Related-key Impossible Differential Cryptanalysis on Lightweight Block Cipher ESF
-
摘要:
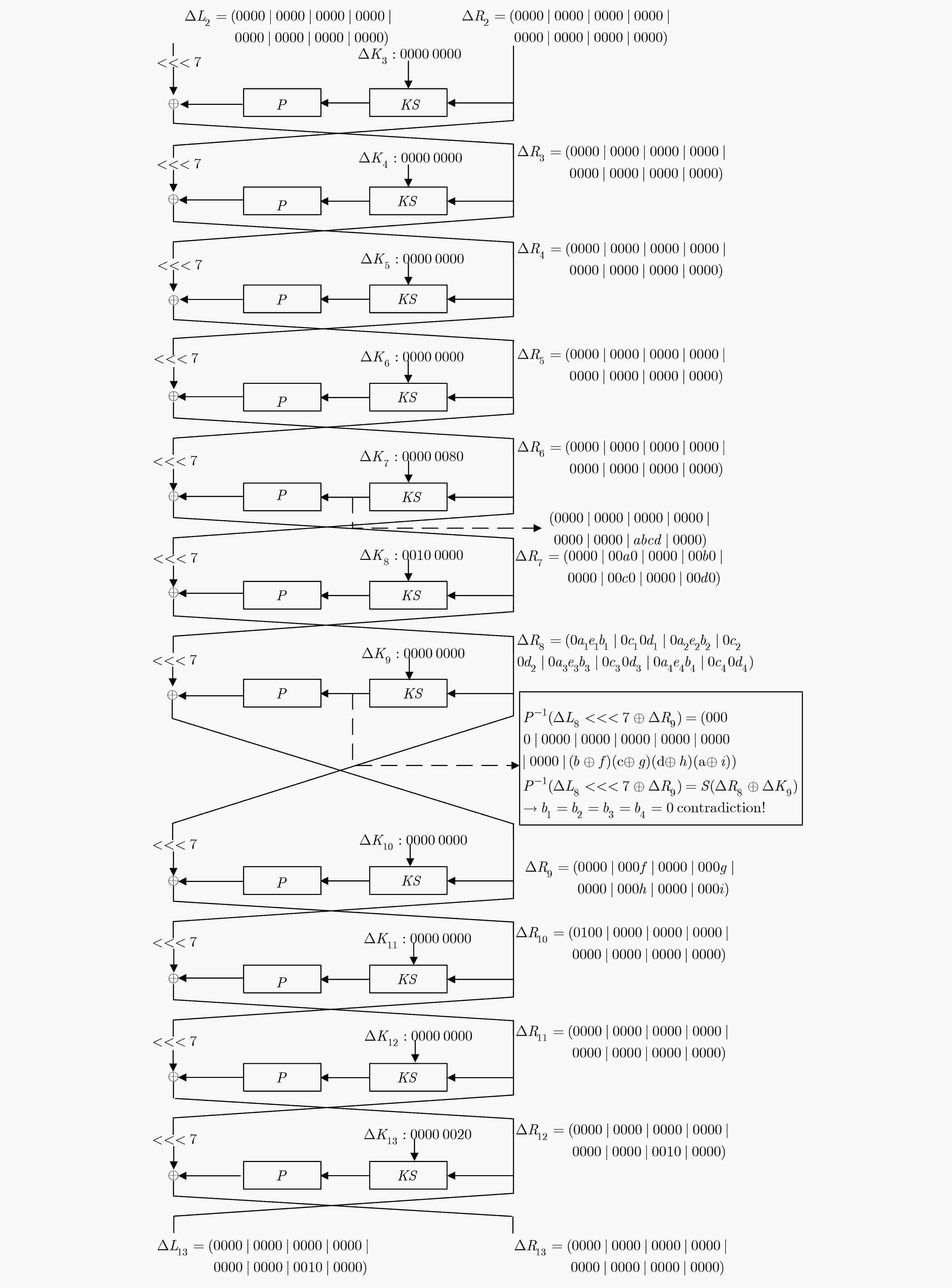
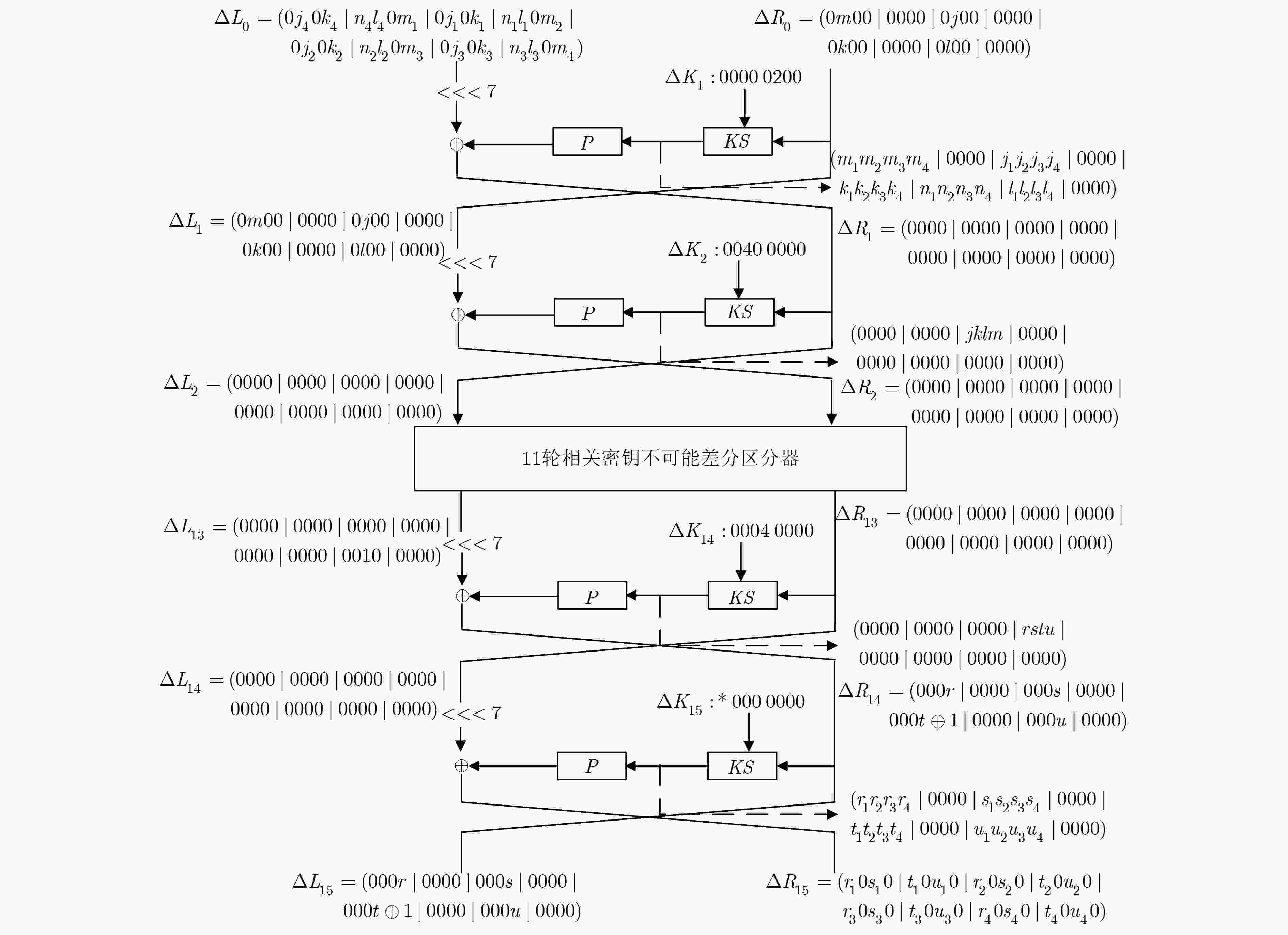
八阵图算法(ESF)是一种具有广义Feistel结构的轻量级分组密码算法,可用在物联网环境下保护射频识别(RFID)标签等资源受限的环境中,目前对该算法的安全性研究主要为不可能差分分析。该文通过深入研究S盒的特点并结合ESF密钥扩展算法的性质,研究了ESF抵抗相关密钥不可能差分攻击的能力。通过构造11轮相关密钥不可能差分区分器,在此基础上前后各扩展2轮,成功攻击15轮ESF算法。该攻击的时间复杂度为240.5次15轮加密,数据复杂度为261.5个选择明文,恢复密钥比特数为40 bit。与现有结果相比,攻击轮数提高的情况下,时间复杂度降低,数据复杂度也较为理想。
Abstract:Eight-Sided Fortress (ESF) is a lightweight block cipher with a generalized Feistel structure, which can be used in resource-constrained environments such as protecting Radio Frequency IDentification (RFID) tags in the internet of things. At present, the research on the security of ESF mainly adopts the impossible differential cryptanalysis. The ability of ESF to resist the related-key impossible differential cryptanalysis is studied based on the characteristics of its S-boxes and key schedule. By constructing an 11-round related-key impossible differential distinguisher, an attack on 15-round ESF is proposed by adding 2-round at the top and 2-round at the bottom. This attack has a time complexity of 240.5 15-round encryptions and a data complexity of 261.5 chosen plaintexts with 40 recovered key-bit. Compared with published results, the time complexity is decreased and the data complexity is ideal with the number of attack rounds increased.
-
Key words:
- Lightweight block cipher /
- ESF algorithm /
- Related-key /
- Impossible differential attack
-
表 1 符号约定
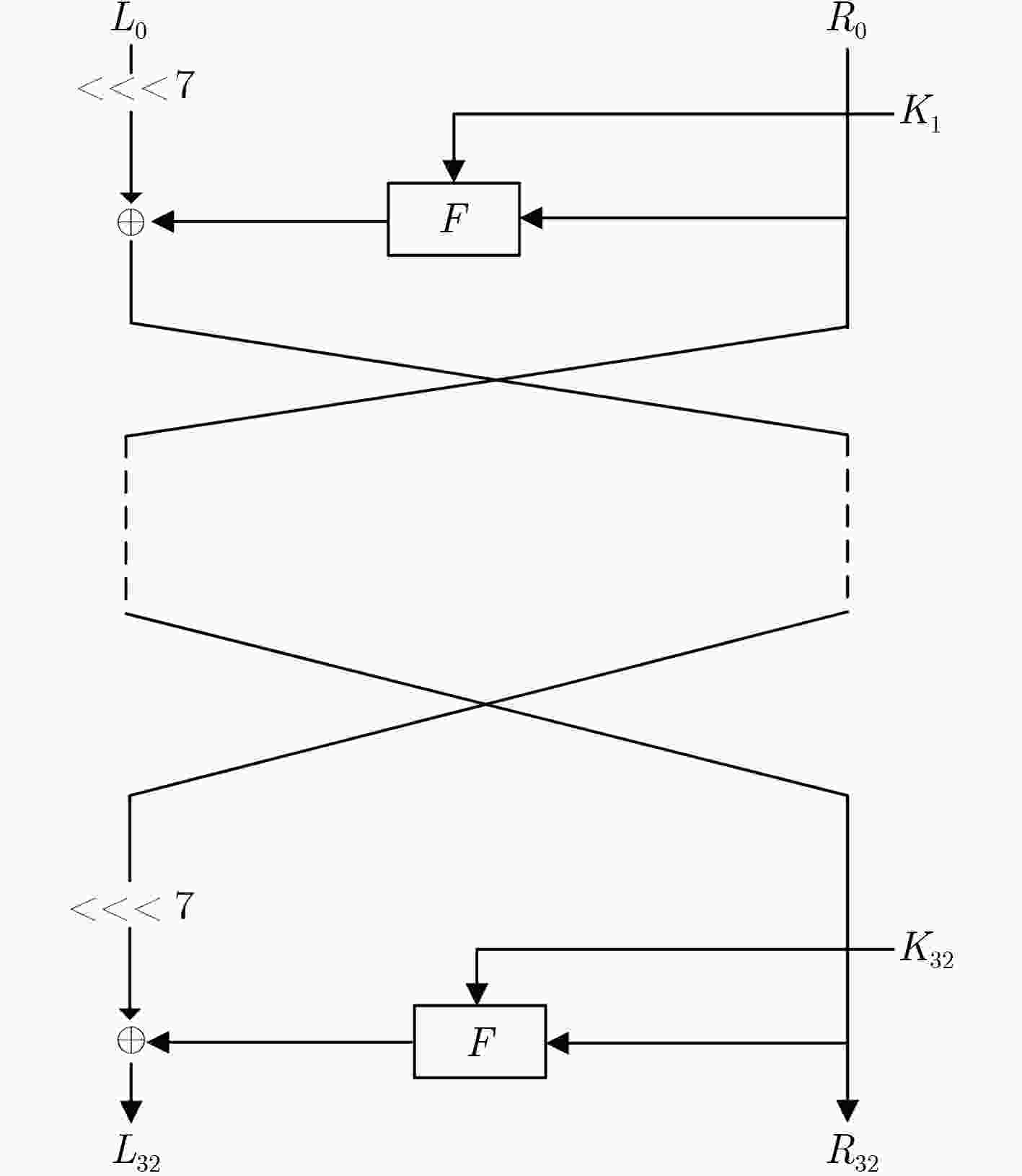
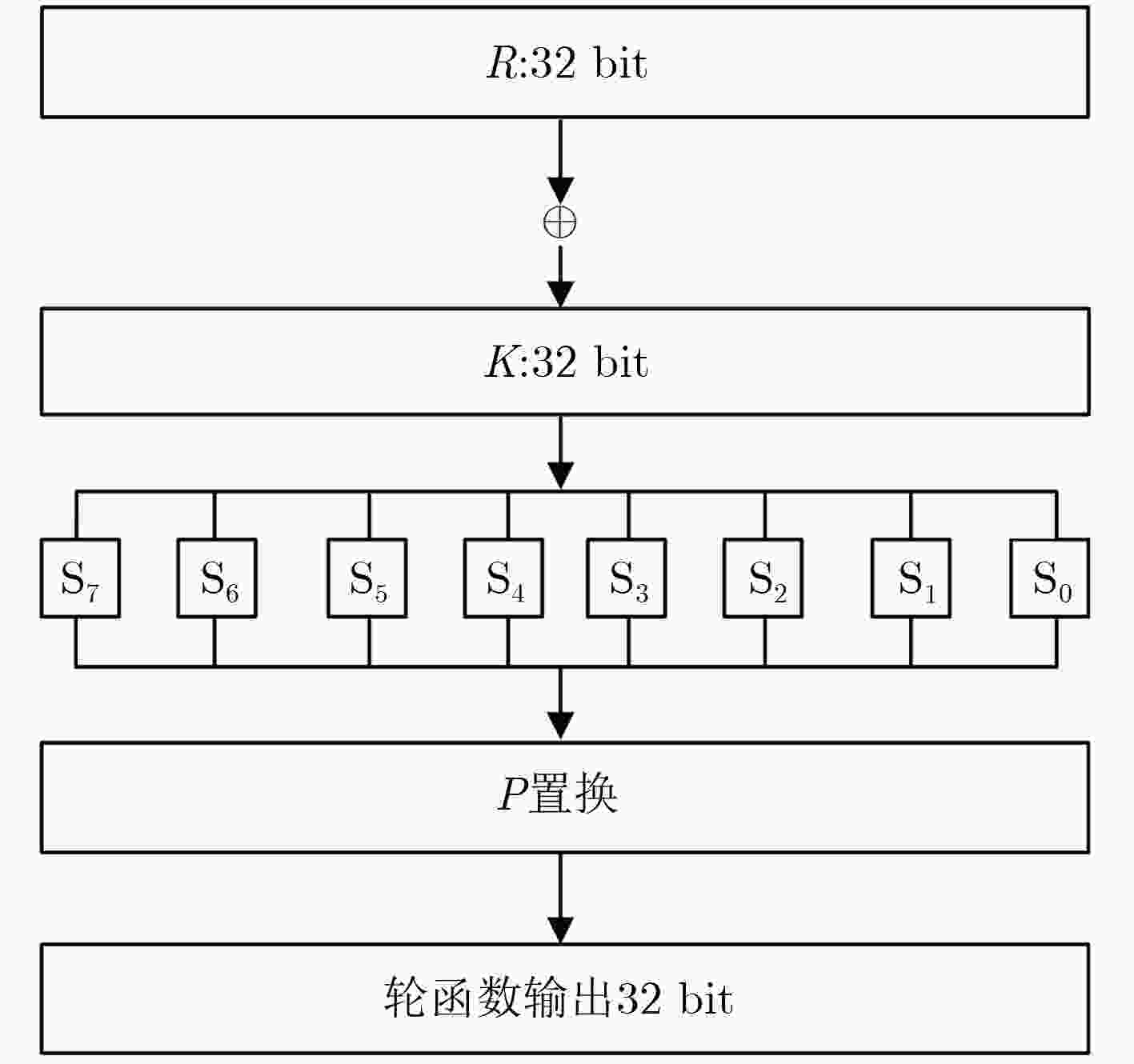
符号 意义 $K$ 80 bit主密钥 ${K_i}$ 第$i\,$轮的32 bit轮密钥 ${K_{i, j}}$ ${K_i}$的第$j$个半字节 $K_{i, j}^l$ ${K_{i, j}}$的第$l$位 ${L_i}$ 第$i\,$轮输出密文的左边32 bit ${R_i}$ 第$i\,$轮输出密文的右边32 bit $ < < < 7$ 循环左移7位 $ \oplus $ 按位异或运算符 $||$ 二进制字符联接 ${[i]_2}$ 常数$i\,$的二进制表示 表 2 15轮相关密钥差分路径
$\Delta K = (00000200000000000000)$ $\Delta {K_1}$ $0000 0200$ $\Delta {K_9}$ $0000 0000$ $\Delta {K_2}$ $0040 0000$ $\Delta {K_{10}}$ $0000 0000$ $\Delta {K_3}$ $0000 0000$ $\Delta {K_{11}}$ $0000 0000$ $\Delta {K_4}$ $0000 0000$ $\Delta {K_{12}}$ $0000 0000$ $\Delta {K_5}$ $0000 0000$ $\Delta {K_{13}}$ $0000 0020$ $\Delta {K_6}$ $0000 0000$ $\Delta {K_{14}}$ $0004 0000$ $\Delta {K_7}$ $0000 0080$ $\Delta {K_{15}}$ $*000 0000$ $\Delta {K_8}$ $0010 0000$ – – -
WU Wenling and ZHANG Lei. LBlock: A lightweight block cipher[C]. Proceedings of 9th International Conference on Applied Cryptography and Network Security, Nerja, Spain, 2011: 327–344. doi: 10.1007/978-3-642-21554-4_19. IZADI M, SADEGHIYAN B, SADEGHIAN S, et al. MIBS: A new light-weight block cipher[C]. Proceedings of CANS 2009, Ishikawa, Japan, 2009: 334–348. doi: 10.1007/978-3-642-10433-6_22. BOGDANOV A, KNUDSEN L, LEANDER G, et al. PRESENT: An ultra-lightweight block cipher[C]. Proceedings of Cryptographic Hardware and Embedded Systems, Vienna, Austria, 2007: 450–466. doi: 10.1007/978-3-540-74735-2_31. 刘宣, 刘枫, 孟帅. 轻量级分组密码算法ESF的不可能差分分析[J]. 计算机工程与科学, 2013, 35(9): 89–95. doi: 10.3969/j.issn.1007-130X.2013.09.014LIU Xuan, LIU Feng, and MENG Shuai. Impossible differential cryptanalysis of lightweight block ciper ESF[J]. Computer and Engineering Science, 2013, 35(9): 89–95. doi: 10.3969/j.issn.1007-130X.2013.09.014 陈玉磊, 卫宏儒. ESF算法的不可能差分密码分析[J]. 计算机科学, 2016, 43(8): 89–91. doi: 10.11896/j.issn.1002-137X.2016.8.018CHEN Yulei and WEI Hongru. Impossible differential cryptanalysis of ESF[J]. Computer Science, 2016, 43(8): 89–91. doi: 10.11896/j.issn.1002-137X.2016.8.018 高红杰, 卫宏儒. 用不可能差分法分析12轮ESF算法[J]. 计算机科学, 2017, 44(8): 147–150. doi: 10.11896/j.issn.1002-137X.2017.10.028GAO Hongjie and WEI Hongru. Impossible differential attack on 12-round block cipher ESF[J]. Computer Science, 2017, 44(8): 147–150. doi: 10.11896/j.issn.1002-137X.2017.10.028 尹军, 马楚炎, 宋健, 等. 轻量级分组密码算法ESF的安全性分析[J]. 计算机研究与发展, 2017, 54(10): 2224–2231. doi: 10.7544/issn1000-1239.2017.20170455YIN Jun, MA Chuyan, SONG Jian, et al. Security analysis of lightweight block cipher ESF[J]. Journal of Computer Research and Development, 2017, 54(10): 2224–2231. doi: 10.7544/issn1000-1239.2017.20170455 尹军, 宋健, 曾光, 等. 轻量级分组密码算法ESF的相关密钥差分分析[J]. 密码学报, 2017, 4(4): 333–344. doi: 10.13868/j.cnki.jcr.000186YIN Jun, SONG Jian, ZENG Guang, et al. Related-key differential attack on lightweight block cipher ESF[J]. Journal of Cryptologic Research, 2017, 4(4): 333–344. doi: 10.13868/j.cnki.jcr.000186 KNUDSEN L. Crypatanalysis of LOKI[C] Proceedings of Advances in Cryptology, Gold Coast, Australia, 1991: 22–35. BIHAM E. New types of cryptanalytic attacks using related keys[J]. Journal of Cryptology, 1994, 7(4): 229–246. doi: 10.1007/BF00203965 BIHAM E, BIRYUKOV A, and SHAMIR A. Cryptanalysis of Skipjack reduced to 31 rounds using impossible differentials[C]. Proceedings of Advances in Cryptolog EUROCRYPT'99. Prague, CZ, 1999: 12–23. doi: 10.1007/3-540-48910-x_2. JIANG Zilong and JIN Chenhui. Impossible differential cryptanalysis of 8-round Deoxys-BC-256[J]. IEEE Access, 2018, 6: 8890–8895. doi: 10.1109/ACCESS.2018.2808484 徐洪, 苏鹏晖, 戚文峰. 减轮SPECK算法的不可能差分分析[J]. 电子与信息学报, 2017, 39(10): 2479–2486. doi: 10.11999/JEIT170049XU Hong, SU Penghui, and QI Wenfeng. Impossible differential cryptanalysis of reduced-round SPECK[J]. Journal of Electronics &Information Technology, 2017, 39(10): 2479–2486. doi: 10.11999/JEIT170049 付立仕, 金晨辉. MIBS-80的13轮不可能差分分析[J]. 电子与信息学报, 2016, 38(4): 848–855. doi: 10.11999/JEIT150673FU Lishi and JIN Chenhui. Impossible differential cryptanalysis on 13-round MIBS-80[J]. Journal of Electronics &Information Technology, 2016, 38(4): 848–855. doi: 10.11999/JEIT150673 XIE Min, LI Jingjing, and ZANG Yuechuan. Related-key impossible differential cryptanalysis of LBlock[J]. Chinese Journal of Electronics, 2017, 26(1): 35–41. doi: 10.1049/cje.2016.06.031 CHENG Lu, XU Peng, and WEI Yuechuan. New related-key impossible differential attack on MIBS-80[C]. Proceedings of 2016 International Conference on Intelligent Networking and Collaborative Systems, Ostrawva, CZ, 2016: 203–206. doi: 10.1109/incos.2016.41. -





 下载:
下载:


 下载:
下载:
