Malware Sandbox Evasion Detection Based on Code Evolution
-
摘要:
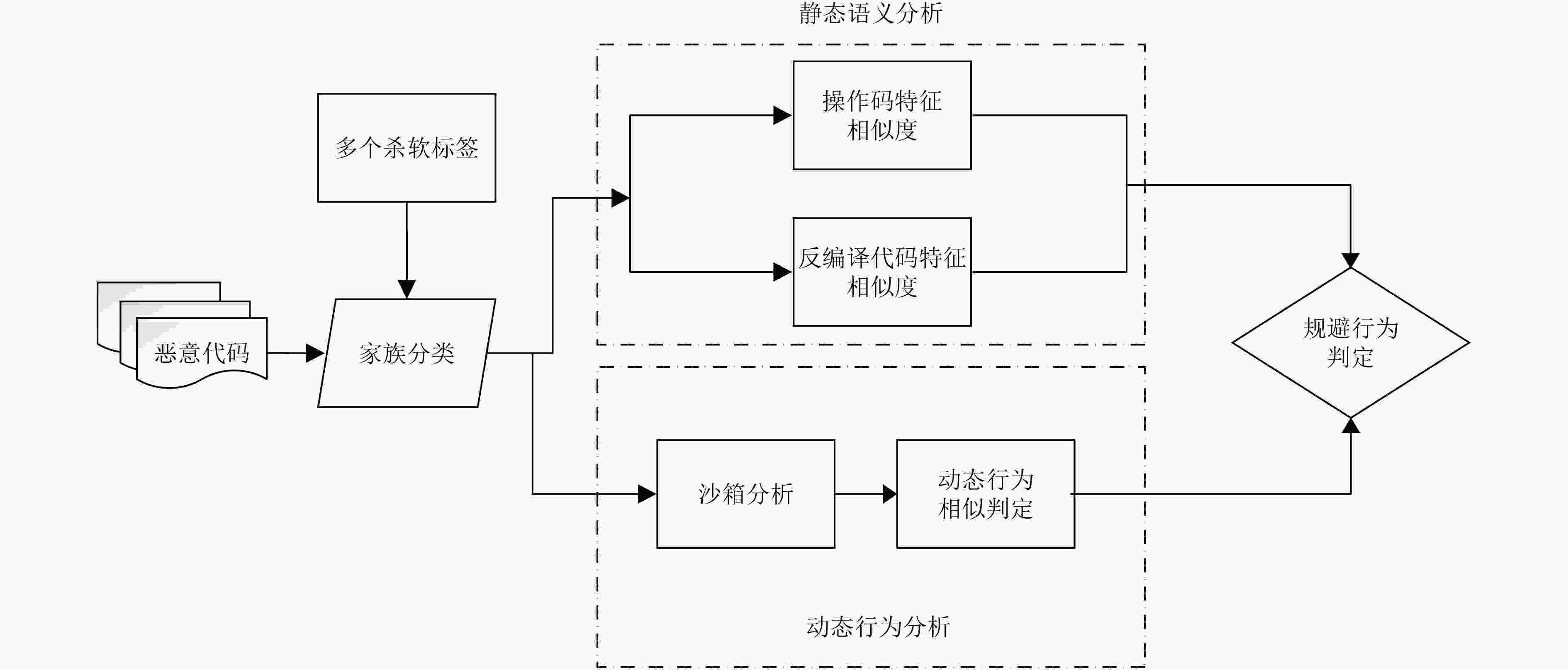
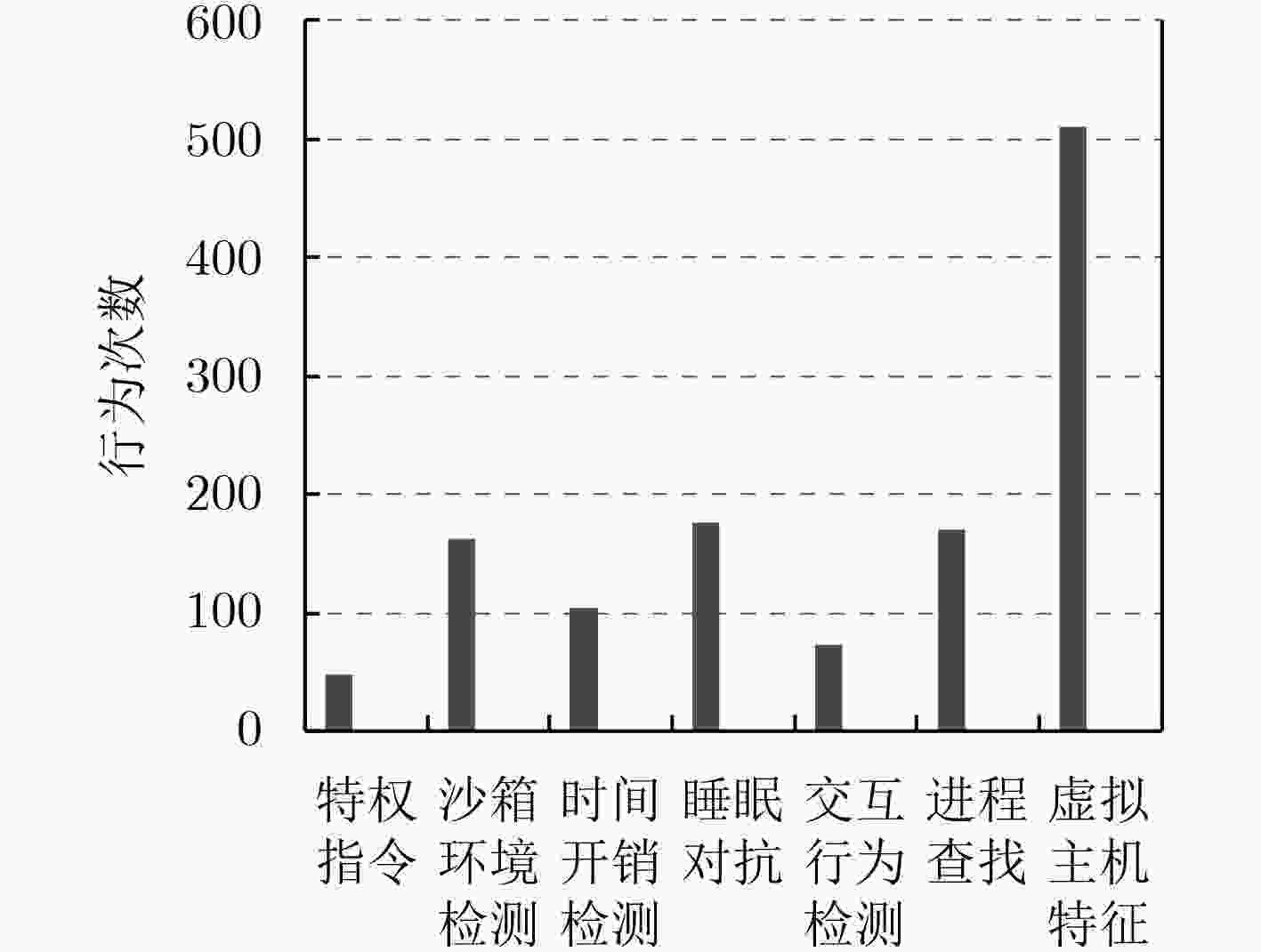
为了对抗恶意代码的沙箱规避行为,提高恶意代码的分析效率,该文提出基于代码进化的恶意代码沙箱规避检测技术。提取恶意代码的静态语义信息和动态运行时信息,利用沙箱规避行为在代码进化过程中所产生的动静态语义上的差异,设计了基于相似度差异的判定算法。在7个实际恶意家族中共检测出240个具有沙箱规避行为的恶意样本,相比于JOE分析系统,准确率提高了12.5%,同时将误报率降低到1%,其验证了该文方法的正确性和有效性。
Abstract:In order to resist the malware sandbox evasion behavior, improve the efficiency of malware analysis, a code-evolution-based sandbox evasion technique for detecting the malware behavior is proposed. The approach can effectively accomplish the detection and identification of malware by first extracting the static and dynamic features of malware software and then differentiating the variations of such features during code evolution using sandbox evasion techniques. With the proposed algorithm, 240 malware samples with sandbox-bypassing behaviors can be uncovered successfully from 7 malware families. Compared with the JOE analysis system, the proposed algorithm improves the accuracy by 12.5% and reduces the false positive to 1%, which validates the proposed correctness and effectiveness.
-
Key words:
- Malware /
- Sandbox evasion /
- Static similarity
-
表 1 沙箱规避代码进化示意
Malicious code A Evasive Malicious code B Main_behavior( ) Main_behavior( ) { { 1 Registry_opeartion( ) 1 flag = check_sandbox( ) 2 Process_injection( ) 2 if (flag == True): 3 File_compress( ) 3 do_benign( ) or exit() 4 Connection_C&C_server( ) 4 else: 5 Waiting_for_instruction( ) 5 Registry_opeartion( ) 6 File_send( ) 6 Process_injection( ) } 7 File_compress( ) 8 Connection_C&C_server( ) 9 Waiting_for_ instruction( ) 10 File_send( ) } 表 2 规避行为检测算法
For $\left( {{M_i},{M_j}} \right)$ in $C_M^2$: PS $\left( {{M_i},{M_j}} \right)$ = $\alpha $ if $\alpha < \varepsilon $: continue ${\rm PB}\left( {{M_i},{M_j}} \right) = \beta $ if $\alpha - \beta > \tau $: if ${B_i} > {B_j}$: ${M_j}$ is an evasive malware else: ${M_i}$ is an evasive malware else: No Evasion 表 3 恶意代码家族情况
家族名称 数量 时间分布 Bifrose 317 2008~2015 Dridex 57 2012~2014 Necurs 154 2011~2016 Sfone 151 2009~2016 Unruy 725 2008~2016 Urleas 57 2010~2015 Confidence 166 2011~2016 表 4 沙箱规避情况统计
家族名称 样本数量 沙箱规避样本数量 百分比(%) Bifrose 317 41 12.9 Dridex 57 22 38.5 Necurs 154 40 25.9 Sfone 151 11 7.2 Unruy 725 70 9.6 Urleas 57 30 52.6 Confidence 166 26 15.6 表 5 检测结果对比
TP TN FP FN 精度(%) TPR (%) FPR (%) F1 JOE 232 1294 52 49 81.6 82.5 3.8 0.8204 MSED 226 1331 14 56 94.1 80.1 1 0.8653 -
ANUBIS: Analyzing unknown binaries[OL]. www.anubis.iseclab.org, 2015. YIN Heng and SONG Dawn. Temu: Binary code analysis via whole-system layered annotative execution[R]. Submitted to Vee University of California, Berkeley, Tech Rep, 2010. CUCKOO Sandbox. Automated malware analysis[OL]. www.cuckoosandbox.org, 2016. RAIU C, HASBINI M, BEOLV S, et al. From Shamoon to Stonedrill-Wipers attacking Saudi organizations and beyond[R]. Kaspersky Lab, March, 2017. YOKOYAMA A, ISHII K, and TANABE R. SandPrint: Fingerprinting malware sandboxes to provide intelligence for sandbox evasion[C]. International Symposium on Research in Attacks, Intrusions, and Defenses, SudParis, France, 2016: 165–187. KIRAT D, VINGA G, and KRUEGEL C. Barebox: Efficient malware analysis on bare-metal[C]. Proceeding of the 27th Annual Computer Security Applications Conference, Orlando, USA, 2011: 403–412. CRANDALL J R, WASSERMANN G, and OLIVEIRA D A S. Temporal search: Detecting hidden malware timebombs with virtual machines[J]. ACM SIGARCH Computer Architecture News, 2006, 34(5): 25–36. doi: 10.1145/1168919 KIRAT D and VIGNA G. MalGene: Automatic extraction of malware analysis evasion signature[C]. Proceedings of the 22nd ACM SIGSAC Conference on Computer and Communications Security, Los Angeles, USA, 2015: 769–780. GILBOY M R. Fighting evasive malware with DVasion[D]. [Master dissertation], University of Maryland, College Park, 2016: 31–44. TANBE R. Evasive malware via identifier implanting[C]. International Conference on Detection of Intrusions and Malware, and Vulnerability Assessment, Pairs, France, 2018: 162–184. KRUEGEL C. Evasive malware exposed and deconstructed[C]. RSA Conference, San Francisco, USA, 2015: 112–120. MIRAMIRKHANI N, APPINI M P, and NIKIFORAKIS N. Spotless sandboxes: Evading malware analysis systems using wear-and-tear artifacts[C]. IEEE Symposium on Security and Privacy, San Jose, USA, 2017: 1009–1024. BINDIFF[OL]. www.zynamics.com/bindiff.html. 2017. 张一弛. 基于反编译的恶意代码检测关键技术研究与实现[D]. [博士论文], 解放军信息工程大学, 2009: 22–39.ZHANG Yichi. Research and Implementation of critical technology in malware detection based on decompilation[D]. [Ph.D. dissertation], PLA Information and Engineering University, 2009: 22–39. KI Y, KIM E, and KIM H. A novel approach to detect malware based on API call sequence analysis[J]. International Journal of Distributed Sensor Networks, 2015, 58(7): 3201–3206. MALWAREBENCHMARK[OL]. www.malwarebenchmark.org, 2018. JOESECURITY Sandbox[OL]. www.joesandbox.com, 2018. -





 下载:
下载:


 下载:
下载:
