Robust Secure Transmission Scheme Based on Artificial Noise-aided for Heterogeneous Networks with Simultaneous Wireless Information and Power Transfer
-
摘要:
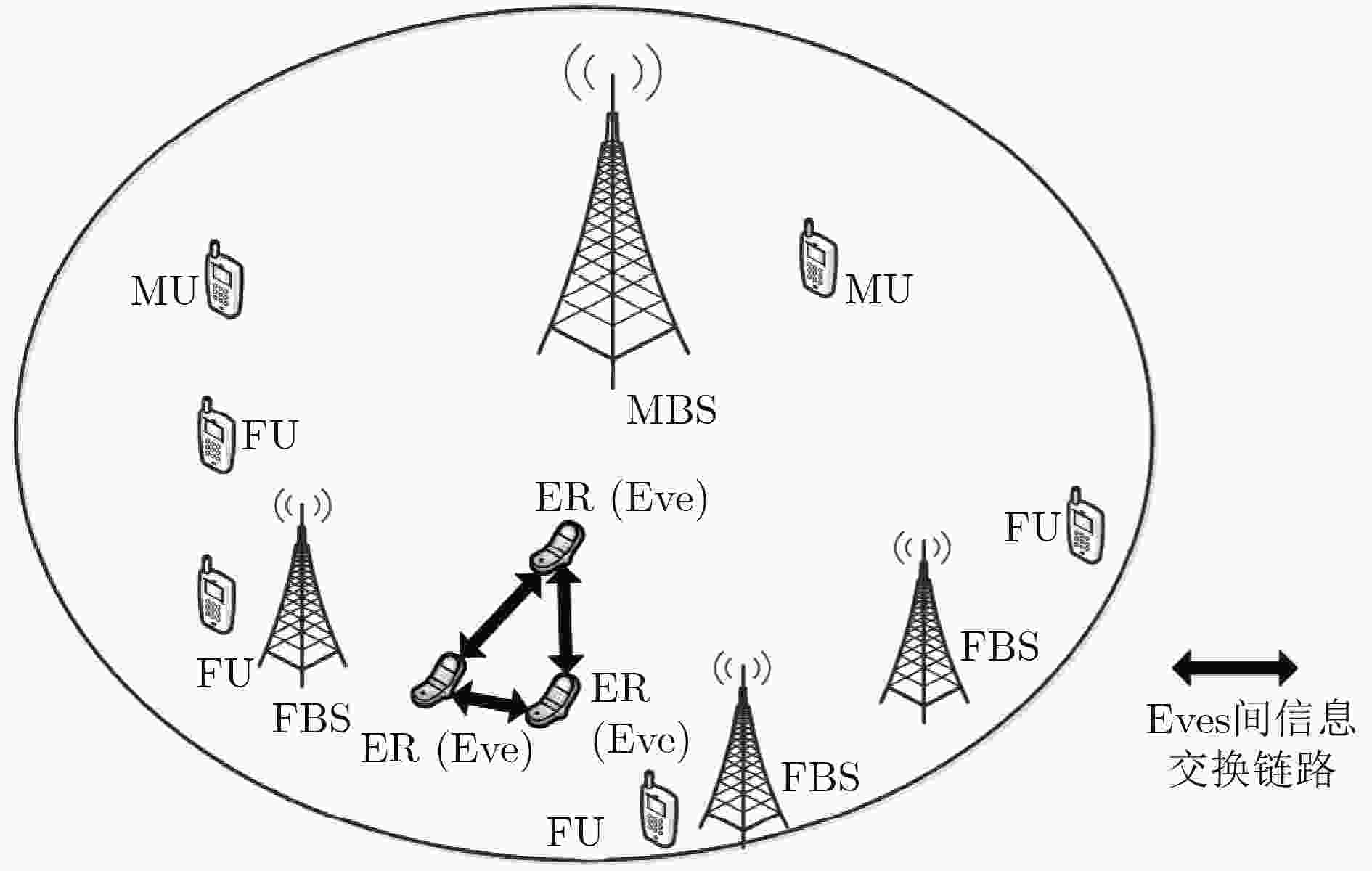
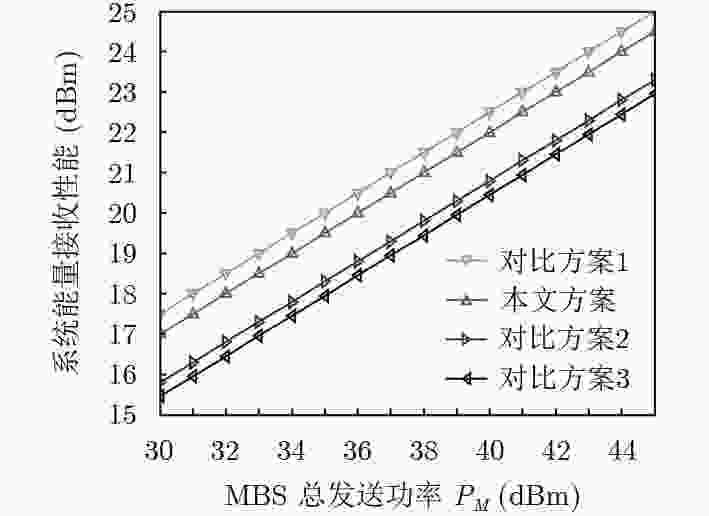
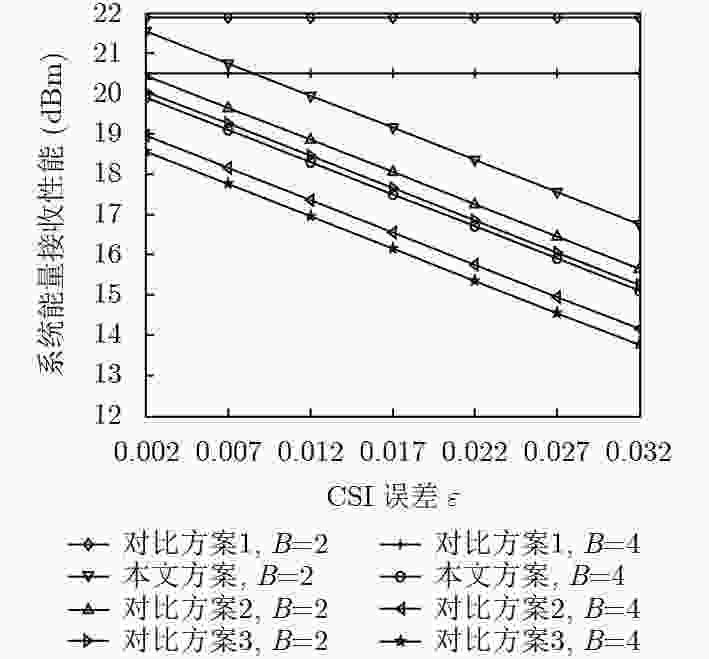
异构携能通信网络中信道状态信息不准确时,为保证信息、能量传输的安全性与可靠性,该文提出一种基于人工噪声辅助的鲁棒安全传输方案。通过联合设计宏基站、微基站的下行信息波束及人工噪声矩阵,干扰窃听者,同时提升系统能量接收性能。在基站的发送功率约束、合法用户的信息接收及能量接收中断约束和窃听者的窃听信息中断约束下,以最大化系统能量接收性能为目标进行建模。针对该问题的非凸性,首先将其等效转化为一种易于处理的形式;而后进一步利用Berstein-type不等式处理其中的中断概率约束,将其转化为凸的问题进行求解。仿真结果验证了该方案的安全性和鲁棒性。
Abstract:When the Channel State Information (CSI) is not accurate in heterogeneous networks with simultaneous wireless information and power transfer, to guarantee the security and reliability of information and energy transfer simultaneously, a robust secure transmission scheme based on Artificial Noise (AN)-aided is proposed. Through jointly designing the downlink information beamforming and AN matrix of macrocell base station and femtocell base stations, the potential eavesdroppers will be jammed, and the energy harvesting performance of system can be improved. To obtain the optimal designs, the problem of maximizing the energy harvesting performance of system is modeled under the base station power limit and the outage probability limits of information transfer, energy transfer and confidential information eavesdropped. This modeled problem is non-convex. To address the problem, it is transformed into an equivalent form, which can be processed easily. Then, the Bernstein-type inequality is utilized to deal with the outage probability limits, and it is transformed into a convex problem. Simulation results validate the security and the robustness of the proposed scheme.
-
表 1 基于人工噪声辅助的鲁棒安全传输算法
初始化:设置 $j = 0$ ,最大迭代次数

$g$ ,并随机生成可以满足式 (24)问题可行解约束的

$\mathop {{{w}_m}}\limits^ \simeq {\rm{(}}j{\rm{)}}$ ,

$\mathop {{{w}_{nk}}}\limits^ \simeq {\rm{(}}j{\rm{)}}$ ;

循环: 步骤 1 将 $\mathop {{{w}_m}}\limits^ \simeq {\rm{(}}j{\rm{)}}$ ,

$\mathop {{{w}_{nk}}}\limits^ \approx {\rm{(}}j{\rm{)}}$ 代入式(24)问题中求解,获得相应的 解

${w}_m^ * $ ,

${w}_{nk}^ * $ ;

步骤 2 更新: $j = j + 1$ ;

步骤 3 令 $\mathop {{{w}_m}}\limits^ \simeq {\rm{(}}j{\rm{) = }}{w}_m^ * $ ,

$\mathop {{{w}_{nk}}}\limits^ \simeq {\rm{(}}j{\rm{) = }}{w}_{nk}^ * $ ;

终止:直至收敛或达到最大迭代次数 $g$ ;

输出:最优的 ${w}_m^ * $ ,

${w}_{nk}^ * $ ,

${Z}_0^ * $ ,

${Z}_n^ * $ ,及系统能量接收性能值

$t$ 。

-
ZHANG Haijun, DU Jiali, and CHENG Juliang. Incomplete CSI based resource optimization in SWIPT -enabled heterogeneous networks: A non-cooperative game theoretic approach[J]. IEEE Transactions on Wireless Communications, 2018, 17(3): 1882–1892 doi: 10.1109/TWC.2017.2786255 AKBAR S and DENG Yansha. Simultaneous wireless information and power transfer in K-tier heterogeneous cellular networks[J]. IEEE Transactions on Wireless Communications, 2016, 15(8): 5804–5818 doi: 10.1109/TWC.2016.2570209 SHENG Ming, WANG Liang, and WANG Xijun. Energy efficient beamforming in MISO heterogeneous cellular networks with wireless information and power transfer[J]. IEEE Journal on Selected Areas in Communications, 2016, 34(4): 954–968 doi: 10.1109/JSAC.2016.2544538 LIU Yiliang, CHEN Hsiaohwa, and WANG Liangmin. Physical layer security for next generation wireless networks: theories, technologies, and challenges[J]. IEEE Transactions on Information Forensics and Security, 2017, 19(1): 347–376 doi: 10.1109/COMST.2016.2598968 SUN Li and DU Qinghe. Physical layer security with its applications in 5G networks: A review[J]. China Communications, 2017, 14(12): 1–14 doi: 10.1109/CC.2017.8246328 CHU Zheng, NQUYEN H X, and CAIRE G. Game theory-based resource allocation for secure WPCN multi-antenna multicasting systems[J]. IEEE Transactions on Information Forensics&Security, 2018, 13(4): 926–939 doi: 10.1109/TIFS.2017.2774441 ALEXANDER A O, MUHAMMAD R A K, WONG K K, et al. Secure full-duplex two-way relaying for SWIPT[J]. IEEE Wireless Communications Letters, 2018, 7(3): 336–339 doi: 10.1109/LWC.2017.2776928 LI Quanzhong, ZHANG Qi, and QIN Jiayin. Secure relay beamforming for SWIPT in amplify-and-forward two-way relay networks[J]. IEEE Transactions on Vehicular Technology, 2016, 65(11): 9006–9019 doi: 10.1109/TVT.2016.2519339 REN Yuan, LÜ Tiejun, GAO Hui, et al. Secure wireless information and power transfer in heterogeneous networks[J]. IEEE Access, 2017, 99(5): 4967–4979 doi: 10.1109/ACCESS.2017.2682277 LI Bin, FEI Zesong, CHU Zheng, et al. Secure transmission for heterogeneous cellular networks with wireless information and power transfer[J]. IEEE Systems Journal,Early Access, 2017 doi: 10.1109/JSYST.2017.2713881 ZHU Zhengyu and CHU Zheng. Outage constrained robust beamforming for secure broadcasting systems with energy harvesting[J]. IEEE Transactions on Wireless Communications, 2016, 15(11): 7610–7620 doi: 10.1109/TWC.2016.2605102 LE T A and VIEN Q T. Robust chance-constrained optimization for power-efficient and secure SWIPT systems[J]. IEEE Transactions on Green Communications&Networking, 2017, 1(3): 333–346 doi: 10.1109/TGCN.2017.2706063 LI Bin and FEI Zesong. Probabilistic-constrained robust secure transmission for energy harvesting over MISO channels[J]. Science China Information Sciences, 2018, 61(2): 1–12 doi: 10.1007/s11432-016-9040-x NIU Hehao and GUO Daoxin. Outage constrained robust energy harvesting maximization for secure MIMO SWIPT Systems[J]. IEEE Wireless Communications Letters, 2017, 6(5): 614–617 doi: 10.1109/LWC.2017.2722415 RASHID U, TUAN H, KHA H, et al. Joint optimization of source precoding and relay beamforming in wireless MIMO relay networks[J]. IEEE Transactions on Communications, 2014, 62(2): 488–499 doi: 10.1109/TCOMM.2013.122013.130239 ZHANG Lijian and JIN Liang. Robust secure transmission for multiuser MISO systems with probabilistic QoS constraints[J]. Science China Information Sciences, 2016, 59(2): 1–13 doi: 10.1007/s11432-015-5342-6 -





 下载:
下载:




 下载:
下载:
