Design and Implementation of Hardware Trojan Detection Algorithm for Coarse-grained Reconfigurable Arrays
-
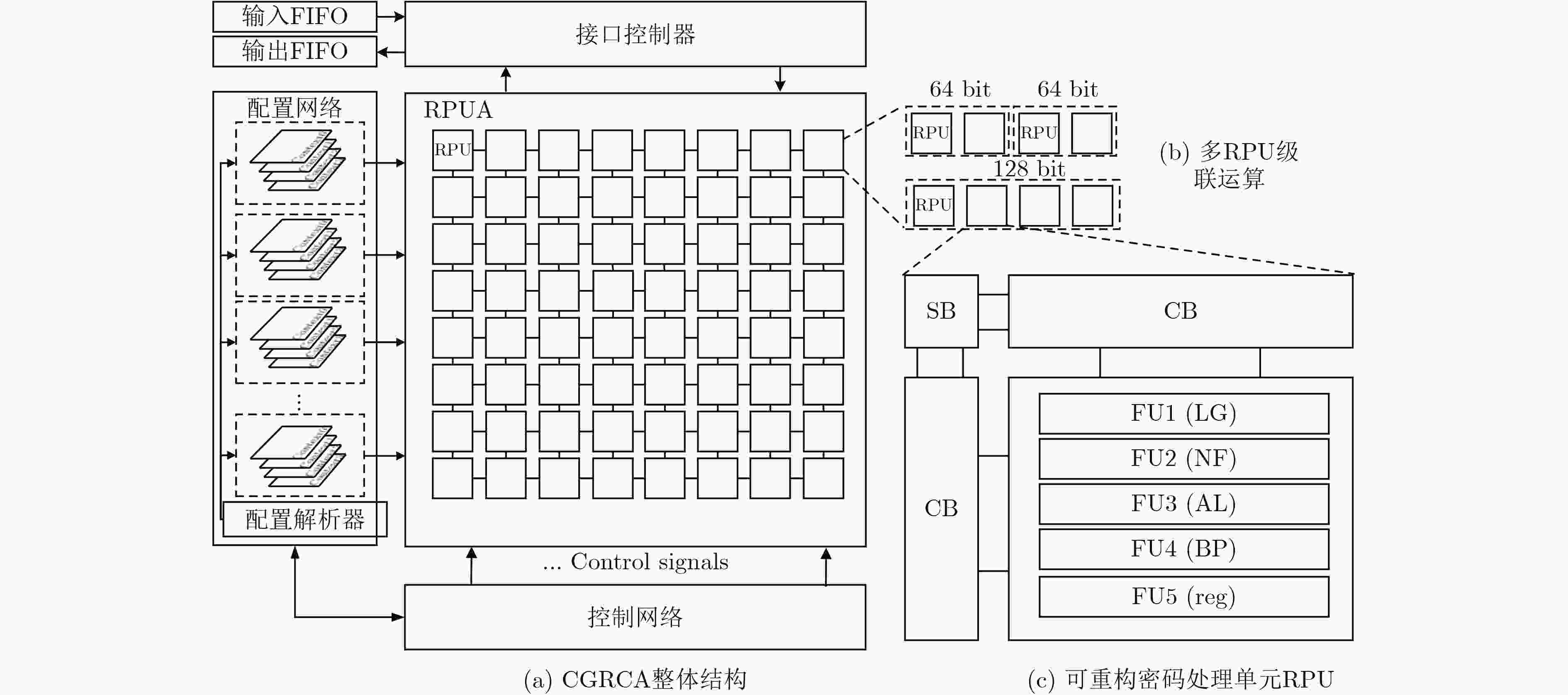
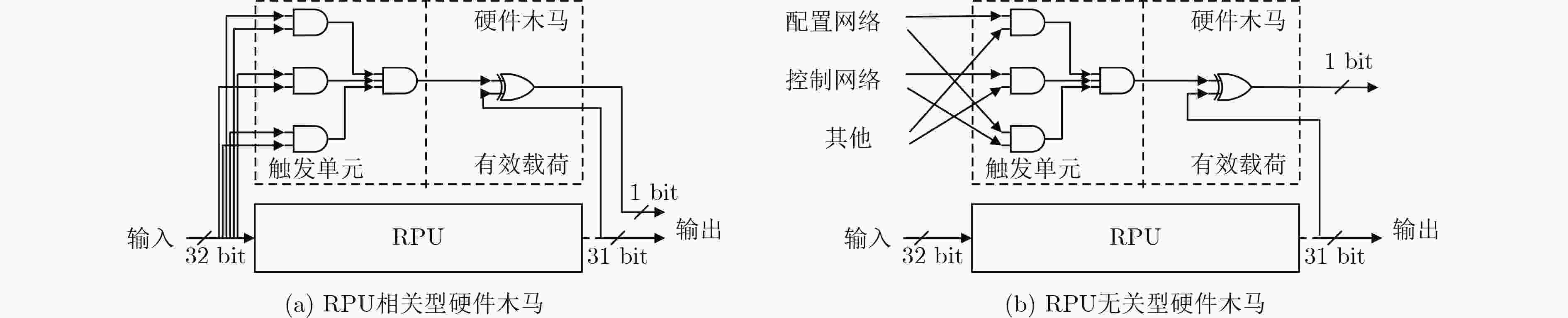
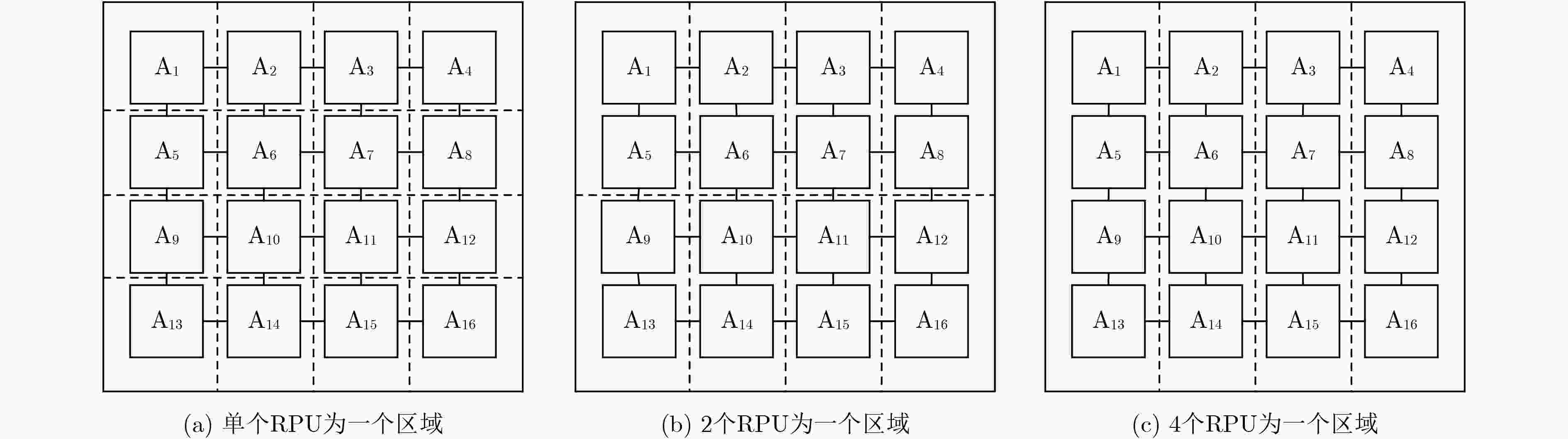
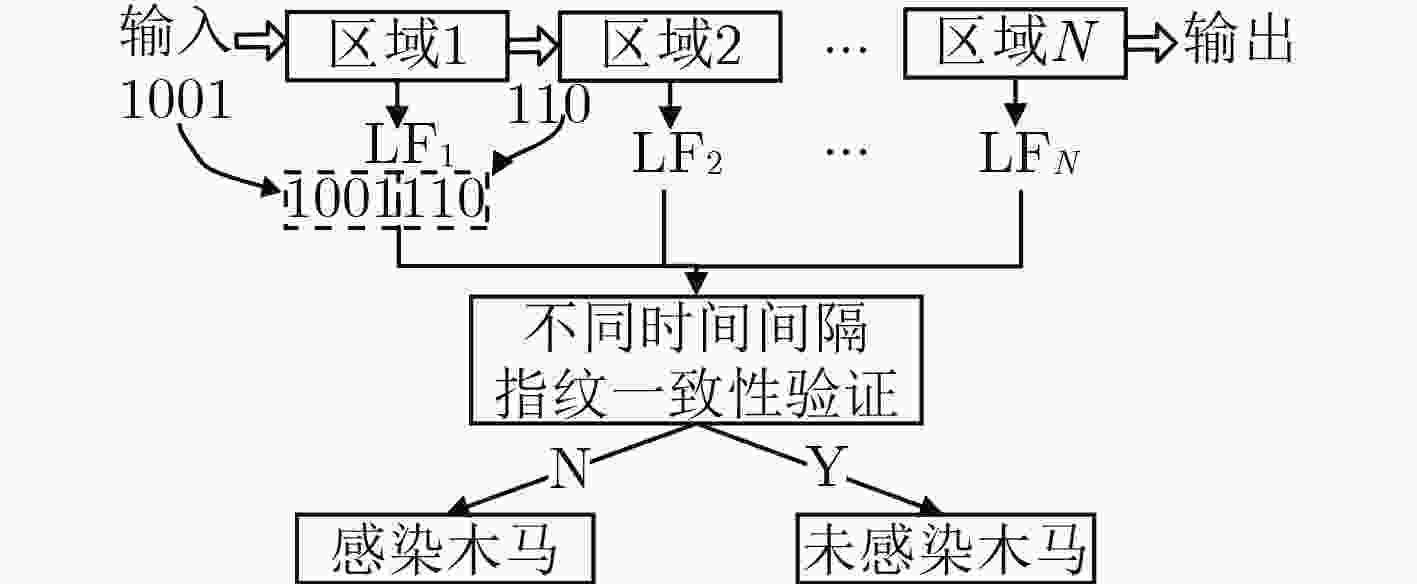
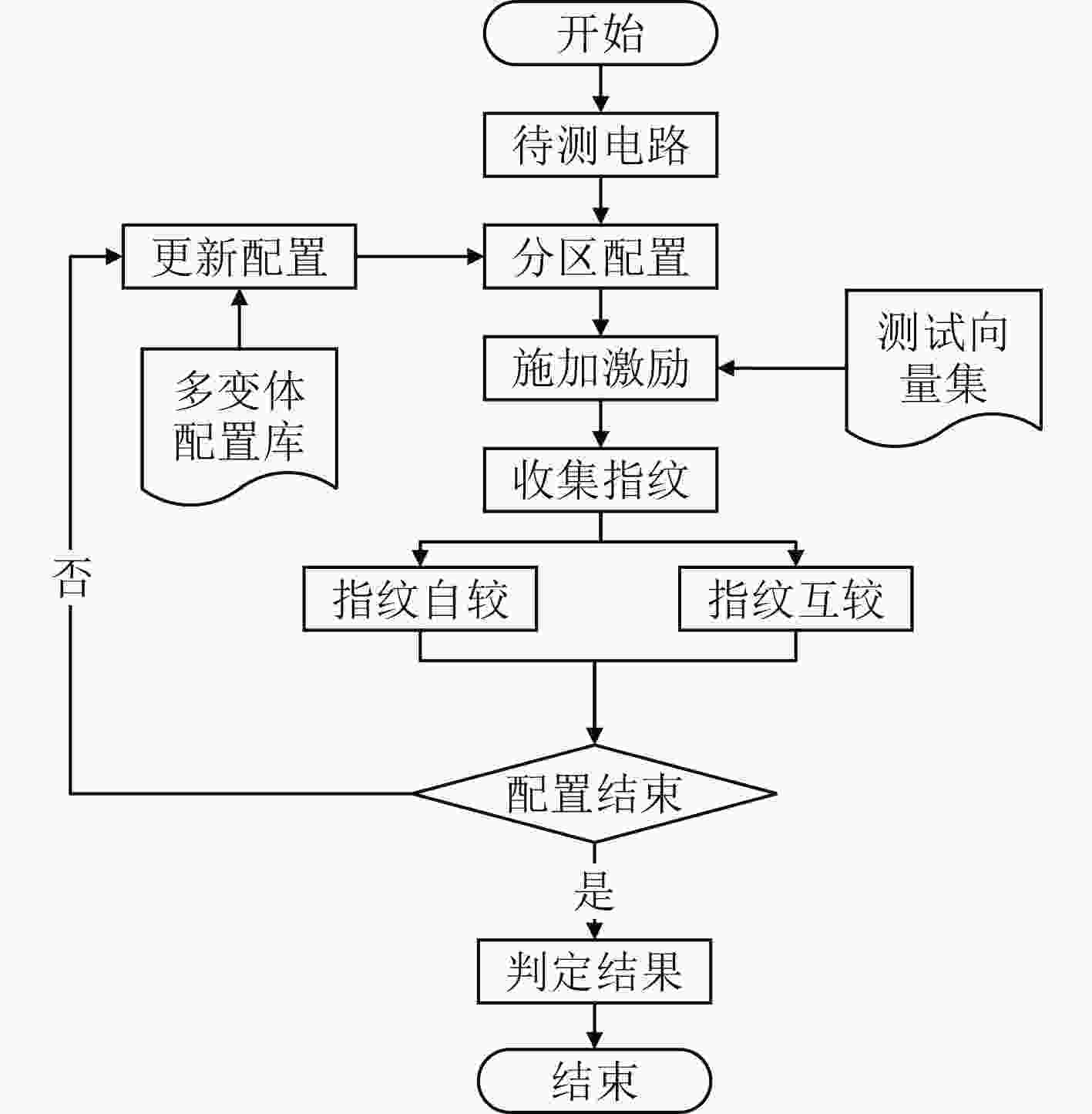
摘要: 硬件木马检测已成为当前芯片安全领域的研究热点,现有检测算法大多面向ASIC电路和FPGA电路,且依赖于未感染硬件木马的黄金芯片,难以适应于由大规模可重构单元组成的粗粒度可重构阵列电路。因此,该文针对粗粒度可重构密码阵列的结构特点,提出基于分区和多变体逻辑指纹的硬件木马检测算法。该算法将电路划分为多个区域,采用逻辑指纹特征作为区域的标识符,通过在时空两个维度上比较分区的多变体逻辑指纹,实现了无黄金芯片的硬件木马检测和诊断。实验结果表明,所提检测算法对硬件木马检测有较高的检测成功率和较低的误判率。
-
关键词:
- 硬件木马检测 /
- 粗粒度可重构密码阵列 /
- 逻辑指纹 /
- 多变体
Abstract: Hardware Trojan horse detection has become a hot research topic in the field of chip security. Most existing detection algorithms are oriented to ASIC circuits and FPGA circuits, and rely on golden chips that are not infected with hardware Trojan horses, which are difficult to adapt to the coarse-grained reconfigurable array consisting of large-scale reconfigurable cells. Therefore, aiming at the structural characteristics of Coarse-grained reconfigurable cryptographic logical arrays, a hardware Trojan horse detection algorithm based on partitioned and multiple variants logic fingerprints is proposed. The algorithm divides the circuit into multiple regions, adopts the logical fingerprint feature as the identifier of the region, and realizes the hardware Trojan detection and diagnosis without golden chip by comparing the multiple variant logic fingerprints of the regions in both dimensions of space and time. Experimental results show that the proposed detection algorithm has high detection success rate and low misjudgment rate for hardware Trojan detection. -
表 1 检测结果可能情况
实际情况 检测情况 不含硬件木马 含有硬件木马 不含硬件木马 正确 错误 含有硬件木马 错误 正确 表 2 待测电路具体情况
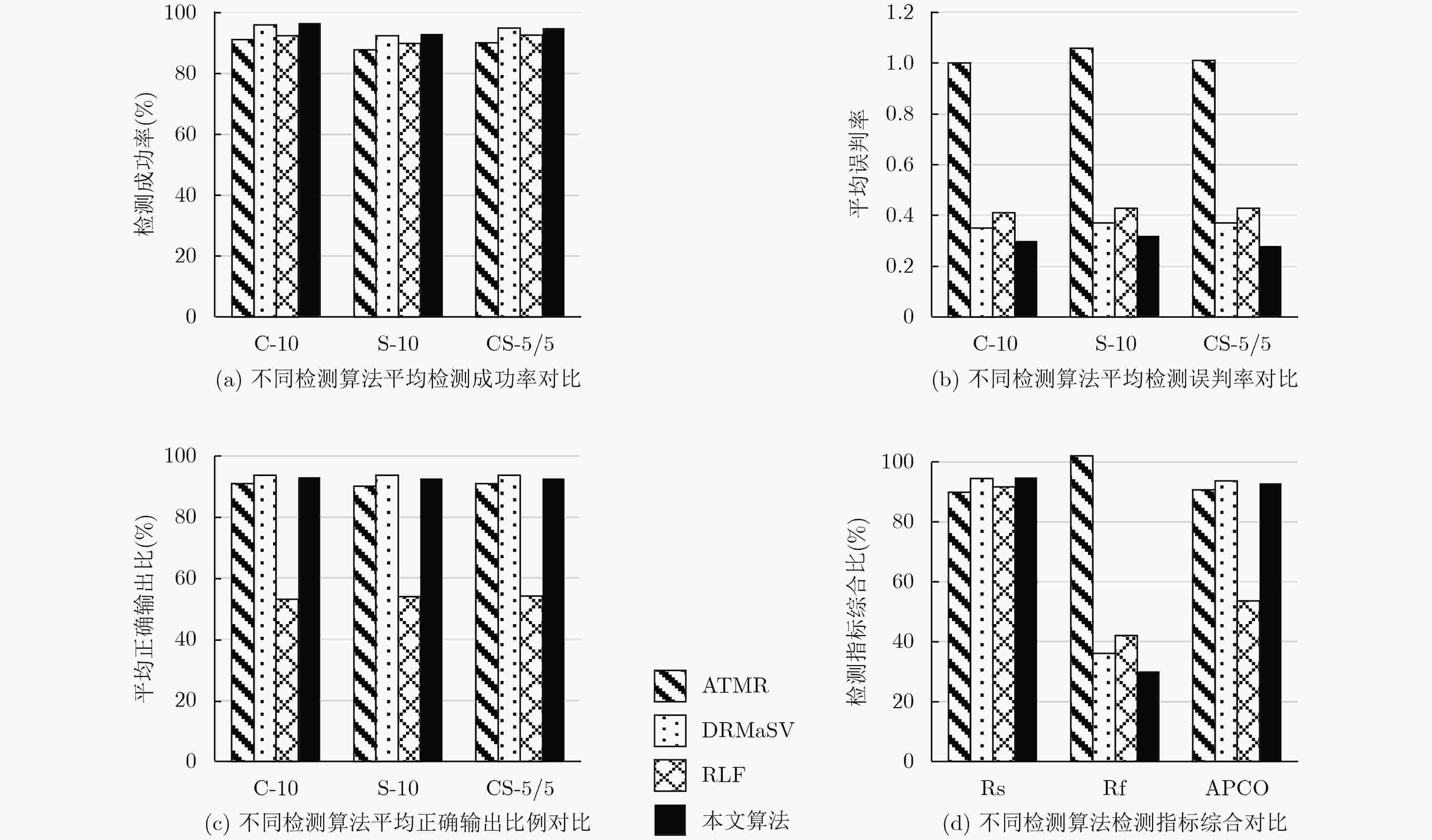
电路编号 分区数 线网数 输入 输出 木马面积占比(%) 原始电路 16 260 49 44 / C-10 16 260 49 44 0.015 S-10 16 260 49 44 0.025 CS-5/5 16 260 49 44 0.031 表 3 检测算法实验结果对比(%)
电路编号 ATMR DRMaSV RLF 本文算法 Rs Rf APCO Rs Rf APCO Rs Rf APCO Rs Rf APCO C-10 AES 91.1 1.02 91.3 97.2 0.37 93.7 93.1 0.45 52.1 97.3 0.31 93.2 SMS4 92.9 0.98 91.7 97.3 0.35 93.8 93.2 0.41 54.1 97.7 0.29 93.7 A5/1 89.7 0.99 89.9 93.5 0.32 93.9 91.1 0.37 52.7 94.7 0.30 92.1 均值 91.2 1.00 91.0 96.0 0.35 93.8 92.5 0.41 53.0 96.6 0.30 93.0 S-10 AES 89.7 1.13 90.2 93.2 0.39 93.5 89.6 0.47 53.7 93.4 0.32 93.3 SMS4 88.5 1.05 90.3 93.4 0.38 93.9 90.1 0.44 53.9 93.3 0.31 92.9 A5/1 85.3 1.01 89.7 90.5 0.33 93.4 90.2 0.39 54.1 92.7 0.33 91.7 均值 87.8 1.06 90.1 92.4 0.37 93.6 90.0 0.43 53.9 93.1 0.32 92.6 CS-5/5 AES 90.1 1.00 91.0 95.3 0.39 93.8 93.0 0.46 54.6 95.4 0.27 92.1 SMS4 91.3 0.99 91.3 95.6 0.37 94.0 92.7 0.43 54.7 95.6 0.27 93.2 A5/1 89.3 1.01 90.7 93.7 0.35 93.5 92.3 0.39 53.3 93.7 0.31 92.7 均值 90.2 1.00 91.0 94.9 0.37 93.8 92.7 0.43 54.2 94.9 0.28 92.7 均值 89.8 1.02 90.7 94.4 0.36 93.7 91.7 0.42 53.7 94.9 0.30 92.8 -
AGRAWAL D, BAKTIR S, KARAKOYUNLU D, et al. Trojan detection using IC fingerprinting[C]. IEEE Symposium on Security and Privacy. IEEE Computer Society, Berkeley, USA, 2007: 296–310. KITSOS P, SIMOS D E, TORRES-Jimenez J, et al. Exciting FPGA cryptographic trojans using combinatorial testing[C]. IEEE International Symposium on Software Reliability Engineering, Gaithersbury, USA, 2016: 69–76. 赵剑锋, 史岗. 硬件木马研究动态综述[J]. 信息安全学报, 2017, 2(1): 74–90. doi: 10.19363/j.cnki.cn10-1380/tn.2017.01.006ZHAO Jianfeng and SHI Gang. A survey on the studies of hardware trojan[J]. Journal of Cyber Security, 2017, 2(1): 74–90. doi: 10.19363/j.cnki.cn10-1380/tn.2017.01.006 COMPTON K and HAUCK S. Reconfigurable computing: A survey of systems and software[J]. ACM Computing Surveys, 2002, 34(2): 171–210. doi: 10.1145/508352.508353v VEERANNA N and SCHAFER B C. Hardware trojan avoidance and detection for dynamically re-configurable FPGAs[C]. International IEEE Conference on Field-Programmable Technology. Xi'an, China, 2017: 193–196. LIU Leibo, ZHOU Zhuoquan, WEI Shaojun, et al. DRMaSV: Enhanced capability against hardware trojans in coarse grained reconfigurable architectures[J]. IEEE Transactions on Computer-Aided Design of Integrated Circuits and Systems, 2017, 37(4): 782–795. doi: 10.1109/TCAD.2017.2729340 KHALEGHI B, AHARI A, ASADI H, et al. FPGA-based protection scheme against hardware trojan horse insertion using dummy logic[J]. IEEE Embedded Systems Letters, 2015, 7(2): 46–50. doi: 10.1109/LES.2015.2406791 PIRPILIDIS F, STEFANIDIS K G, VOYIATZIS A G, et al. On the effects of ring oscillator length and hardware Trojan size on an FPGA-based implementation of AES[J]. Microprocessors & Microsystems, 2017, 54(1): 75–82. doi: 10.1016/j.micpro.2017.09.001 SARAN T, RANJANI R S, DEVI M N, et al. A region based fingerprinting for hardware Trojan detection and diagnosis[C]. International Conference on Signal Processing and Integrated Networks. Noida, India. 2017: 166–172. MAL-SARKAR S, KARAM R, NARASIMHAN S, et al. Design and validation for FPGA trust under hardware trojan attacks[J]. IEEE Transactions on Multi-Scale Computing Systems, 2017, 2(3): 186–198. doi: 10.1109/TMSCS.2016.2584052 陈韬, 罗兴国, 李校南, 等. 一种基于流处理框架的可重构分簇式分组密码处理结构模型[J]. 电子与信息学报, 2014, 36(12): 3027–3034. doi: 10.3724/SP.J.1146.2014.00023CHEN Tao, LUO Xingguo, LI Xiaonan, et al. An architecture of stream based reconfigurable clustered block cipher processing array[J]. Journal of Electronics &Information Technology, 2014, 36(12): 3027–3034. doi: 10.3724/SP.J.1146.2014.00023 WAKSMAN A and SETHUMADHAVAN S. Silencing hardware backdoors[C]. IEEE Security and Privacy. Berkeley, USA, 2011: 49–63. SASHANK K A, REDDY H S, PAVITHRAN P, et al. Hardware trojan detection using effective test patterns and selective segmentation[C]. International Symposium on Security in Computing and Communication. Singapore, 2017: 379–386. SALMANI H, TEHRANIPOOR M, and PLUSQUELLIC J. A layout-aware approach for improving localized switching to detect hardware trojans in integrated circuits[C]. IEEE International Workshop on Information Forensics and Security, Seattle, USA, 2011: 1–6. XIAO Kan, FORTE D, JIN Yier, et al. Hardware trojans: lessons learned after one decade of research[J]. ACM Transactions on Design Automation of Electronic Systems, 2016, 22(1): 1–23. doi: 10.1145/2906147 MCINTYRE D, WOLFF F, PAPACHRISTOU C, et al. Trustworthy computing in a multi-core system using distributed scheduling[C]. IEEE On-Line Testing Symposium. Corfu, Greece, 2010: 211–213. -





 下载:
下载:


 下载:
下载:
