle 11.2.0.3 Windows Server 2003+IIS 6.0+SQL Server 2016 Windows Server 2008+Apache 2.4.0+SQL Server 2012 SP2 Windows 7+Apache 2.4.0+SQL Server 2014 SP2 RedHat 7+Apache 2.4.0+Oracle 11.2.0.3 5 Windows Server 2003+IIS 6.0+SQL Server 2012 SP2 10 Ubuntu 12.04+Apache 2.4.0+Mysql 5.7.18 Windows Server 2012+IIS 7.0+SQL Server 2016 Windows Server 2008+Apache 2.4.0+Mysql 5.7.18 Windows 7+Nginx 1.12.0+SQL Server 2014 SP2 Windows 7+Apache 2.4.0+Mysql 5.7.18 表 2 差异性参数表
构件1 构件2 d 构件1 构件2 d Ubuntu 12.04 RedHat 7 0.9868 Windows Server 2012 Windows 7 0.5391 Windows Server 2003 Windows 7 0.7842 Windows Server 2008 Windows 7 0.2246 Windows Server 2016 Windows 7 0.8782 IIS 6.0 IIS 7.0 0.7686 Ubuntu 12.04 Debian 7.0 0.9341 SQL Server 2012 SP2 SQL Server 2014 SP2 0.9331 RedHat 7 Debian 7.0 0.9930 SQL Server 2014 SP2 SQL Server 2016 0.7206 Windows Server 2003 Windows Server 2012 0.9707 -
中国互联网络信息中心. 第42次《中国互联网络发展状况统计报告》[OL]. http://www.cnnic.net.cn/hlwfzyj/hlwxzbg/hlwtjbg/201808/t20180820_70488.htm, 2018.China Internet Network Information Center. The 42nd "China Internet network development state statistic report"[OL]. http://www.cnnic.net.cn/hlwfzyj/hlwxzbg/hlwtjbg/201808/t20180820_70488.htm, 2018. SUBRAHMANIAN V S, OVELGONNE M, DUMITRAS T, et al. The Global Cyber-vulnerability Report[M]. Cham, Switzerland: Springer International Publishing, 2015. doi: 10.1007/978-3-319-25760-0. ERIC T, MAJORCZYK F, and MÉ L. COTS diversity based intrusion detection and application to web servers[C]. The 8th International Symposium on Recent Advances in Intrusion Detection, Washington, USA, 2005: 43–62. doi: https://doi.org/10.1007/11663812_3. GASHI I and POPOV P. Rephrasing rules for off-the-shelf SQL database servers[C]. European Dependable Computing Conference, Coimbra, Portugal, 2006: 139–148. doi: 10.1109/EDCC.2006.20. OKHRAVI H, HOBSON T, BIGELOW D, et al. Finding focus in the blur of moving-target techniques[J]. IEEE Security & Privacy, 2014, 12(2): 16–26. doi: 10.1109/MSP.2013.137 邬江兴. 网络空间拟态防御导论[M]. 北京:科学出版社, 2017: 341–399.WU Jiangxing. Introduction to Cyberspace Mimic Defense[M]. Beijing: Science Press, 2017: 341–399. 殷斌, 陆熊, 陶想林. 非相似三余度飞控计算机设计和可靠性分析[J]. 测控技术, 2015, 34(5): 53–56. doi: 10.19708/j.ckjs.2015.05.015YIN Bin, LU Xiong, and TAO Xianglin. Design of a prototype flight control computer system with triple dissimilar redundancy[J]. Measurement &Control Technology, 2015, 34(5): 53–56. doi: 10.19708/j.ckjs.2015.05.015 WANG Shaoping, CUI Xiaoyu, SHI Jian, et al. Modeling of reliability and performance assessment of a dissimilar redundancy actuation system with failure monitoring[J]. Chinese Journal of Aeronautics, 2016, 29(3): 799–813. doi: 10.1016/j.cja.2015.10.002 仝青, 张铮, 张为华, 等. 拟态防御Web服务器设计与实现[J]. 软件学报, 2017, 28(4): 883–897. doi: 10.13328/j.cnki.jos.005192TONG Qing, ZHANG Zheng, ZHANG Weihua, et al. Design and implementation of mimic defense Web server[J]. Journal of Software, 2017, 28(4): 883–897. doi: 10.13328/j.cnki.jos.005192 GHORABAEE M K, AMIRI M, and AZIMI P. Genetic algorithm for solving bi-objective redundancy allocation problem with k-out-of-n subsystems[J]. Applied Mathematical Modelling, 2015, 39(20): 6396–6409. doi: 10.1016/j.apm.2015.01.070 AMIRI M and KHAJEH M. Developing a bi-objective optimization model for solving the availability allocation problem in repairable series-parallel systems by NSGA II[J]. Journal of Industrial Engineering International, 2016, 12(1): 61–69. doi: 10.1007/s40092-015-0128-4 韩进, 臧斌宇. 软件相异性对于系统安全的有效性分析[J]. 计算机应用与软件, 2010, 27(9): 273–275. doi: 10.3969/j.issn.1000-386X.2010.09.086HAN Jin and ZANG Binyu. Analyzing the effectiveness of software diversity for system security[J]. Computer Applicationsand Software, 2010, 27(9): 273–275. doi: 10.3969/j.issn.1000-386X.2010.09.086 TWU P, MOSTOFI Y, and EGERSTEDT M. A measure of heterogeneity in multi-agent systems[C]. IEEE American Control Conference, Portland, USA, 2014: 3972–3977. doi: 10.1109/ACC.2014.6858632. RAO C R. Diversity and dissimilarity coefficients: A unified approach[J]. Theoretical Population Biology, 1982, 21(1): 24–43. doi: 10.1016/0040-5809(82)90004-1 DING Ning, YANG Weifang, ZHOU Yunlei, et al. Different responses of functional traits and diversity of stream macroinvertebrates to environmental and spatial factors in the Xishuangbanna watershed of the upper Mekong River Basin, China[J]. Science of the Total Environment, 2017, 574(52): 288–299. doi: 10.1016/j.scitotenv.2016.09.053 LIU Zhijun. Bootstrapping one way analysis of rao's quadratic entropy[J]. Communication in Statistics-Theory and Methods, 2007, 20(20): 1683–1703. doi: 10.1080/03610929108830592 BOTTA-DUKáT Z. Rao's quadratic entropy as a measure of functional diversity based on multiple traits[J]. Journal of Vegetation Science, 2010, 16(5): 533–540. doi: 10.1111/j.1654-1103.2005.tb02393.x YOUNIS A, MALAIYA Y K, and RAY I. Evaluating CVSS base score using vulnerability rewards programs[C]. Proceedings of IFIP International Information Security and Privacy Protection, Ghent, Belgium, 2016: 62–75. doi: https://doi.org/10.1007/978-3-319-33630-5_5. CHEN L and AVIZIENIS A. N-version programming: A fault-tolerance approach to reliability of software operation[C]. Eighth International Conference on Fault Tolerant Computing, Toulouse, France, 1978: 3–9. 仝青, 张铮, 邬江兴. 基于软硬件多样性的主动防御技术[J]. 信息安全学报, 2017, 2(1): 1–12. doi: 10.19363/j.cnki.cn10-1380/tn.2017.01.001TONG Qing, ZHANG Zheng, and WU Jiangxing. The active defense technology based on the software/hardware diversity[J]. Journal of Cyber Security, 2017, 2(1): 1–12. doi: 10.19363/j.cnki.cn10-1380/tn.2017.01.001 -





 下载:
下载:


 下载:
下载:
