Adaptive Color Image Steganography Based on Dynamic Distortion Modification
-
摘要:
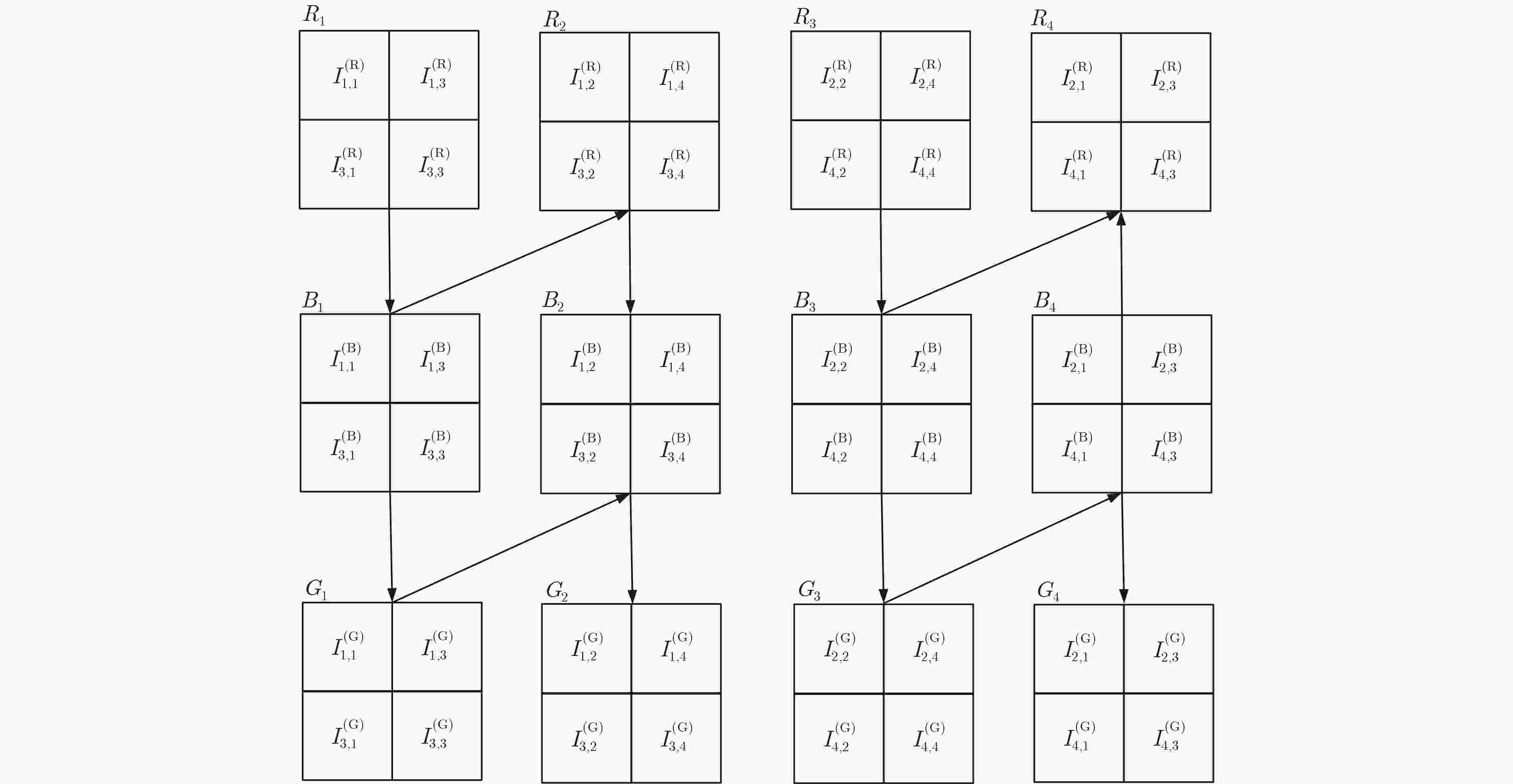
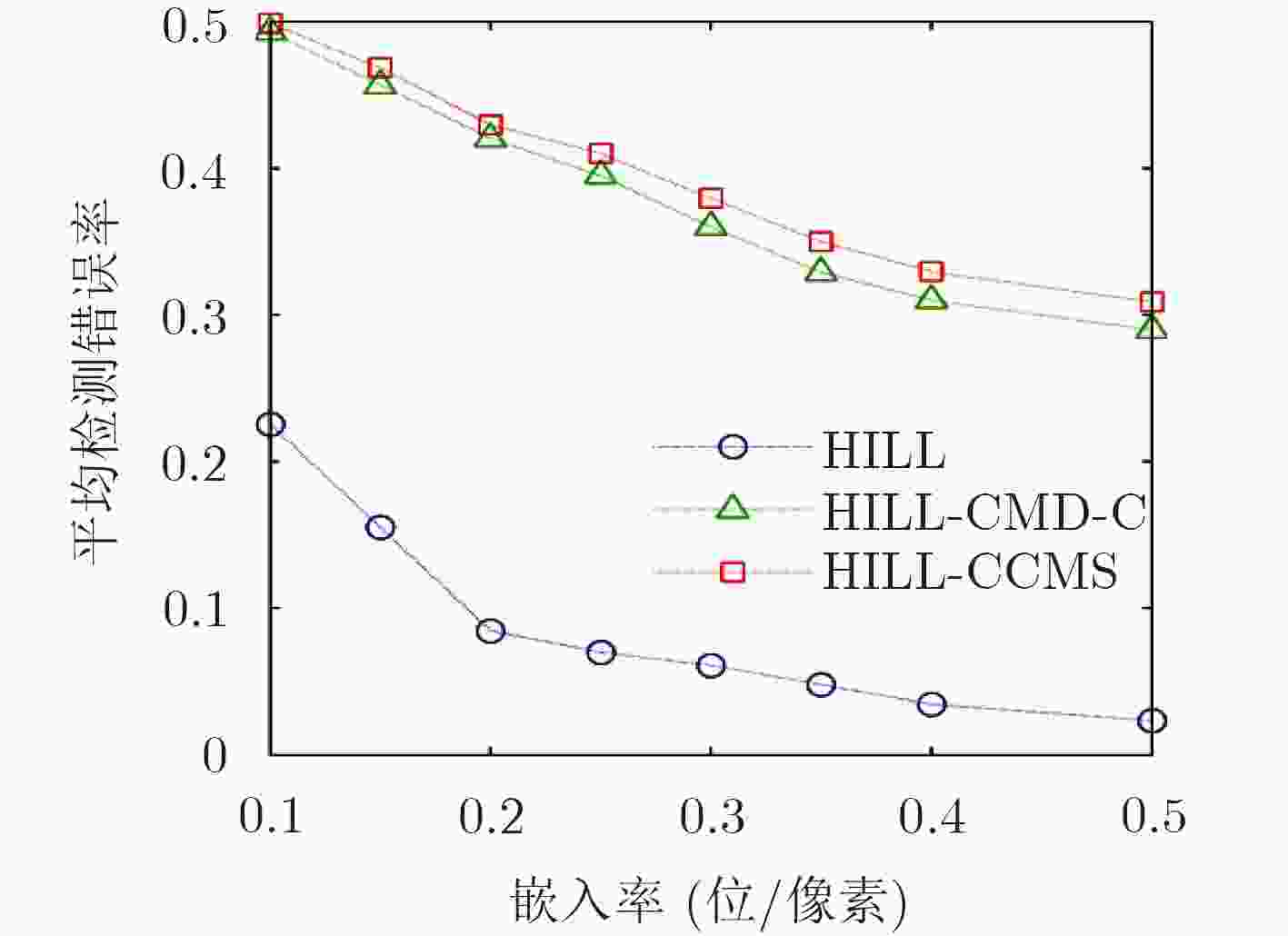
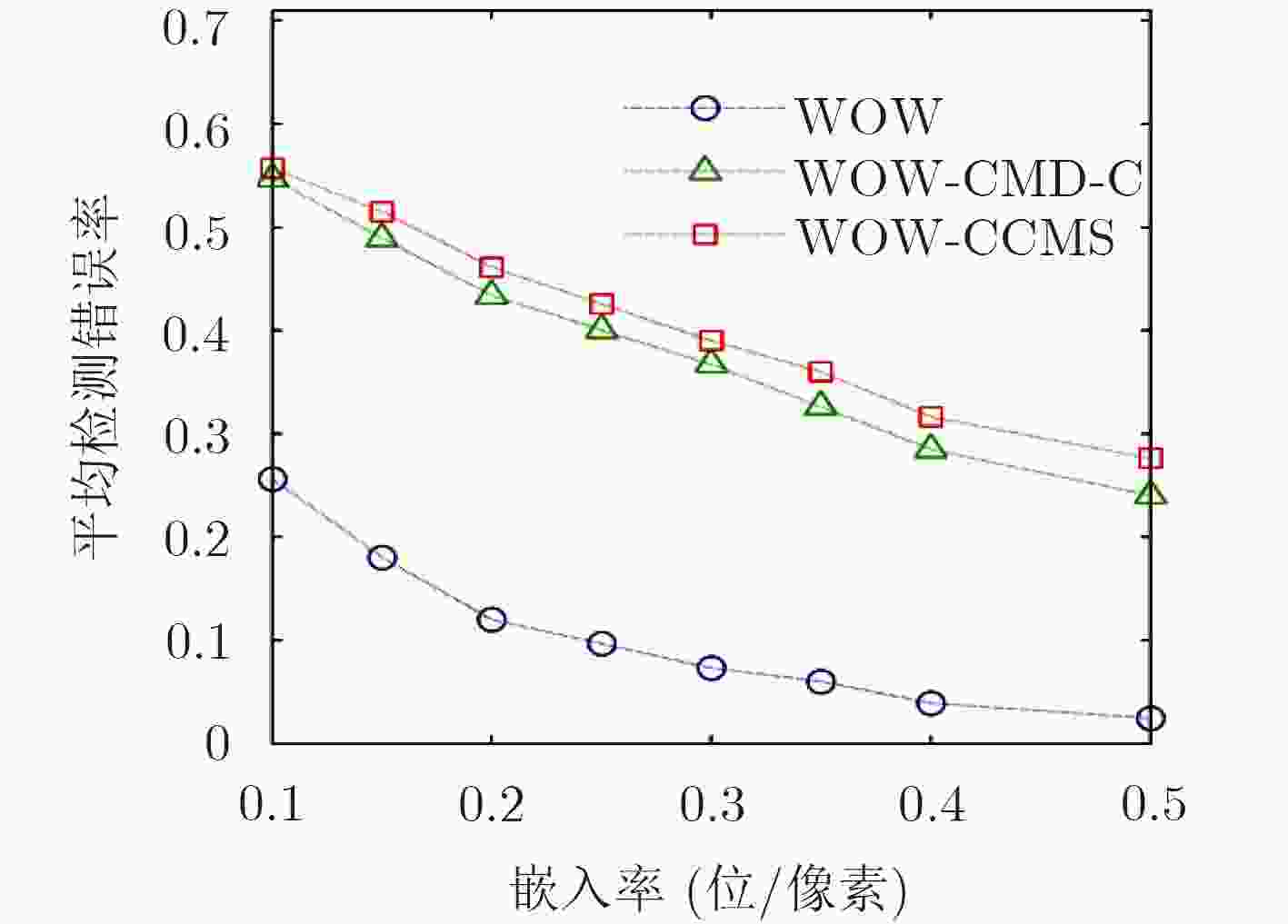
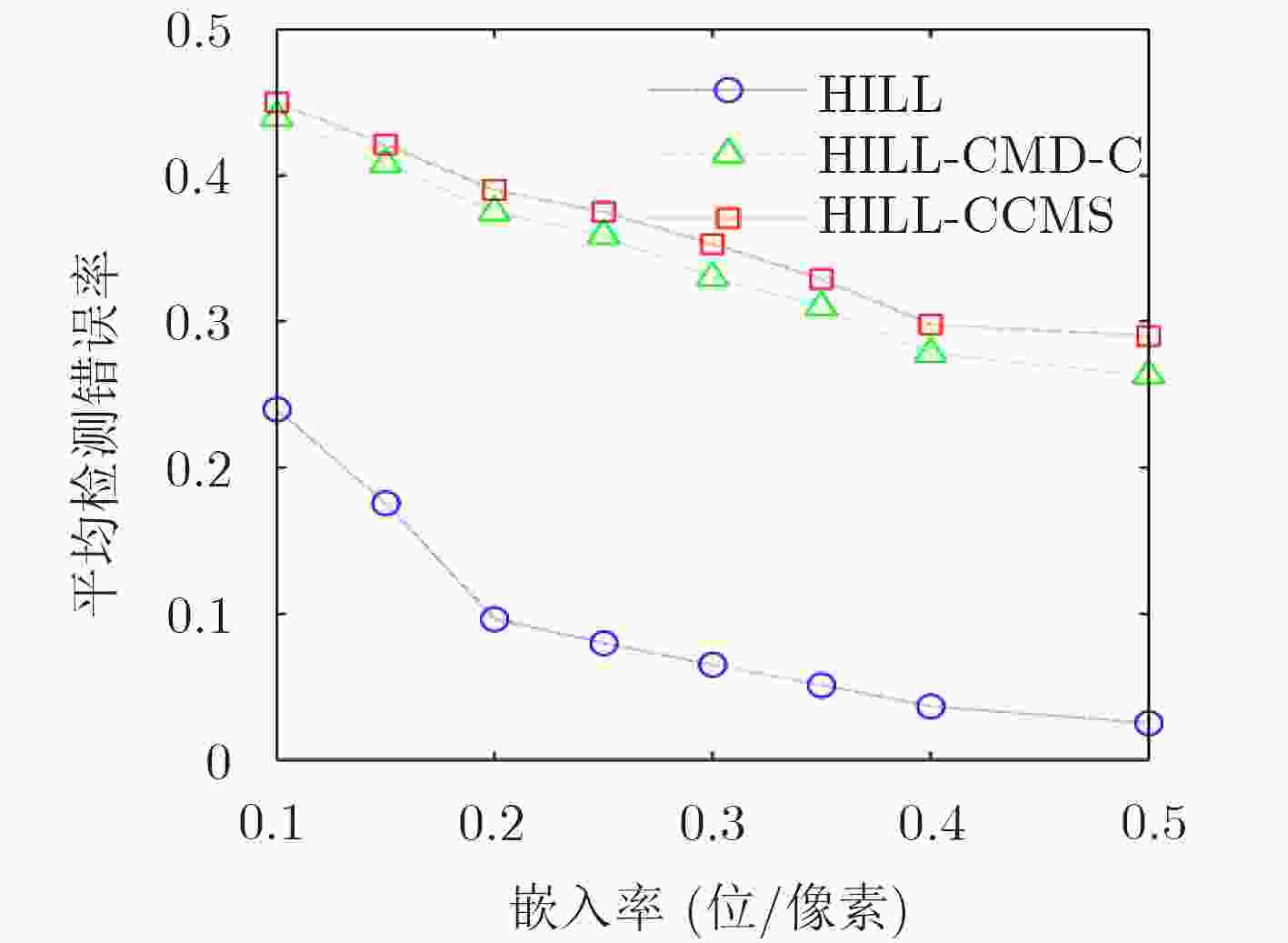
基于灰度图像隐写算法直接应用于彩色图像引起的安全性问题,该文针对彩色分量提出一种动态更新失真代价的空域隐写算法。首先,分析了彩色分量内容特性与通道间相关性的关系,提出中心元素的失真更新准则。随后,考虑到隐写过程中邻域分量嵌入修改产生的交互影响,得到维持邻域相关性的最优修改方式。最后,提出彩色分量的失真代价动态更新策略(CCMS),并应用该策略设计实现了一种彩色图像的空域自适应隐写算法。实验表明,在5种嵌入率下HILL-CCMS,WOW-CCMS算法对彩色隐写特征CRM,SCCRM的抗检测能力明显高于HILL和WOW算法。
Abstract:Considering the possible security problems of directly extending steganographic schemes for gray-scale images to color images, an adaptive distortion-updated steganography method is put forward based on the Modification Strategy for Color Components (CCMS). First, the correlation between color components and RGB channels is analyzed, and the principle of distortion cost modification is proposed. Moreover, the optimal modification mode is conducted to maintain the statistical correlation of adjacent components. Finally, color image steganography schemes called CCMS are proposed. The experimental results show that the proposed HILL-CCMS and WOW-CCMS make great improvement over HILL and WOW methods under 5 embedding rates in resisting state-of-the-art color steganalytic methods such as CRM and SCCRM.
-
表 1 UCID图像库中4幅图像的相关性系数值
序号 HH HL LH LL R/G R/B G/B R/G R/B G/B R/G R/B G/B R/G R/B G/B 1 0.986 0.985 0.983 0.990 0.962 0.994 0.995 0.990 0.995 0.837 0.955 0.941 2 0.941 0.945 0.943 0.934 0.973 0.988 0.927 0.974 0.927 0.479 0.869 0.972 3 0.982 0.978 0.968 0.989 0.983 0.985 0.927 0.975 0.927 0.885 0.909 0.891 4 0.948 0.953 0.939 0.980 0.991 0.976 0.978 0.974 0.978 0.823 0.907 0.904 表 2 3种修改模式的颜色分量修改组合
序号 1 2 3 4 5 6 Syn (0, 0, 0) (+1, +1, +1) (–1, –1, –1) – – – 1-Asyn (+1, 0, 0) (–1, 0, 0) (0, 0, +1) (0, 0, –1) (0, +1, +1) (–1, +1, +1) 2-Asyn (+1, 0, +1) (+1, 0, –1) (–1, 0, +1) (–1, 0, –1) (0, +1, 0) (–1, +1, –1) 序号 7 8 9 10 11 12 Syn – – – – – – 1-Asyn (+1, +1, 0) (+1, +1, –1) (0, –1, –1) (+1, –1, –1) (+1, –1, –0) (–1, –1, +1) 2-Asyn (–1, +1, 0) (0, +1, –1) (0, –1, 0) (+1, –1, 0) (0, –1, +1) (+1, –1, +1) 表 3 彩色分量不同修改模式下的抗隐写检测能力
抗检测性(%) Syn 1-Asyn 2-Asyn SRM 31.5290 31.0850 30.9980 CRM 35.9320 19.8730 2.9473 SCCRM 30.4530 19.9450 3.0272 GCRM 37.7660 21.6840 5.7357 表 4 4种隐写算法隐写后彩色图像的平均峰值信噪比(dB)
嵌入率(bpc) 0.1 0.2 0.3 0.4 0.5 WOW-CMD 39.034 37.516 35.371 33.246 30.617 HILL-CMD 38.915 37.482 35.268 32.192 29.781 WOW-CCMS 40.231 38.647 37.143 35.071 31.726 HILL-CCMS 39.873 38.534 36.894 34.735 31.084 表 5 6种算法对一幅尺寸为
$256 \times 256$ 的彩色图像进行隐写的平均执行时间(s)嵌入率(bpc) 0.1 0.2 0.3 0.4 0.5 WOW 0.4053 0.5012 0.5945 0.6931 0.8967 HILL 0.3018 0.3867 0.4733 0.5591 0.7078 WOW-CMD 0.6123 0.7108 0.8126 0.9128 1.4204 HILL-CMD 0.3742 0.4806 0.5768 0.6932 0.8974 WOW-CCMS 0.6397 0.7403 0.8431 0.9448 1.4532 HILL-CCMS 0.4027 0.5106 0.6093 0.7273 0.9356 -
DENEMARK T D, BOROUMAND M, and FRIDRICH J. Steganalysis features for content-adaptive JPEG steganography[J]. IEEE Transactions on Information Forensics & Security, 2017, 11(8): 1736–1746. doi: 10.1109/TIFS.2016.2555281 汤光明, 边媛, 韦大伟, 等. 一种动态更新失真代价的自适应±k隐写算法[J]. 电子与信息学报, 2017, 39(1): 58–65. doi: 10.11999/JEIT160254TANG Guangming, BIAN Yuan, WEI Dawei, et al. Adaptive ±k steganography based on dynamic updating distortion cost[J]. Journal of Electronics &Information Technology, 2017, 39(1): 58–65. doi: 10.11999/JEIT160254 TANG Weixuan, LI Bin, LUO Weiqi, et al. Clustering steganographic modification directions for color components[J]. IEEE Signal Processing Letters, 2016, 23(2): 197–201. doi: 10.1109/LSP.2015.2504583 PEVNÝ T, FILLER T, and BAS P. Using high-dimensional image models to perform highly undetectable steganography[J]. Lecture Notes in Computer Science, 2010, 6(6387): 161–177. doi: 10.1007/978-3-642-16435-4_13 HOLUB V and FRIDRICH J. Designing steganographic distortion using directional filters[C]. IEEE International Workshop on Information Forensics and Security, Costa Adeje, Spain, 2012: 234–239. FRIDRICH J and KODOVSKY J. Rich models for steganalysis of digital images[J]. IEEE Transactions on Information Forensics & Security, 2012, 7(3): 868–882. doi: 10.1109/TIFS.2012.2190402 FRIDRICH J. Digital image steganography using universal distortion[C]. ACM Workshop on Information Hiding and Multimedia Security, Montpellier, France, 2013: 59–68. LI Bin, WANG Ming, HUANG Jiwu, et al. A new cost function for spatial image steganography[C]. IEEE International Conference on Image Processing, Quebec City, Canada, 2015: 4206–4210. GOLJAN M, FRIDRICH J, and COGRANNE R. Rich model for steganalysis of color images[C]. IEEE International Workshop on Information Forensics and Security, Roma, Italy, 2015: 185–190. ABDULRAHMAN H, CHAUMONT M, MONTESINOS P, et al. Color image stegananalysis using correlations between RGB channels[C]. International Conference on Availability, Reliability and Security, Toulouse, France, 2015: 448–454. ABDULRAHMAN H, CHAUMONT M, MONTESINOS P, et al. Color image steganalysis based on steerable Gaussian filters bank[C]. ACM Workshop on Information Hiding and Multimedia Security, Vigo, Spain, 2016: 109–114. LI Bin, WANG Ming, LI Xiaolong, et al. A strategy of clustering modification directions in spatial image steganography[J]. IEEE Transactions on Information Forensics & Security, 2015, 10(9): 1905–1917. doi: 10.1109/TIFS.2015.2434600 GUNTURK B K, ALTUNBASAK Y, and MERSEREAU R M. Color plane interpolation using alternating projections[J]. IEEE Transactions on Image Processing, 2002, 11(9): 997–1013. doi: 10.1109/TIP.2002.801121 SCHAEFER G and STICH M. UCID - An uncompressed colour image database[J]. Storage & Retrieval Methods & Applications for Multimedia, 2003, 5307: 472–480. doi: 10.1117/12.525375 DING Yong, ZHAO Yang, and ZHAO Xinyu. Image quality assessment based on multi-feature extraction and synthesis with support vector regression[J]. Signal Processing Image Communication, 2017, 54(3): 81–92. doi: 10.1016/j.image.2017.03.001 KODOVSKY J, FRIDRICH J, and HOLUB V. Ensemble classifiers for steganalysis of digital media[J]. IEEE Transactions on Information Forensics & Security, 2012, 7(2): 432–444. doi: 10.1109/TIFS.2011.2175919 -





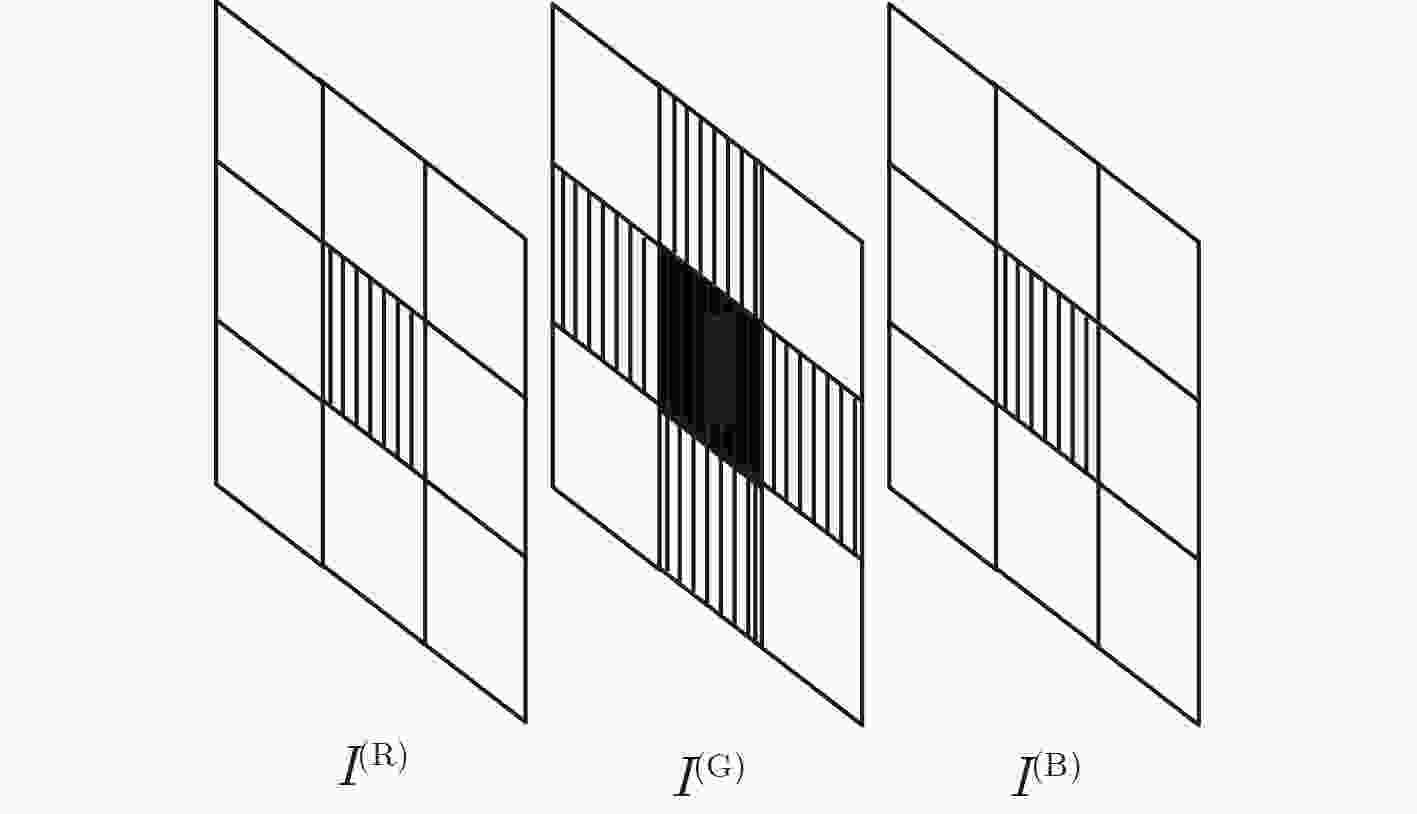
 下载:
下载:
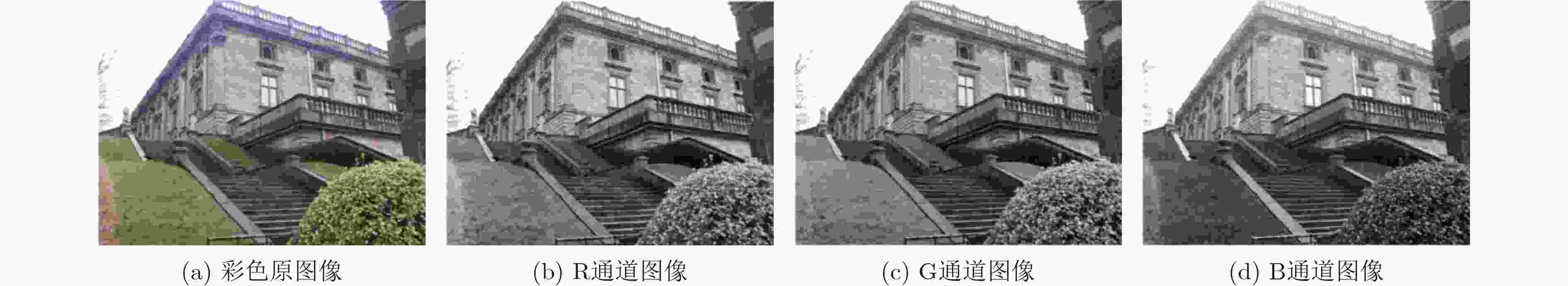

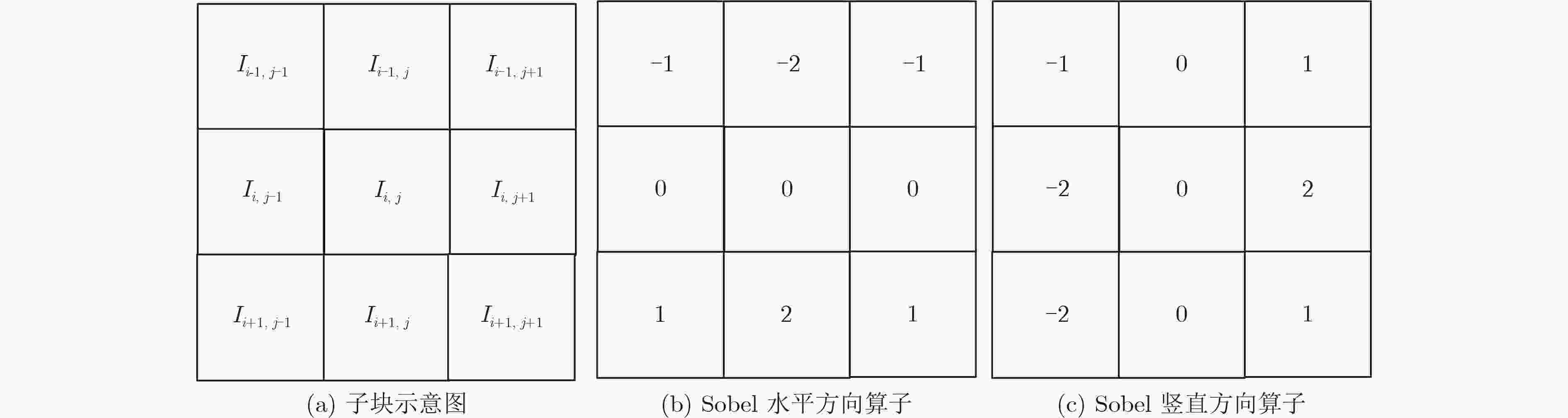
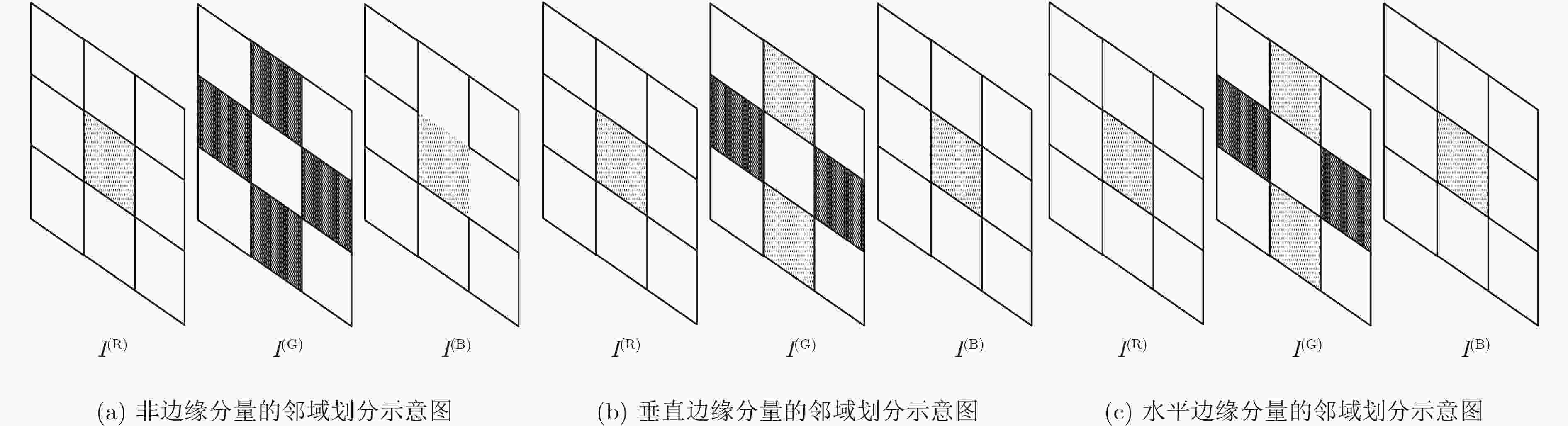
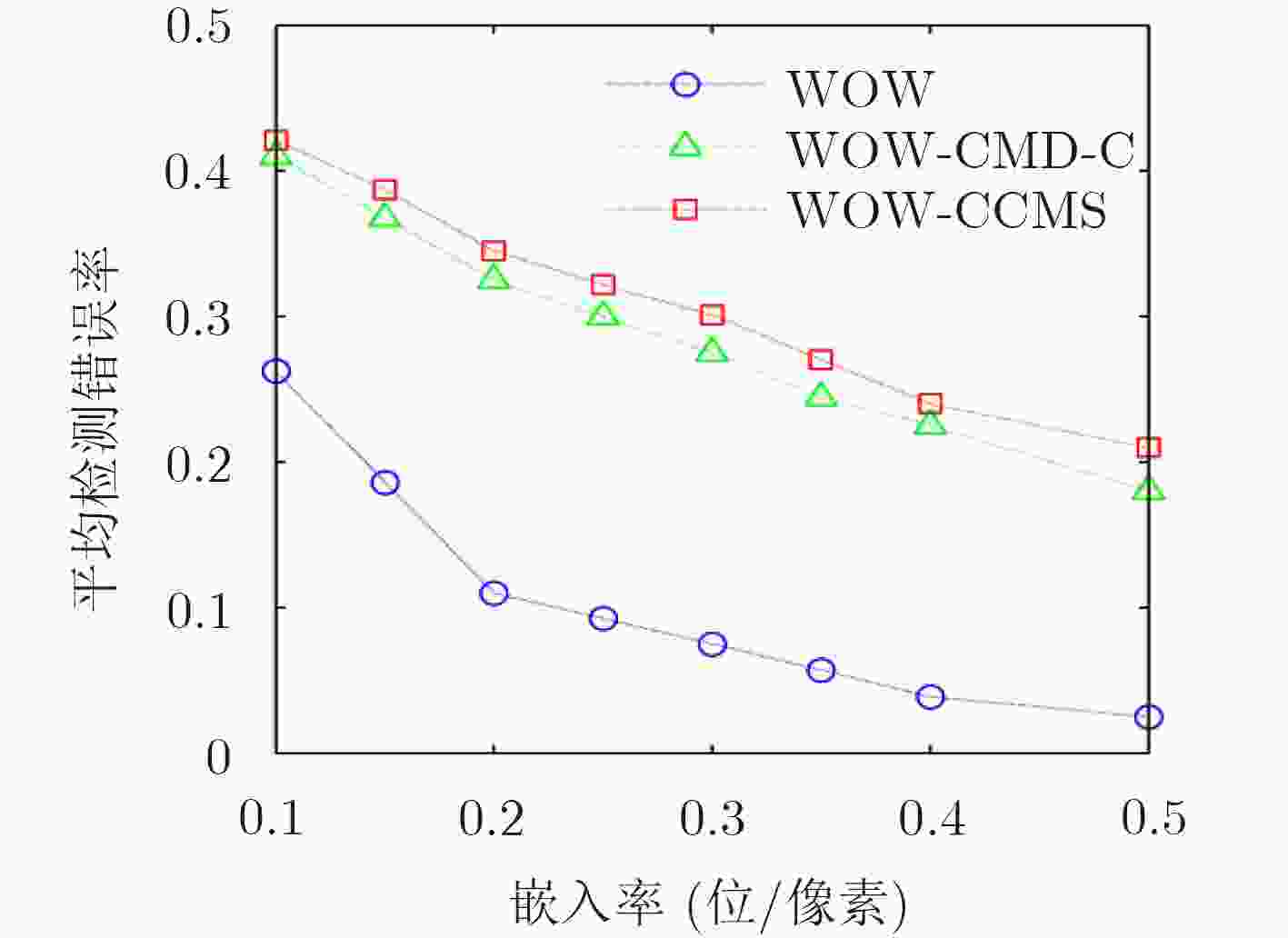
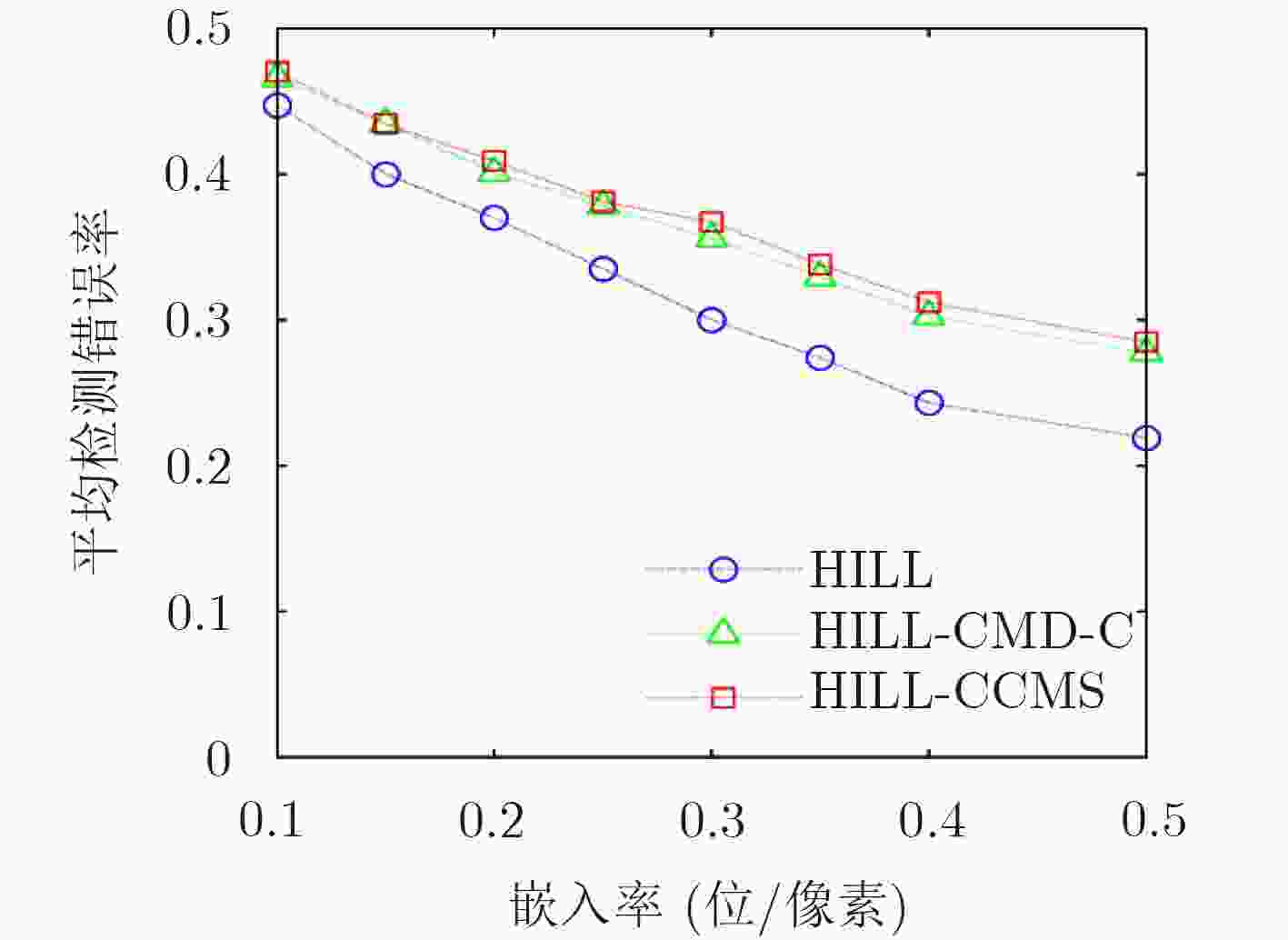
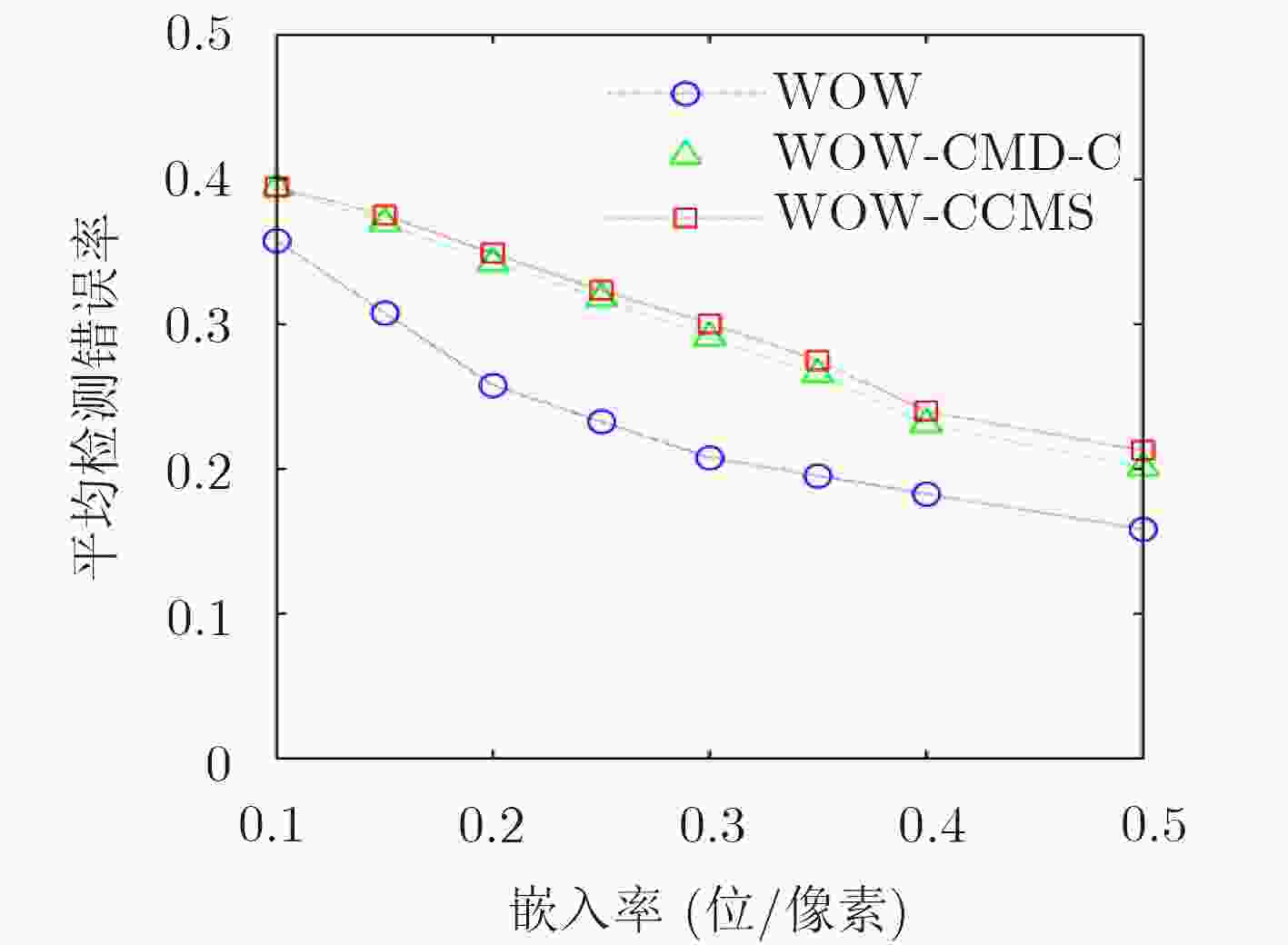



 下载:
下载:
