Privacy Preseving Attribute Based Searchable Encryption Scheme in Intelligent Transportation System
-
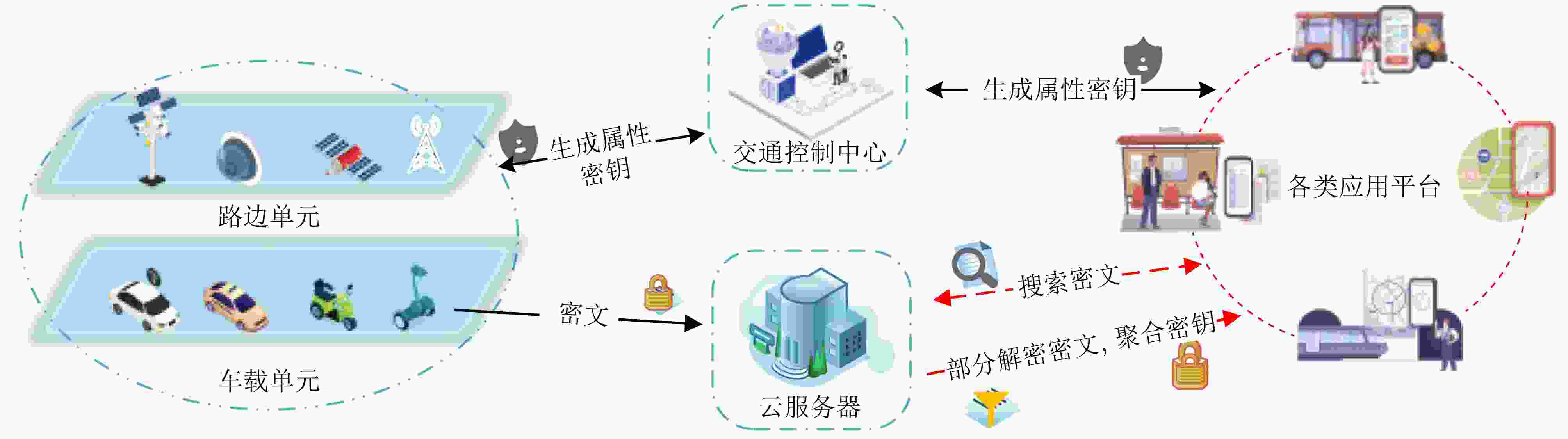
摘要: 针对智能交通系统(ITS)中车载用户出行信息容易被非法盗用、交通系统云端服务器存储的交通数据被恶意用户非法滥用等问题,该文提出一种新的属性基可搜索加密(ABSE)方案,该方案具有隐私保护、密钥聚合和轻量计算等功能。该方案在密钥生成阶段、访问控制阶段和部分解密阶段实现了全隐私保护;将搜索关键字嵌入到访问结构中,在实现部分策略隐藏的同时保证了关键字安全;通过密钥聚合技术,将所有满足搜索条件和访问策略的文件标识聚合成一个聚合密钥,减轻用户的密钥存储负担,保障文件密钥安全的同时进一步保障了数据安全。安全性分析表明,该方案具有隐藏访问结构安全、关键字密文不可区分安全和陷门不可区分安全。理论分析和数值模拟显示所提方案在通信和计算方面的开销是高效且实用的。Abstract: In order to solve the problem that the travel information of vehicle users in Intelligent Transportation System (ITS) is easy to be illegally stolen and the traffic data stored in the cloud server of transportation system is abused by malicious users, a new Attribute Based Searchable Encryption (ABSE) scheme is proposed in this paper, which has the functions of privacy protection, key aggregation and lightweight calculation. The scheme realizes full privacy protection in key generation stage, access control stage and partial decryption stage. The search keyword is embedded into the access structure, which can realize partial policy hiding and keyword security. Through key aggregation technology, all file identities that meet the search conditions and access policies are aggregated into one aggregate key, which reduces the burden of key storage for users, and further ensures the security of file keys and data. The security analysis shows that the scheme has the advantages of hidden access structure security, keyword ciphertext indistinguishable security and trapdoor indistinguishable security. The theoretical analysis and numerical simulation showed the proposed scheme was efficient and practical in terms of communication and computing overhead.
-
表 1 功能比较
表 2 用户端的通信量分析
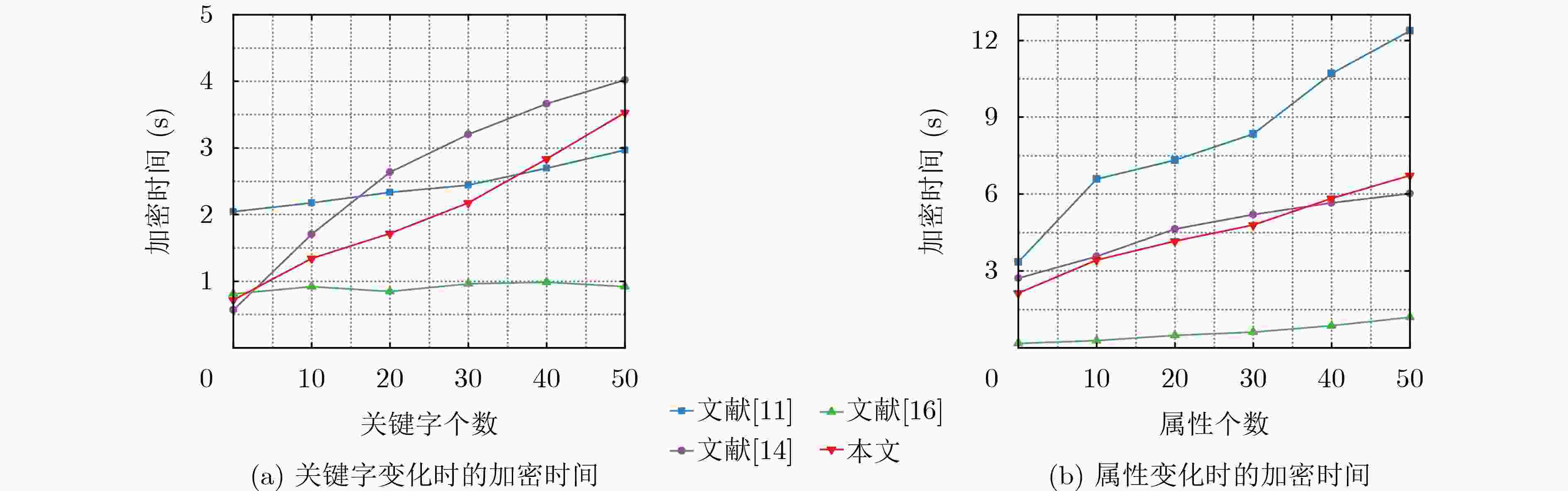
方案 加密阶段 陷门生成阶段 解密阶段 文献[11] $ (2{\text{ + }}n{\text{ + }}u)|{Z_p}|{\text{ + }}(1{\text{ + }}l{\text{ + }}3n{\text{ + }}3u)|{G_1}|{\text{ + }}(u{\text{ + }}n)|{G_2}|{\text{ + }}n|H| $ $|{Z_p}|{\text{ + }}3|{G_1}|{\text{ + }}u|{G_2}|$ $ n'|{Z_p}|{\text{ + }}n'|{G_2}|{\text{ + }}n'l|H| $ 文献[14] $(u{\text{ + }}1)n|{Z_p}|{\text{ + }}(2u{\text{ + }}3)n|{G_1}|{\text{ + }}(2{\text{ + }}u)n|{G_2}|$ $(u{\text{ + }}1)|{G_1}|$ $un'|{G_1}|{\text{ + }}2n'|{G_2}|$ 文献[16] $(3u{\text{ + }}3)n|{Z_p}|{\text{ + }}(4{\text{ + }}u)n|{G_1}|{\text{ + }}2n|{G_2}|$ $(3{\text{ + }}u)|{Z_p}|{\text{ + }}2|{G_1}|{\text{ + }}|{G_2}|$ $ n'|{G_2}| $ 本文 $|{Z_p}|{\text{ + }}(5{\text{ + }}l)|{G_1}|{\text{ + }}(l{\text{ + }}n)|{G_2}|{\text{ + }}|(M,\pi )|$ $(2u{\text{ + }}l)|{G_1}|$ $n'|{G_1}|$ 表 3 终端设备加密文件计算量分析
方案 计算量 文献[11] $(l+3+u){{{T}}_{\text{h}}}+(2+u){{{T}}_{\text{m}}}+(7+l+4u){{{T}}_{\text{e}}}+(1+u){{{T}}_{\text{p}}}$ 文献[14] $(l+u){{{T}}_{\text{h}}}+(2+u+l){{{T}}_{\text{m}}}+(6+2l+u){{{T}}_{\text{e}}}+l{{{T}}_{\text{p}}}$ 文献[16] $2u{{{T}}_{\text{h}}}+(1+2u){{{T}}_{\text{m}}}+(7+3u){{{T}}_{\text{e}}}+2{{{T}}_{\text{p}}}$ 本文 $u{{{T}}_{\text{h}}}+(2u+l+4){{{T}}_{\text{e}}}+l{{{T}}_{\text{p}}}$ 表 4 用户端生成陷门与解密计算量分析
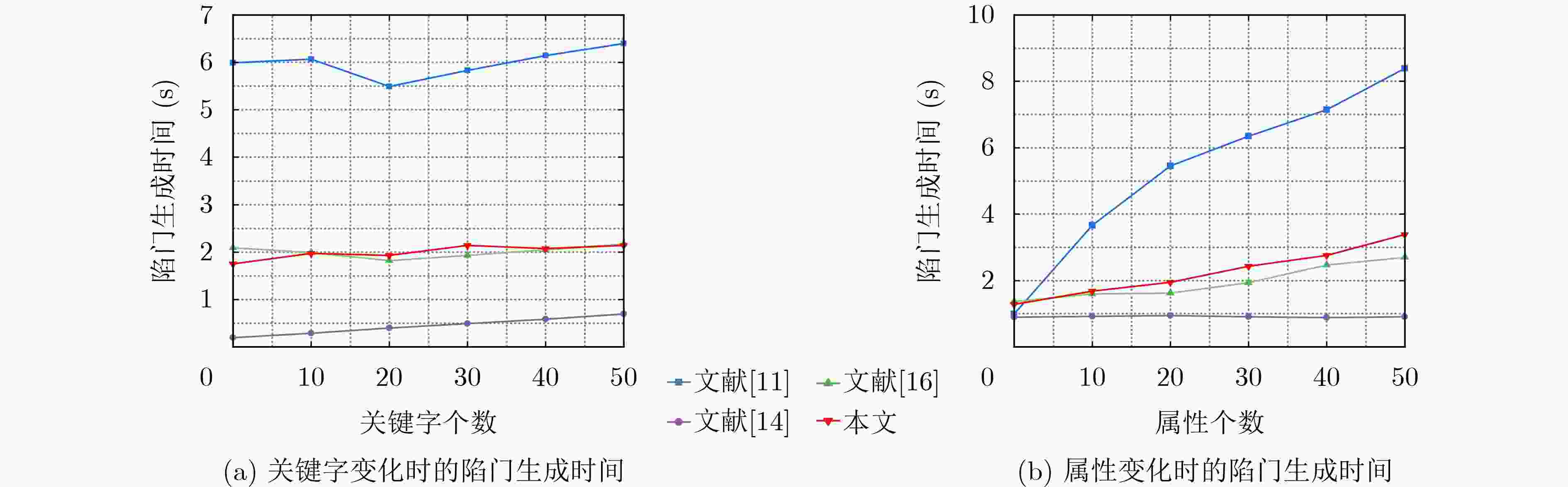
方案 生成陷门 解密 文献[11] $(2l-2){{{T}}_{\text{a}}}+u{{{T}}_{\text{h}}}+2{{{T}}_{\text{m}}}+(3+u){{{T}}_{\text{e}}}+u{{{T}}_{\text{p}}}$ ${{{T}}_{\text{h}}}+{{{T}}_{\text{m}}}+{{{T}}_{\text{e}}}$ 文献[14] $ l{{{T}}_{\text{h}}}+(l+1){{{T}}_{\text{m}}}+{{{T}}_{\text{e}}} $ $2u{{{T}}_{\text{h}}}+u{{{T}}_{\text{m}}}+2u{{{T}}_{\mathrm{e}}}+(2u+1){{{T}}_{\text{p}}}$ 文献[16] $(u{\text{ + }}1){{{T}}_{\text{a}}}+u{{{T}}_{\text{h}}}+3{{{T}}_{\text{m}}}+(3+u){{{T}}_{\text{e}}}+{{{T}}_{\text{p}}}$ ${{{T}}_{\text{m}}}+{{{T}}_{\text{e}}}$ 本文 $(u{\text{ + }}l){{{T}}_{\text{h}}}{\text{ + }}(u{\text{ + }}l){{{T}}_{\text{m}}}{\text{ + }}{{{T}}_{\text{e}}}$ $ {{{T}}_{\text{m}}}+{{{T}}_{\text{e}}}+{{{T}}_{\text{p}}} $ -
[1] ARTHURS P, GILLAM L, KRAUSE P, et al. A taxonomy and survey of edge cloud computing for intelligent transportation systems and connected vehicles[J]. IEEE Transactions on Intelligent Transportation Systems, 2022, 23(7): 6206–6221. doi: 10.1109/TITS.2021.3084396. [2] ÇELIK Y, AYDIN M M, PETRI L, et al. Intelligent transportation systems applications: Safety and transfer of big transport data[C]. The 13th International Conference TRANSBALTICA, Vilnius, Lithuania, 2022: 59–73. doi: 10.1007/978-3-031-25863-3_6. [3] YU Miao. Construction of regional intelligent transportation system in smart city road network via 5G network[J]. IEEE Transactions on Intelligent Transportation Systems, 2023, 24(2): 2208–2216. doi: 10.1109/TITS.2022.3141731. [4] JIANG Shan, CAO Jiannong, WU Hanqing, et al. Privacy-preserving and efficient data sharing for blockchain-based intelligent transportation systems[J]. Information Sciences, 2023, 635: 72–85. doi: 10.1016/j.ins.2023.03.121. [5] ZHOU Zhili, GAURAV A, GUPTA B B, et al. A fine-grained access control and security approach for intelligent vehicular transport in 6G communication system[J]. IEEE Transactions on Intelligent Transportation Systems, 2022, 23(7): 9726–9735. doi: 10.1109/TITS.2021.3106825. [6] SONG D X, WAGNER D, and PERRIG A. Practical techniques for searches on encrypted data[C]. Proceeding of 2000 IEEE Symposium on Security and Privacy, Berkeley, USA, 2000: 44–55. doi: 10.1109/SECPRI.2000.848445. [7] ZHENG Kaifa, WANG Na, LIU Jianwei, et al. An efficient multikeyword fuzzy ciphertext retrieval scheme based on distributed transmission for Internet of Things[J]. International Journal of Intelligent Systems, 2022, 37(10): 7419–7443. doi: 10.1002/int.22886. [8] LI Xinghua, TONG Qiuyun, ZHAO Jinwei, et al. VRFMS: Verifiable ranked fuzzy multi-keyword search over encrypted data[J]. IEEE Transactions on Services Computing, 2023, 16(1): 698–710. doi: 10.1109/TSC.2021.3140092. [9] ZHANG Hua, ZHAO Shaohua, GUO Ziqing, et al. Scalable fuzzy keyword ranked search over encrypted data on hybrid clouds[J]. IEEE Transactions on Cloud Computing, 2023, 11(1): 308–323. doi: 10.1109/TCC.2021.3092358. [10] KAUSHIK K, VARADHARAJAN V, and NALLUSAMY R. Multi-user attribute based searchable encryption[C]. The 2013 IEEE 14th International Conference on Mobile Data Management, Milan, Italy, 2013: 200–205. doi: 10.1109/MDM.2013.94. [11] LIU Xueyan, LU Tingting, HE Xiaomei, et al. Verifiable attribute-based keyword search over encrypted cloud data supporting data deduplication[J]. IEEE Access, 2020, 8: 52062–52074. doi: 10.1109/ACCESS.2020.2980627. [12] SUN Jianfei, HU Shengnan, and NIE Xuyun. Fine-grained ranked multi-keyword search over hierarchical data for IoT-oriented health system[J]. IEEE Access, 2019, 7: 101969–101980. doi: 10.1109/ACCESS.2019.2928441. [13] LAI Junzuo, ZHOU Xuhua, DENG R H, et al. Expressive search on encrypted data[C]. The 8th ACM SIGSAC Symposium on Information, Computer and Communications Security, New York, USA, 2013: 243–252. doi: 10.1145/2484313.2484345. [14] ZHOU Yunhong, NAN Jiehui, and WANG Licheng. Fine-grained attribute-based multikeyword search for shared multiowner in internet of things[J]. Security and Communication Networks, 2021, 2021: 6649119. doi: 10.1155/2021/6649119. [15] ZHAO Zhiyuan, SUN Lei, LI Zuohui, et al. Searchable ciphertext-policy attribute-based encryption with multi-keywords for secure cloud storage[C]. The 2018 International Conference on Computing and Pattern Recognition, Shenzhen, China, 2018: 35–41. doi: 10.1145/3232829.3232844. [16] ZHANG Ke, LONG Jiahuan, WANG Xiaofen, et al. Lightweight searchable encryption protocol for industrial internet of things[J]. IEEE Transactions on Industrial Informatics, 2021, 17(6): 4248–4259. doi: 10.1109/TII.2020.3014168. [17] LIU Xueyan, YANG Xiaotao, LUO Yukun, et al. Verifiable multikeyword search encryption scheme with anonymous key generation for medical internet of things[J]. IEEE Internet of Things Journal, 2022, 9(22): 22315–22326. doi: 10.1109/JIOT.2021.3056116. [18] GREEN M, HOHENBERGER S, and WATERS B. Outsourcing the decryption of ABE ciphertexts[C]. The 20th USENIX Conference on Security, San Francisco, USA, 2011: 34. doi: 10.5555/2028067.2028101. [19] CANETTI R, KRAWCZYK H, and NIELSEN J B. Relaxing chosen-ciphertext security[C]. The 23rd Annual International Cryptology Conference, Santa Barbara, USA, 2003: 565–582. doi: 10.1007/978-3-540-45146-4_33. [20] HOHENBERGER S and WATERS B. Online/offline attribute-based encryption[C]. The 17th International Conference on Practice and Theory in Public-Key Cryptography, Buenos Aires, Argentina, 2014: 293–310. doi: 10.1007/978-3-642-54631-0_17. -





 下载:
下载: