Hybrid Group Signcryption Scheme Based on Heterogeneous Cryptosystem
-
摘要:
群组签密既能实现群组签名,又能实现群组加密,但是现有的群组签密方案的发送者和接收者基本上在同一个密码系统中,不能满足现实环境的需求,而且基本上采用的是公钥加密技术,公钥加密技术在加密长消息时效率较低。因此该文提出由基于身份的密码体制(IBC)到无证书密码体制(CLC)的异构密码系统的混合群组签密方案。在该方案中,私钥生成器(PKG)和密钥生成中心(KGC)能够分别在IBC密码体制和CLC密码体制中产生自己的系统主密钥;而且群组成员只有协作才能解签密,提高了方案的安全性;同时在无需更换群组公钥和其他成员私钥的情况下,用户可以动态地加入该群组。所提方案采用了混合签密,具有可加密任意长消息的能力。在随机预言模型下,证明了该文方案在计算Diffie-hellman困难问题下具有保密性和不可伪造性。通过理论和数值实验分析表明该方案具有更高的效率和可行性。
Abstract:Group signcryption is a cryptosystem which can realize group signature and group encryption. However, the message sender and receiver of existing group signcryption schemes are basically in the same cryptosystem, which does not meet the needs of the real environment and the public key encryption technology is basically used, public key encryption technology in encrypted long message efficiency is too low. Therefore, this paper proposes a hybrid group signcryption scheme based on heterogeneous cryptosystem from Identity-Based Cryptosystem (IBC) to CertificateLess Cryptosystem (CLC). In the scheme, The Private Key Generator (PKG) in the IBC cryptosystem and Key Generation Center (KGC) in the CLC cryptosystem generate their own system master keys, and group members can only solve signcryption through collaboration, which improves the security of the scheme. Meanwhile, the user can dynamically join the group without changing the group public key and other members’ private key. The scheme uses hybrid signcryption and has the ability to encrypt any long message. It is proved that the scheme satisfies confidentiality and unforgeability in computing the Diffie-hellman hard problem in the random oracle model. Theoretical and numerical analysis shows that the scheme is more efficient and feasible.
-
表 1 效率分析
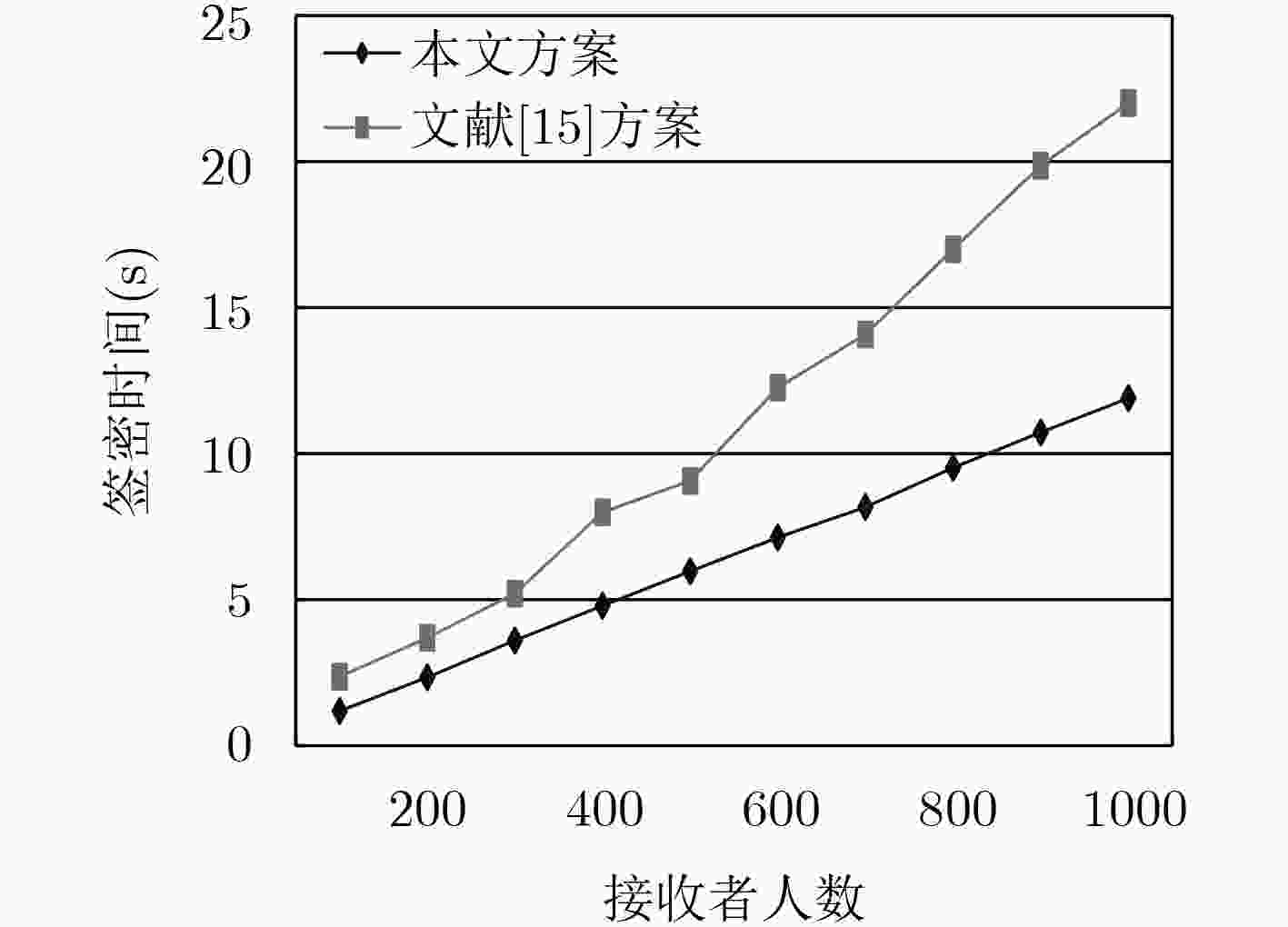
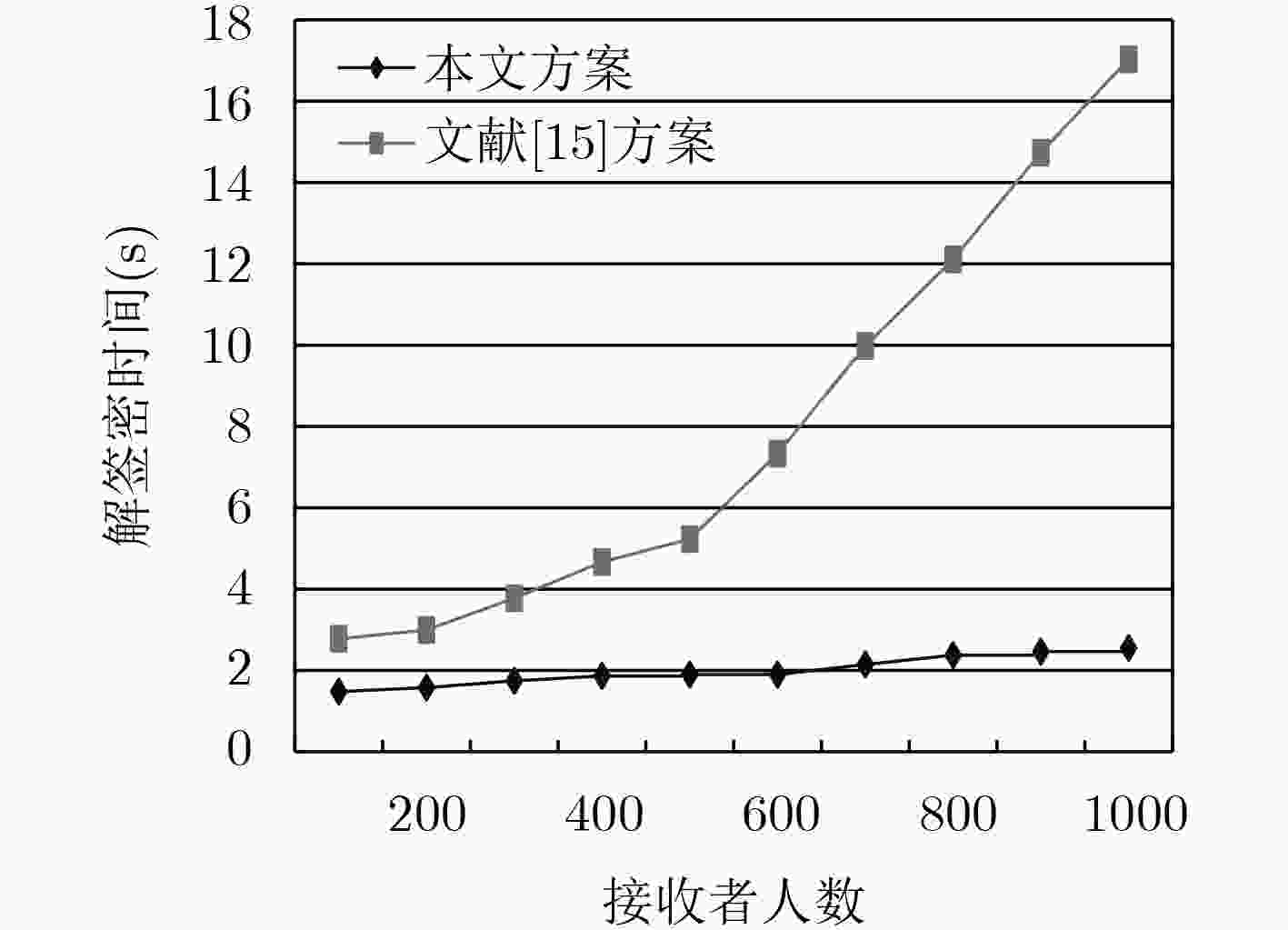
方案 签密阶段运算量 解签密阶段运算量 签密密文长度 文献[13] $(2{n^2} + 7n + 3){P_M} + 3{P_H}$ $({n^2} + n + 3){P_M} + 3{P_H}$ $2|{G_1}| + 3|{{Z}}_q^*|$ 文献[15] $(2{n^2} + 3n + 2){P_M} + 3{P_H}$ $({n^2} + n + 2){P_M} + 3{P_H}$ $|{G_1}| + 3|{{Z}}_q^*|$ 本文 $(2n + 7){P_M} + 4{P_H}$ $(2n + 5){P_M} + 3{P_H}$ $|{G_1}| + 4|{{Z}}_q^*|$ 表 2 本文方案计算时间(s)
n 100 200 300 400 500 600 700 800 900 1000 签密时间 1.1861 2.3375 3.6016 4.7899 5.9708 7.1283 8.1671 9.5163 10.7285 11.8963 解签密时间 1.4792 1.5774 1.7442 1.8645 1.8991 1.9001 2.1469 2.3773 2.4658 2.5549 -
ZHENG Yuliang. Digital signcryption or how to achieve cost(signature & encryption) << cost(signature) +cost(encryption)[C]. Proceedings of the Cryptology-CRYPTO 1997, California, USA, 1997: 165–179. doi: 10.1007/BFb0052234. BAEK J, STEINFELD R, and ZHENG Yuliang. Formal proofs for the security of signcryption[C]. Proceedings of the Cryptology-PKC2002, Paris, France, 2002: 81–98. doi: 10.1007/3-540-45664-3_6. 张宇, 陈晶, 杜瑞颖, 等. 适于车载网安全通信的高效签密方案[J]. 电子学报, 2015, 43(3): 512–517. doi: 10.3969/j.issn.0372-2112.2015.03.015ZHANG Yu, CHEN Jing, DU Ruiying, et al. An efficient signcryption scheme for secure communication of VANET[J]. Acta Electronica Sinica, 2015, 43(3): 512–517. doi: 10.3969/j.issn.0372-2112.2015.03.015 周才学. 几个签密方案的密码学分析与改进[J]. 计算机工程与科学, 2016, 38(11): 2246–2253. doi: 10.3969/j.issn.1007-130X.2016.11.014ZHOU Caixue. Cryptanalysis and improvement of some signcryption schemes[J]. Computer Engineering and Science, 2016, 38(11): 2246–2253. doi: 10.3969/j.issn.1007-130X.2016.11.014 王彩芬, 李亚红, 张玉磊, 等. 标准模型下高效的异构签密方案[J]. 电子与信息学报, 2017, 39(4): 881–886. doi: 10.11999/JEIT160662WANG Caifen, LI Yahong, ZHANG Yulei, et al. Efficient heterogeneous signcryption scheme under standard model[J]. Journal of Electronics &Information Technology, 2017, 39(4): 881–886. doi: 10.11999/JEIT160662 牛淑芬, 牛灵, 王彩芬, 等. 一种可证安全的异构聚合签密方案[J]. 电子与信息学报, 2017, 39(5): 1213–1218. doi: 10.11999/JEIT160829NIU Shufen, NIU Ling, WANG Caifen, et al. A provable aggregate signcryption for heterogeneous systems[J]. Journal of Electronics &Information Technology, 2017, 39(5): 1213–1218. doi: 10.11999/JEIT160829 薛鹏. 混合加密的密钥封装算法研究与设计[D]. [博士论文], 西安电子科技大学, 2014.XUE Peng. Research and design of hybrid encryption key encapsulation algorithm[D]. [Ph.D. dissertation], Xi’an University, 2014. YU Huifang and YANG Bo. Provably secure certificateless hybrid signcryption[J]. Chinese Journal of Computers, 2015, 38(4): 804–813. doi: 10.3724/SP.J.1016.2015.00804 卢万谊, 韩益亮, 杨晓元. 前向安全的可公开验证无证书混合签密方案[C]. 中国计算机学会服务计算学术会议, 西安, 中国, 2012: 1–6.LU Wanyi, HAN Yiliang, and YANG Xiaoyuan. Forward secure publicly verifiable hybrid certificateless signcryption scheme[C]. Academic Conference on Service Computing of China Computer Society, Xi’an, China, 2012: 1–6. 周彦伟, 杨波, 王青龙. 可证安全的抗泄露无证书混合签密机制[J]. 软件学报, 2016, 27(11): 2898–2911. doi: 10.13328/j.cnki.jos.004941ZHOU Yanwei, YANG Bo, and WANG Qinglong. Provably secure leakage-resilient certificateless hybrid signcryption scheme[J]. Journal of Software, 2016, 27(11): 2898–2911. doi: 10.13328/j.cnki.jos.004941 徐鹏, 薛伟. 可公开验证的无证书混合签密方案[J]. 计算机应用与软件, 2017(11): 278–283. doi: 10.3969/j.issn.1000-386x.2017.11.051XU Peng and XUE Wei. A publicly verifiable certificateless hybrid signcryption scheme[J]. Computer Application and Software, 2017(11): 278–283. doi: 10.3969/j.issn.1000-386x.2017.11.051 张波, 徐秋亮. 基于身份的面向群组签密方案[C]. 中国计算机网络与信息安全学术会议, 天津, 中国, 2009: 23–28.ZHANG Bo and XU Qiuliang. Identity based group oriented signcryption scheme[C]. China Academic Conference on Computer Network and Information Security, Tianjin, China, 2009: 23–28. 陈尚弟, 卞广旭. 一种新的基于身份的群体签密方案[J]. 中国民航大学学报, 2013, 31(1): 93–96. doi: 10.3969/j.issn.1674-5590.2013.01.022CHEN Shangdi and BIAN Guangxu. A new identity based group signcryption scheme[J]. Journal of Civil Aviation University of China, 2013, 31(1): 93–96. doi: 10.3969/j.issn.1674-5590.2013.01.022 冯君, 汪学明. 一种高安全的门限群签密方案[J]. 计算机应用研究, 2013, 30(2): 503–506. doi: 10.3969/j.issn.1001-3695.2013.02.051FENG Jun and WANG Xueming. A high security threshold group signcryption scheme[J]. Computer Application Research, 2013, 30(2): 503–506. doi: 10.3969/j.issn.1001-3695.2013.02.051 PENG Changgen, LI Xiang, and LUO Wenjun. A generalized group-oriented threshold signcryption schemes[J]. Acta Electronica Sinica, 2007, 35(1): 64–67. POINTCHEVAL D and STERN J. Security arguments for digital signatures and blind signatures[J]. Journal of Cryptology, 2000, 13(3): 361–396. doi: 10.1007/s001450010003 -





 下载:
下载:


 下载:
下载:
