Executer Synchronization in Highly Reliable Information System with Dissimilar Redundancy Architecture
-
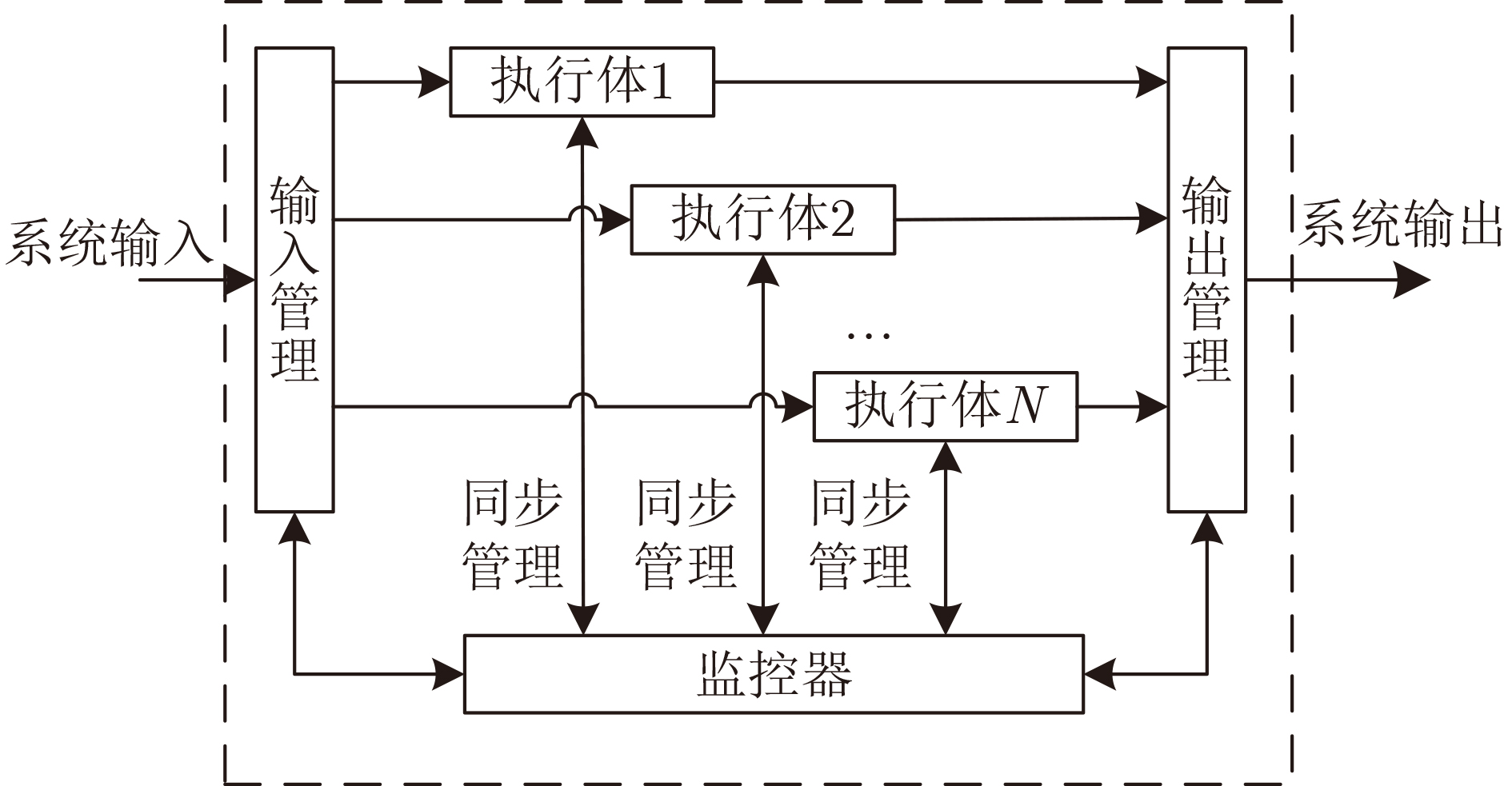
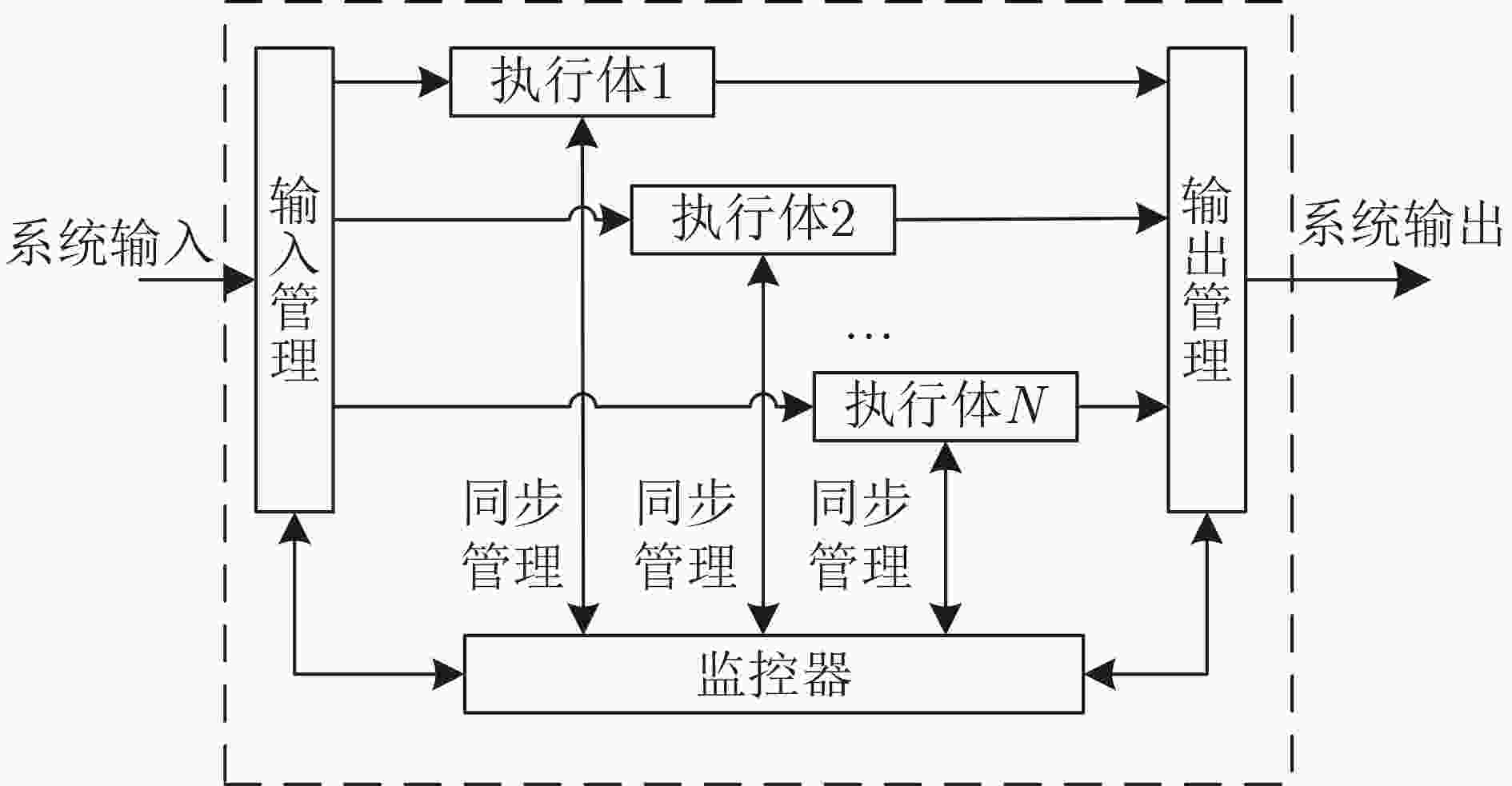
摘要: 非相似冗余架构被广泛使用到信息系统中,提高系统的安全性和可靠性。非相似冗余架构中的执行体之间存在差异,当系统正常工作时,执行体表现一致,但在面对恶意攻击行为时,执行体会表现出不一致。架构通过比较执行体的表现监控系统、感知威胁,从而提升系统安全可靠性。执行体的同步监控,是所有非相似冗余架构都需要解决的难题。目前没有针对同步技术比较系统性的描述和总结。该文首先对执行体同步问题进行了抽象建模,然后提出基于同步点的同步技术分类方法,并分别对每种技术的基本方式、流行度、优缺点进行了总结。该文还提出了影响同步效果的3个重要指标:同步点、误报率和性能,同时给出了同步技术的数学模型,可用于同步技术的设计评估。最后,结合网络弹性工程领域和软件定义晶上系统领域的发展,指出了同步技术未来的发展潜力和可能的发展方向。Abstract: Dissimilar redundancy architecture is widely used in information systems to improve their security and reliability. When the system operates normally, the executers behave consistently, but when faced with malicious attacks, the executers exhibit inconsistency. The architecture improves the security and reliability of the system by comparing the performance of the executers to monitor the system and perceive threats. The synchronization of executers is a challenge that all dissimilar redundancy architectures need to address. There is currently no systematic description and summary of synchronization technology. This article is a review of executer synchronization techniques in dissimilar redundancy architectures. First, the importance of synchronization in dissimilar redundancy systems is explained and a standardized description of synchronization is provided. Then, a synchronization technology classification method based on synchronization points is proposed and the basic process, popularity, advantages and disadvantages of each class are summarized separately. This article also proposes three important indicators that affect synchronization performance, namely synchronization point, false alarm rate, and performance, and provides a mathematical model for synchronization technology, which can be used for design evaluation. Finally, this article combines the development of cyber resilience and software defined system on wafer, pointing out the potential and possible directions for the future development of synchronous technology.
-
表 1 执行体同步技术总结
序号 架构名称 同步点 严格同步 误报率 测试集 延迟/开销 1 N-Variant[28] 系统调用 是 高 WebBench 5.0 17.8%~93.77% 2 未命名[56] 系统调用 是 高 httperf 1.2%~68.93% 3 未命名[57] 系统调用 是 低 thttpd 31%~6x 4 TightLip[29] 系统调用 是 高 SpecWeb99 5% 5 Orchestra[30] 部分系统调用 是 低 SPEC CPU2000 16% 6 GHUMVEE[31] 部分系统调用 是 低 SPEC CPU2006 15% 7 DCL[32] 部分系统调用 是 高 SPEC CPU2006 6.37% 8 ReMon[33] 规则定义的系统调用 是 低 SPEC CPU2006 3.1% 9 MvArmor[34] 规则定义的系统调用 是 低 SPEC CINT2006 9.10% 10 Bunshin[35] 规则定义的系统调用 是 低 PARSEC 8.50% 11 未命名[58] 规则定义的系统调用 是 低 PARSEC 2.1 <15% 12 DMON[36] 规则定义的系统调用 是 低 lighttpd 443% 13 HeterSec[37] 规则定义的系统调用 是 低 lighttpd 50% 14 dMVX[39] 规则定义的系统调用 可选 低 lighttpd 3.10% 15 I-MVX[59] 规则定义的系统调用
&动态链接的插桩函数是 低 SPEC CINT2006 2.13% 16 NG-MVEE[60] 部分系统调用 是 低 SPEC CPU2006 7% 17 DieHard[10] I/O 是 高 SPECint2000 12% 18 ShadowExe[43] 所有输入 是 高 Adobe reader等应用程序 >100% 19 Exterminator[42] I/O 是 低 SPECint2000 7.20% 20 BUDDY[38] I/O写&部分系统调用 是 低 SPEC CPU2006 2.34% 21 kMVX[45] I/O写&部分系统调用 是 低 nginx-1.10.1, lighttpd-1.4.48等 20%~50% 22 DHR Switch[16] 应用程序读事件
&定时器事件是 低 交换机入网测试集 <3 ms 23 DHR MCU[62] 应用输出(查询响应) 是 低 N/A N/A 24 DHR Router[21] 应用输出(路由表) 是 低 N/A N/A 25 MimicBox[63] 输出 是 高 SPECint2006 <13% 26 Detile[50] 解释器字节码 是 低 N/A 17% 27 Dual Execution[47] 指令级 是 低 N/A >2000x 28 MVX-CFI[13] 间接跳转/
调用指令&返回指令是 低 SPEC CINT2006 N/A 29 EXPERTISE[64] 内存写 是 低 MiBench ~5x 30 Varan[52] 所有系统调用 否 低 SPECint2006 14.20% 31 LDX[53] 输出 否 高 SPECint2006 4.70% 32 Respec[54] 程序段(Epoch) 否 低 PARSEC 18%~55% 33 Mx[51] 系统调用 否 N/A SPEC CPU2006 17.91% -
[1] STAMP M. Risks of monoculture[J]. Communications of the ACM, 2004, 47(3): 120. doi: 10.1145/971617.971650. [2] 王刚, 冯云, 陆世伟, 等. 多操作系统异构网络的病毒传播模型和安全性能优化策略[J]. 电子与信息学报, 2020, 42(4): 972–980. doi: 10.11999/JEIT190360.WANG Gang, FENG Yun, LU Shiwei, et al. Virus propagation model and security performance optimization strategy of multi-operating system heterogeneous network[J]. Journal of Electronics & Information Technology, 2020, 42(4): 972–980. doi: 10.11999/JEIT 190360. [3] 杜三, 舒辉, 康绯. 基于硬件的动态指令集随机化框架的设计与实现[J]. 网络与信息安全学报, 2017, 3(11): 29–39. doi: 10.11959/j.issn.2096-109x.2017.00216.DU San, SHU Hui, and KANG Fei. Design and implementation of hardware-based dynamic instruction set randomization framework[J]. Chinese Journal of Network and Information Security, 2017, 3(11): 29–39. doi: 10.11959/j.issn.2096-109x.2017.00216. [4] CHRISTOU G, VASILIADIS G, PAPAEFSTATHIOU V, et al. On architectural support for instruction set randomization[J]. ACM Transactions on Architecture and Code Optimization, 2020, 17(4): 36. doi: 10.1145/3419841. [5] 张贵民, 李清宝, 曾光裕, 等. 运行时代码随机化防御代码复用攻击[J]. 软件学报, 2019, 30(9): 2772–2790. doi: 10.13328/j.cnki.jos.005516.ZHANG Guimin, LI Qingbao, ZENG Guangyu, et al. Defensing code reuse attacks using live code randomization[J]. Journal of Software, 2019, 30(9): 2772–2790. doi: 10.13328/j.cnki.jos.005516. [6] 何红旗, 王奕森, 董卫宇, 等. 基于编译置换的指令随机化系统设计与实现[J]. 计算机应用与软件, 2017, 34(12): 313–320. doi: 10.3969/j.issn.1000-386x.2017.12.059.HE Hongqi, WANG Yisen, DONG Weiyu, et al. Design and implementation of instruction randomization based on compiling substitution[J]. Computer Applications and Software, 2017, 34(12): 313–320. doi: 10.3969/j.issn.1000-386x.2017.12.059. [7] KIL C, JUN J, BOOKHOLT C, et al. Address space layout permutation (ASLP): Towards fine-grained randomization of commodity software[C]. Proceeding of the 22nd Annual Computer Security Applications Conference, Miami Beach, USA, 2006: 339–348. doi: 10.1109/ACSAC.2006.9. [8] WANG Ye, LI Qingbao, CHEN Zhifeng, et al. Shapeshifter: Intelligence-driven data plane randomization resilient to data-oriented programming attacks[J]. Computers & Security, 2020, 89: 101679. doi: 10.1016/j.cose.2019.101679. [9] 侯尚文, 黄建军, 梁彬, 等. 一种基于实时代码装卸载的代码重用攻击防御方法[J]. 计算机科学, 2022, 49(10): 279–284. doi: 10.11896/jsjkx.220500091.HOU Shangwen, HUANG Jianjun, LIANG Bin, et al. Defense method against code reuse attack based on real-time code loading and unloading[J]. Computer Science, 2022, 49(10): 279–284. doi: 10.11896/jsjkx.220500091. [10] BERGER E D and ZORN B G. DieHard: Probabilistic memory safety for unsafe languages[C]. Proceedings of the 27th ACM SIGPLAN Conference on Programming Language Design and Implementation, Ottawa, Canada, 2006. doi: 10.1145/1133981.1134000. [11] 马博林, 张铮, 陈源, 等. 基于指令集随机化的抗代码注入攻击方法[J]. 信息安全学报, 2020, 5(4): 30–43. doi: 10.19363/J.cnki.cn10-1380/tn.2020.07.03.MA Bolin, ZHANG Zheng, CHEN Yuan, et al. The defense method for code-injection attacks based on instruction set randomization[J]. Journal of Cyber Security, 2020, 5(4): 30–43. doi: 10.19363/J.cnki.cn10-1380/tn.2020.07.03. [12] 张宇嘉, 庞建民, 张铮, 等. 基于软件多样化的拟态安全防御策略[J]. 计算机科学, 2018, 45(2): 215–221. doi: 10.11896/j.issn.1002-137X.2018.02.037.ZHANG Yujia, PANG Jianmin, ZHANG Zheng, et al. Mimic security defence strategy based on software diversity[J]. Computer Science, 2018, 45(2): 215–221. doi: 10.11896/j.issn.1002-137X.2018.02.037. [13] 姚东, 张铮, 张高斐, 等. MVX-CFI: 一种实用的软件安全主动防御架构[J]. 信息安全学报, 2020, 5(4): 44–54. doi: 10.19363/J.cnki.cn10-1380/tn.2020.07.04.YAO Dong, ZHANG Zheng, ZHANG Gaofei, et al. MVX-CFI: A practical active defense framework for software security[J]. Journal of Cyber Security, 2020, 5(4): 44–54. doi: 10.19363/J.cnki.cn10-1380/tn.2020.07.04. [14] CHEN Liming and AVIZIENIS A. N-Version programminc: A fault-tolerance approach to reliability of software operation[C]. Proceedings of the 25th International Symposium on Fault-Tolerant Computing, Pasadena, USA, 1995. doi: 10.1109/FTCSH.1995.532621. [15] 魏帅, 于洪, 顾泽宇, 等. 面向工控领域的拟态安全处理机架构[J]. 信息安全学报, 2017, 2(1): 54–73. doi: 10.19363/j.cnki.cn10-1380/tn.2017.01.005.WEI Shuai, YU Hong, GU Zeyu, et al. Architecture of mimic security processor for industry control system[J]. Journal of Cyber Security, 2017, 2(1): 54–73. doi: 10.19363/j.cnki.cn10-1380/tn.2017.01.005. [16] 宋克, 刘勤让, 魏帅, 等. 基于拟态防御的以太网交换机内生安全体系结构[J]. 通信学报, 2020, 41(5): 18–26. doi: 10.11959/j.issn.1000-436x.2020098.SONG Ke, LIU Qinrang, WEI Shuai, et al. Endogenous security architecture of Ethernet switch based on mimic defense[J]. Journal on Communications, 2020, 41(5): 18–26. doi: 10.11959/j.issn.1000-436x.2020098. [17] 王禛鹏, 扈红超, 程国振. 一种基于拟态安全防御的DNS框架设计[J]. 电子学报, 2017, 45(11): 2705–2714. doi: 10.3969/j.issn.0372-2112.2017.11.018.WANG Zhenpeng, HU Hongchao, and CHENG Guozhen. A DNS architecture based on mimic security defense[J]. Acta Electronica Sinica, 2017, 45(11): 2705–2714. doi: 10.3969/j.issn.0372-2112.2017.11.018. [18] 黄俊贤. 基于拟态防御架构的抗缓存投毒DNS系统研究[D]. [硕士论文], 华南理工大学, 2022. doi: 10.27151/d.cnki.ghnlu.2022.004792.HUANG Junxian. A research on DNS against cache poisoning based on mimic defense architecture[D]. [Master dissertation], South China University of Technology, 2022. doi: 10.27151/d.cnki.ghnlu.2022.004792. [19] 任权, 邬江兴, 贺磊. 基于GSPN的拟态DNS构造策略研究[J]. 信息安全学报, 2019, 4(2): 37–52. doi: 10.19363/J.cnki.cn10-1380/tn.2019.03.05.REN Quan, WU Jiangxing, and HE Lei. Research on mimic DNS architectural strategy based on generalized stochastic petri net[J]. Journal of Cyber Security, 2019, 4(2): 37–52. doi: 10.19363/J.cnki.cn10-1380/tn.2019.03.05. [20] 仝青, 张铮, 张为华, 等. 拟态防御Web服务器设计与实现[J]. 软件学报, 2017, 28(4): 883–897. doi: 10.13328/j.cnki.jos.005192.TONG Qing, ZHANG Zheng, ZHANG Weihua, et al. Design and implementation of mimic defense Web server[J]. Journal of Software, 2017, 28(4): 883–897. doi: 10.13328/j.cnki.jos.005192. [21] 马海龙, 伊鹏, 江逸茗, 等. 基于动态异构冗余机制的路由器拟态防御体系结构[J]. 信息安全学报, 2017, 2(1): 29–42. doi: 10.19363/j.cnki.cn10-1380/tn.2017.01.003.MA Hailong, YI Peng, JIANG Yiming, et al. Dynamic heterogeneous redundancy based router architecture with mimic defenses[J]. Journal of Cyber Security, 2017, 2(1): 29–42. doi: 10.19363/j.cnki.cn10-1380/tn.2017.01.003. [22] 马海龙, 尹梓诺, 胡涛. 面向异构化平台的轻量级程序异常检测方法[J]. 电子与信息学报, 2022, 44(2): 602–610. doi: 10.11999/JEIT210152.MA Hailong, YIN Zinuo, and HU Tao. A lightweight program anomaly detection method for heterogeneous platform[J]. Journal of Electronics & Information Technology, 2022, 44(2): 602–610. doi: 10.11999/JEIT210152. [23] MILLS B, ZNATI T, and MELHEM R. Shadow computing: An energy-aware fault tolerant computing model[C]. Proceedings of 2014 International Conference on Computing, Networking and Communications, Honolulu, USA, 2014: 73–77,doi: 10.1109/ICCNC.2014.6785308. [24] SHYE A, BLOMSTEDT J, MOSELEY T, et al. PLR: A software approach to transient fault tolerance for multicore architectures[J]. IEEE Transactions on Dependable and Secure Computing, 2009, 6(2): 135–148. doi: 10.1109/TDSC.2008.62. [25] ITURBE X, VENU B, OZER E, et al. The arm triple core lock-step (TCLS) processor[J]. ACM Transactions on Computer Systems, 2018, 36(3): 7. doi: 10.1145/3323917. [26] SALAMA A, BINNIG C, KRASKA T, et al. Cost-based fault-tolerance for parallel data processing[C]. Proceedings of the 2015 ACM SIGMOD International Conference on Management of Data, Melbourne, Australia, 2015: 285–297. doi: 10.1145/2723372.2749437. [27] JAYASEKARA S, HARWOOD A, and KARUNASEKERA S. A utilization model for optimization of checkpoint intervals in distributed stream processing systems[J]. Future Generation Computer Systems, 2020, 110: 68–79. doi: 10.1016/j.future.2020.04.019. [28] COX B and EVANS D. N-Variant systems: A secretless framework for security through diversity[C]. Proceedings of the 15th USENIX Security Symposium, Vancouver, Canada, 2006: 105–120. [29] YUMEREFENDI A R, MICKLE B, and COX L P. TightLip: Keeping applications from spilling the beans[C]. Proceedings of the 4th Symposium on Networked Systems Design and Implementation, Cambridge, USA, 2007: 25–31. [30] SALAMAT B, JACKSON T, GAL A, et al. Orchestra: Intrusion detection using parallel execution and monitoring of program variants in user-space[C]. Proceedings of the 4th ACM European Conference on Computer Systems, Nuremberg, Germany, 2009. doi: 10.1145/1519065.1519071. [31] VOLCKAERT S, DE SUTTER B, DE BAETS T, et al. GHUMVEE: Efficient, effective, and flexible replication[C]. Proceedings of the 15th International Symposium on Foundations and Practice of Security, Montreal, Canada, 2013. doi: 10.1007/978-3-642-37119-6_17. [32] VOLCKAERT S, COPPENS B, and DE SUTTER B. Cloning your gadgets: Complete ROP attack immunity with multi-variant execution[J]. IEEE Transactions on Dependable and Secure Computing, 2016, 13(4): 437–450. doi: 10.1109/TDSC.2015.2411254. [33] VOLCKAERT S, COPPENS B, VOULIMENEAS A, et al. Secure and efficient application monitoring and replication[C]. Proceedings of the 2016 USENIX Conference on Usenix Annual Technical Conference, Denver, USA, 2016: 167–179. [34] KONING K, BOS H, and GIUFFRIDA C. Secure and efficient multi-variant execution using hardware-assisted process virtualization[C]. Proceedings of the 46th Annual IEEE/IFIP International Conference on Dependable Systems and Networks, Toulouse, France, 2016: 431–442. doi: 10.1109/DSN.2016.46. [35] XU Meng, LU Kangjie, KIM T, et al. Bunshin: Compositing security mechanisms through diversification[C]. Proceedings of the 2017 USENIX Conference on Usenix Annual Technical Conference, Santa Clara, United States, 2017. [36] VOULIMENEAS A, SONG D, PARZEFALL F, et al. DMON: A distributed heterogeneous n-variant system[EB/OL].https://arxiv.org/abs/1903.03643, 2019. [37] WANG Xiaoguang, YEOH S, LYERLY R, et al. A framework to secure applications with ISA heterogeneity[C]. Proceedings of the SFMA Workshop’19, Dresden, Germany, 2019. [38] LU Kangjie, XU Meng, SONG Chengyu, et al. Stopping memory disclosures via diversification and replicated execution[J]. IEEE Transactions on Dependable and Secure Computing, 2021, 18(1): 160–173. doi: 10.1109/TDSC.2018.2878234. [39] VOULIMENEAS A, SONG D, LARSEN P, et al. dMVX: Secure and efficient multi-variant execution in a distributed setting[C]. Proceedings of the 14th European Workshop on Systems Security, United Kingdom, 2021. doi: 10.1145/3447852.3458714. (查阅网上资料,未找到对应的出版城市信息,请确认) .VOULIMENEAS A, SONG D, LARSEN P, et al. dMVX: Secure and efficient multi-variant execution in a distributed setting[C]. Proceedings of the 14th European Workshop on Systems Security, United Kingdom, 2021. doi: 10.1145/3447852.3458714. (查阅网上资料,未找到对应的出版城市信息,请确认). [40] BERGER E D and ZORN B G. DieHard: Efficient probabilistic memory safety[J]. ACM Transactions on Computers, 2007. (查阅网上资料, 未找到对应的卷期页码信息, 请确认) .BERGER E D and ZORN B G. DieHard: Efficient probabilistic memory safety[J]. ACM Transactions on Computers, 2007. (查阅网上资料, 未找到对应的卷期页码信息, 请确认). [41] NOVARK G and BERGER E D. DieHarder: Securing the heap[C]. Proceedings of the 17th ACM Conference on Computer and Communications Security, Chicago, USA, 2010. doi: 10.1145/1866307.1866371. [42] NOVARK G, BERGER E D, and ZORN B G. Exterminator: Automatically correcting memory errors with high probability[J]. Communications of the ACM, 2008, 51(12): 87–95. doi: 10.1145/1409360.1409382. [43] CAPIZZI R, LONGO A, VENKATAKRISHNAN V N, et al. Preventing information leaks through shadow executions[C]. Proceedings of 2008 Annual Computer Security Applications Conference, Anaheim, USA, 2008: 102–110. doi: 10.1109/ACSAC.2008.50. [44] RICHARDSON T, STAFFORD-FRASER Q, WOOD K R, et al. Virtual network computing[J]. IEEE Internet Computing, 1998, 2(1): 33–38. doi: 10.1109/4236.656066. [45] ÖSTERLUND S, KONING K, OLIVIER P, et al. kMVX: Detecting kernel information leaks with multi-variant execution[C]. Proceedings of the Twenty-Fourth International Conference on Architectural Support for Programming Languages and Operating Systems, Providence, USA, 2019: 559–572. doi: 10.1145/3297858.3304054. [46] 苏野, 魏帅, 姚领彦, 等. 基于相对时间的异构执行体程序状态同步方法[C]. 第三届“先进计算与内生安全”学术会议论文集, 南京, 中国, 2020: 716–725. (查阅网上资料, 未找到对应的英文翻译, 请确认) .SU Ye, WEI Shuai, YAO Lingyan, et al. Program state synchronization method of heterogeneous executors based on relative time[C]. Proceedings of the 3rd Conference on Advanced Computing and Endogenous Safety & Security, Nanjing, China, 2020: 716–725. [47] KIM D, KWON Y, SUMNER W N, et al. Dual execution for on the fly fine grained execution comparison[C]. Proceedings of the Twentieth International Conference on Architectural Support for Programming Languages and Operating Systems, Istanbul, Turkey, 2015: 325–338. doi: 10.1145/2694344.2694394. [48] XIN Bin, SUMNER W N, and ZHANG Xiangyu. Efficient program execution indexing[C]. Proceedings of the 29th ACM SIGPLAN Conference on Programming Language Design and Implementation, Tucson, USA, 2008: 238–248. doi: 10.1145/1375581.1375611. [49] KIM D, SUMNER W N, ZHANG Xiangyu, et al. Reuse-oriented reverse engineering of functional components from x86 binaries[C]. Proceedings of the 36th International Conference on Software Engineering, Hyderabad, India, 2014: 1128–1139. doi: 10.1145/2568225.2568296. [50] GAWLIK R, KOPPE P, KOLLENDA B, et al. Detile: Fine-grained information leak detection in script engines[C]. Proceedings of the 13th International Conference on Detection of Intrusions and Malware, and Vulnerability Assessment, San Sebastián, Spain, 2016: 322–342. doi: 10.1007/978-3-319-40667-1_16. [51] HOSEK P and CADAR C. Safe software updates via multi-version execution[C]. Proceedings of 2013 35th International Conference on Software Engineering, San Francisco, USA, 2013: 612–621. doi: 10.1109/ICSE.2013.6606607. [52] HOSEK P and CADAR C. VARAN the unbelievable: An efficient N-version execution framework[C]. Proceedings of the 20th International Conference on Architectural Support for Programming Languages and Operating Systems, Istanbul, Turkey, 2015. doi: 10.1145/2694344.2694390. [53] KWON Y, KIM D, SUMNER W N, et al. LDX: Causality inference by lightweight dual execution[C]. Proceedings of the 21st International Conference on Architectural Support for Programming Languages and Operating Systems, Atlanta, USA, 2016. doi: 10.1145/2872362.2872395. [54] LEE D, WESTER B, VEERARAGHAVAN K, et al. Respec: Efficient online multiprocessor replayvia speculation and external determinism[J]. ACM SIGARCH Computer Architecture News, 2010, 38(1): 77–90. doi: 10.1145/1735970.1736031. [55] XU Jun, GUO Pinyao, CHEN Bo, et al. Demo: A symbolic n-variant system[C]. Proceedings of the 2016 ACM Workshop on Moving Target Defense, Vienna, Austria, 2016. doi: 10.1145/2995272.2995284. [56] BRUSCHI D, CAVALLARO L, and LANZI A. Diversified process replicæ for defeating memory error exploits[C]. Proceedings of 2007 IEEE International Performance, Computing, and Communications Conference, New Orleans, USA, 2007. doi: 10.1109/PCCC.2007.358924. [57] CAVALLARO L. Comprehensive memory error protection via diversity and taint-tracking[D]. [Ph. D. dissertation], Università Degli Studi di Milano, 2007. [58] VOLCKAERT S, COPPENS B, DE SUTTER B, et al. Taming parallelism in a multi-variant execution environment[C]. Proceedings of the Twelfth European Conference on Computer Systems, Belgrade, Serbia, 2017. doi: 10.1145/3064176.3064178. [59] 李秉政, 张铮, 马博林, 等. 编译支持的多变体融合执行设计与实现[J]. 信息安全学报, 2022, 7(4): 114–123. doi: 10.19363/J.cnki.cn10-1380/tn.2022.07.09.LI Bingzheng, ZHANG Zheng, MA Bolin, et al. Design and implementation of integrated multi-variant execution supported by compiler[J]. Journal of Cyber Security, 2022, 7(4): 114–123. doi: 10.19363/J.cnki.cn10-1380/tn.2022.07.09. [60] EL-ZOGHBY A M, ELSAYED M S, JURCUT A D, et al. NG-MVEE: A new proposed hybrid technique for enhanced mitigation of code re-use attack[J]. IEEE Access, 2023, 11: 48169–48191. doi: 10.1109/ACCESS.2023.3269881. [61] DE GROEF W, DEVRIESE D, NIKIFORAKIS N, et al. Secure multi-execution of web scripts: Theory and practice[J]. Journal of Computer Security, 2014, 22(4): 469–509. doi: 10.3233/JCS-130495. [62] 张明权, 于洪, 魏帅, 等. 基于拟态的MCU设计及应用验证[C]. 第三届先进计算与内生安全学术会议论文集, 南京, 中国, 2020: 299–305. (查阅网上资料, 未找到本条文献信息, 请确认) .ZHANG Mingquan, YU Hong, WEI Shuai, et al. MCU design and application verification based on mimic defense[C]. Proceedings of the 3rd Conference on Advanced Computing and Endogenous Safety & Security, Nanjing, China, 2020: 299–305. [63] 潘传幸, 张铮, 马博林, 等. 面向进程控制流劫持攻击的拟态防御方法[J]. 通信学报, 2021, 42(1): 37–47. doi: 10.11959/j.issn.1000-436x.2021013.PAN Chuanxing, ZHANG Zheng, MA Bolin, et al. Method against process control-flow hijacking based on mimic defense[J]. Journal on Communications, 2021, 42(1): 37–47. doi: 10.11959/j.issn.1000-436x.2021013. [64] SO H, DIDEHBAN M, KO Y, et al. EXPERTISE: An effective software-level redundant multithreading scheme against hardware faults[J]. ACM Transactions on Architecture and Code Optimization, 2022, 19(4): 53. doi: 10.1145/3546073. [65] 姚远, 潘传幸, 张铮, 等. 多样化软件系统量化评估方法[J]. 通信学报, 2020, 41(3): 120–125. doi: 10.11959/j.issn.1000-436x.2020051.YAO Yuan, PAN Chuanxing, ZHANG Zheng, et al. Method of quantitative assessment for diversified software system[J]. Journal on Communications, 2020, 41(3): 120–125. doi: 10.11959/j.issn.1000-436x.2020051. [66] DUAN Jun, HAMLEN K W, and FERRELL B. Better late than never: An n-variant framework of verification for Java source code on CPU x GPU hybrid platform[C]. Proceedings of the 28th International Symposium on High-Performance Parallel and Distributed Computing, Phoenix, USA, 2019. doi: 10.1145/3307681.3326604. [67] JONES J, HISER J D, DAVIDSON J W, et al. Defeating denial-of-service attacks in a self-managing N-variant system[J]. ACM Transactions on Software Engineering & Methodology, 2019, 28(3): 126–138. (查阅网上资料, 未找到本条文献信息, 请确认) .JONES J, HISER J D, DAVIDSON J W, et al. Defeating denial-of-service attacks in a self-managing N-variant system[J]. ACM Transactions on Software Engineering & Methodology, 2019, 28(3): 126–138. (查阅网上资料, 未找到本条文献信息, 请确认). [68] BAS F, ALCAIDE S, LORENZO R, et al. SafeDE: A flexible diversity enforcement hardware module for light-lockstepping[C]. Proceedings of 2021 IEEE 27th International Symposium on On-Line Testing and Robust System Design, Torino, Italy, 2021: 1–7. doi: 10.1109/IOLTS52814.2021.9486715. [69] BAS F, ALCAIDE S, CABO G, et al. SafeDE: A low-cost hardware solution to enforce diverse redundancy in multicores[J]. IEEE Transactions on Device and Materials Reliability, 2022, 22(2): 111–119. doi: 10.1109/TDMR.2022.3156799. [70] ZHOU Dacheng, CHEN Hongchang, CHENG Guozhen, et al. SecIngress: An API gateway framework to secure cloud applications based on n-variant system[J]. China Communications, 2021, 18(8): 17–34. doi: 10.23919/JCC.2021.08.002. [71] GOLDMAN H G. Building secure, resilient architectures for cyber mission assurance[R]. McLean: MITRE Corporation, 2010. [72] ROSS R, PILLITTERI V, GRAUBART R, et al. Developing cyber-resilient systems: A systems security engineering approach[R]. NIST Special Publication, 2021. doi: 10.6028/NIST.SP.800-160v2. (查阅网上资料,未找到对应的出版地信息,请确认) .ROSS R, PILLITTERI V, GRAUBART R, et al. Developing cyber-resilient systems: A systems security engineering approach[R]. NIST Special Publication, 2021. doi: 10.6028/NIST.SP.800-160v2. (查阅网上资料,未找到对应的出版地信息,请确认). [73] LINKOV I, LIGO A, STODDARD K, et al. Cyber efficiency and cyber resilience[J]. Communications of the ACM, 2023, 66(4): 33–37. doi: 10.1145/3549073. [74] YADAV S B. A resilient hierarchical distributed model of a cyber physical system[J]. Cyber-Physical Systems, 2023, 9(2): 97–121. doi: 10.1080/23335777.2021. 1964101. [75] 王明楠, 刘勤让, 刘冬培, 等. 一种晶上系统互连网络的容错感知结构[J]. 计算机应用研究, 2023, 40(2): 533–538 doi: 10.19734/j.issn.1001-3695.2022.06.0355.WANG Mingnan, LIU Qinrang, LIU Dongpei, et al. Fault-tolerant awareness structure for network on wafer[J]. Application Research of Computers, 2023, 40(2): 533–538 doi: 10.19734/j.issn.1001-3695.2022.06.0355. -





 下载:
下载: