Intelligent Semantic Location Privacy Protection Method for Location Based Services in Three-Dimensional Spaces
-
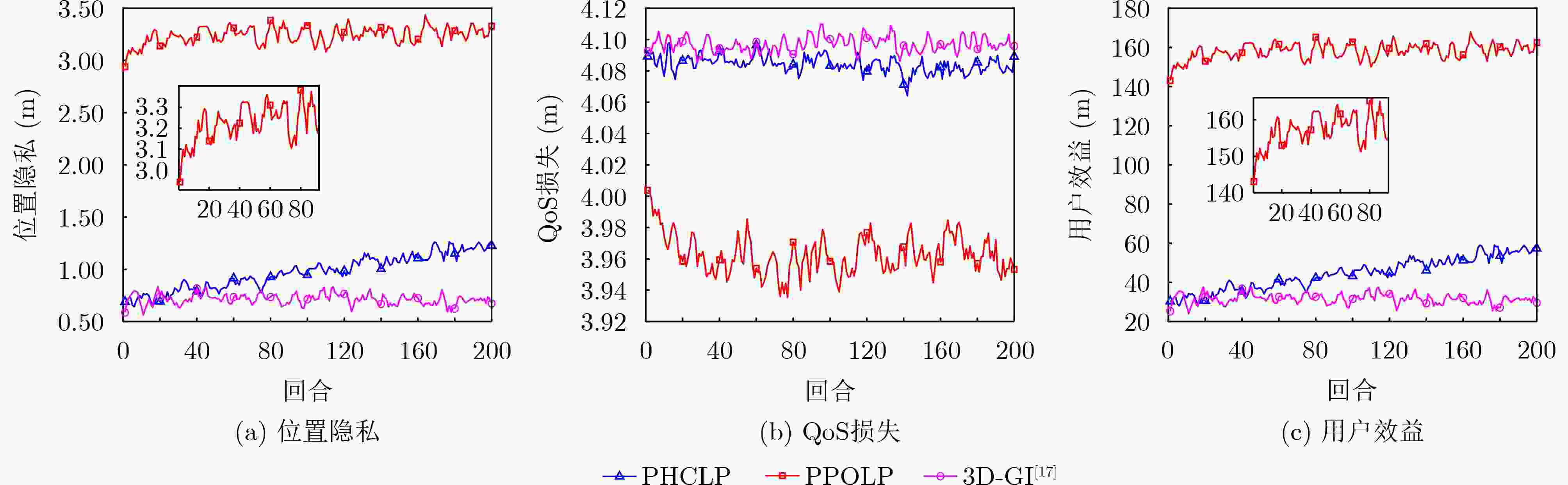
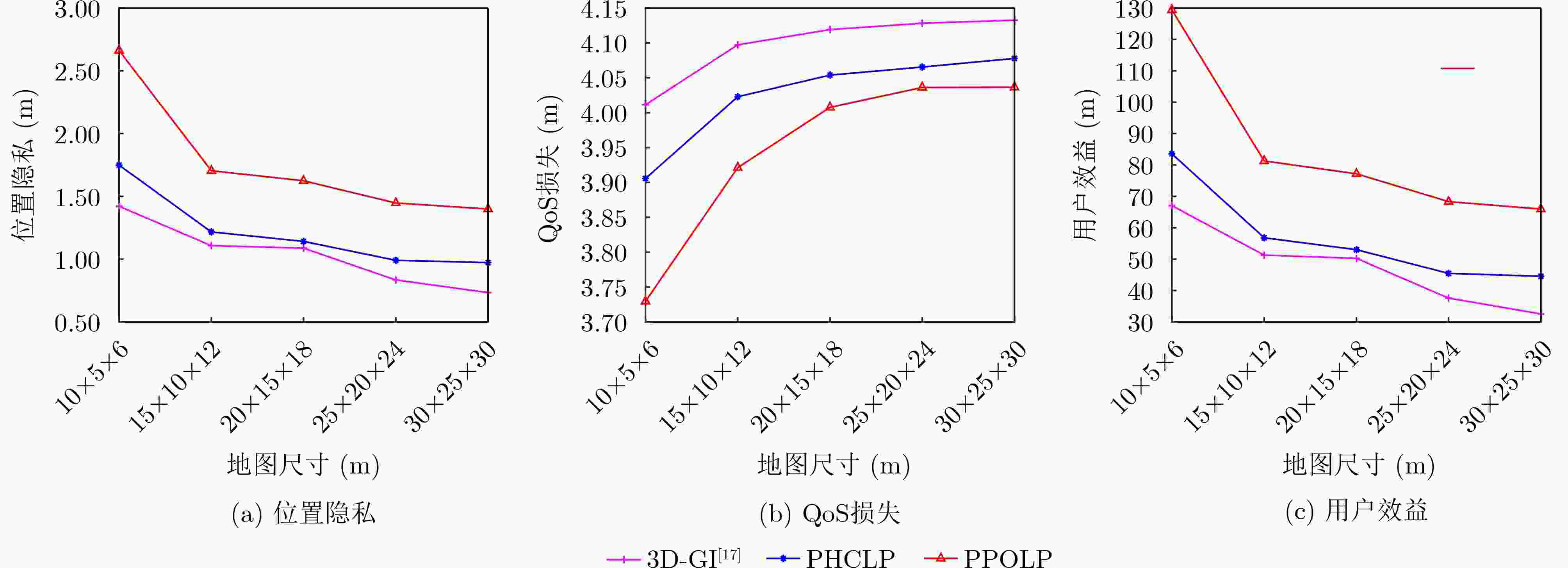
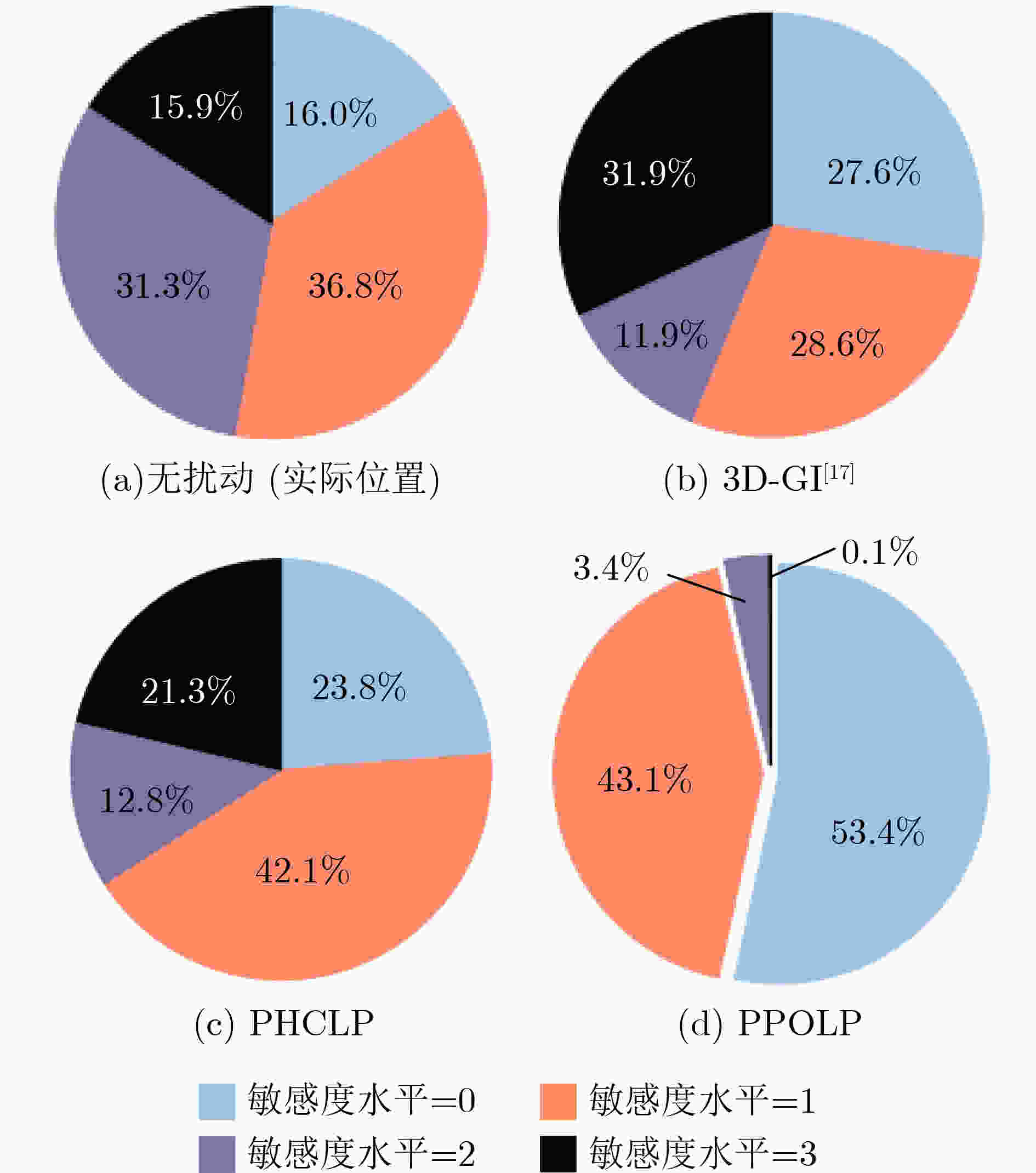
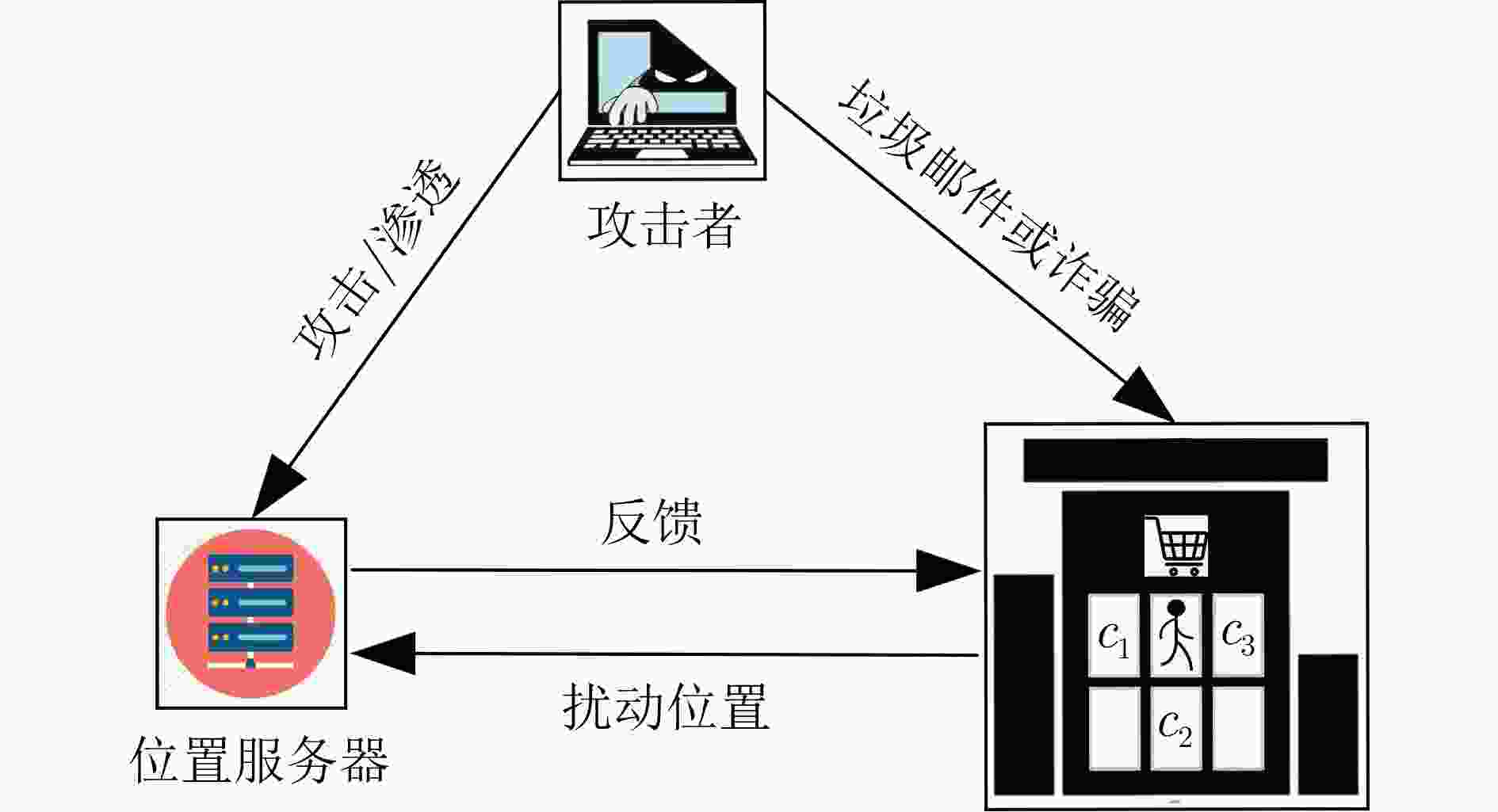
摘要: 针对大型医院、商场及其他3维(3D)空间位置服务中敏感语义位置(如药店、书店等)隐私泄露问题,该文研究了基于3D空间地理不可区分性(3D-GI)的智能语义位置隐私保护方法。为摆脱对特定环境和攻击模型的依赖,该文利用强化学习(RL)技术实现对用户语义位置隐私保护策略的动态优化,提出基于策略爬山算法(PHC)的3D语义位置扰动机制。该机制通过诱导攻击者推断较低敏感度的语义位置来减少高敏感语义位置的暴露。为解决复杂3D空间环境下的维度灾难问题,进一步提出基于近端策略优化算法(PPO)的3D语义位置扰动机制,利用神经网络捕获环境特征并采用离线策略梯度方法优化神经网络参数更新,提高语义位置扰动策略选择效率。仿真实验结果表明,所提方法可提升用户的语义位置隐私保护性能和服务体验。Abstract: An intelligent semantic location privacy protection method based on 3D Geo-Indistinguishability (3D-GI) is studied for the privacy leakage problem of sensitive semantic locations (such as medicine stores and bookstores) in 3D space location-based services, such as hospitals and shopping centers. Reinforcement Learning (RL) techniques are used in this paper to optimize user’s semantic location privacy protection policies dynamically. Specifically, a 3D semantic location perturbation mechanism is proposed based on the Policy Hill Climbing (PHC) algorithm, independent of specific environments and attack models. This mechanism induces attackers to infer less sensitive locations to reduce the exposure of sensitive semantic locations. To address the dimensional disaster problem of complex 3D space, a 3D semantic location perturbation mechanism based on the Proximal Policy Optimization (PPO) algorithm is further proposed. This mechanism captures the environment features using a neural network and optimizes the neural network parameter updates through the offline policy gradient method to improve the efficiency of semantic location perturbation policy selection. Experimental results show that the proposed mechanism improves both semantic location privacy protection and user service experience.
-
表 1 符号含义
符号 含义 $ {\varepsilon ^{(k)}} $ 隐私预算 $ {d^{(k)}}/{c^{(k)}}/{l^{(k)}} $ 实际地理位置/语义位置/语义位置敏感度 $ {\tilde d^{(k)}}/{\tilde c^{(k)}}/{\tilde l^{(k)}} $ 扰动地理位置/语义位置/语义位置敏感度 $ {\hat d^{(k)}}/{\hat c^{(k)}}/{\hat l^{(k)}} $ 推断地理位置/语义位置/语义位置敏感度 $ {p^{(k)}} $ 隐私水平 $ {q^{(k)}} $ 服务质量(QoS)损失 $ {u^{(k)}} $ 用户的效益 1 基于PHC 的3D语义位置扰动机制
初始化$ Q $表,$ V $表及$ \pi $表,系统参数$\alpha $, $\gamma $, $\delta $, $ {d^{\left( 1 \right)}} $, $ {c^{\left( 1 \right)}} $, $ {l^{\left( 1 \right)}} $,
$ {\varpi ^{\left( 0 \right)}} $;设置学习迭代次数。(1) For $k = 1,2, \cdots $do (2) 观察当前系统状态$ {s^{\left( k \right)}} = \left[ {{d^{\left( k \right)}},{c^{\left( k \right)}},{l^{\left( k \right)}},{\varpi ^{\left( {k - 1} \right)}}} \right] $ (3) 根据$\pi $表选择位置扰动策略$ {{\boldsymbol{a}}^{(k)}} $ (4) 根据伽马分布$ \varGamma \left( {3,{1 \mathord{\left/ {\vphantom {1 \varepsilon }} \right. } \varepsilon }} \right) $,产生预算对应的$ r $ (5) 通过式(6)获得扰动位置$ {\tilde d^{\left( k \right)}} $,并根据地图信息获取$ {\tilde c^{(k)}} $ (6) 根据扰动位置$ ({\tilde d^{(k)}},{\tilde c^{(k)}}) $请求LBS (7) 通过式(7)获取效益$ {u^{\left( k \right)}} $ (8) 通过式(8)更新$ Q({{\boldsymbol{s}}^{(k)}},{{\boldsymbol{a}}^{(k)}}) $ (9) 通过式(9)更新$ V({{\boldsymbol{s}}^{(k)}}) $ (10) 通过式(10)更新$ \pi ({{\boldsymbol{s}}^{(k)}},{\boldsymbol{a}}) $ (11) End 2 基于PPO的3D语义位置扰动机制
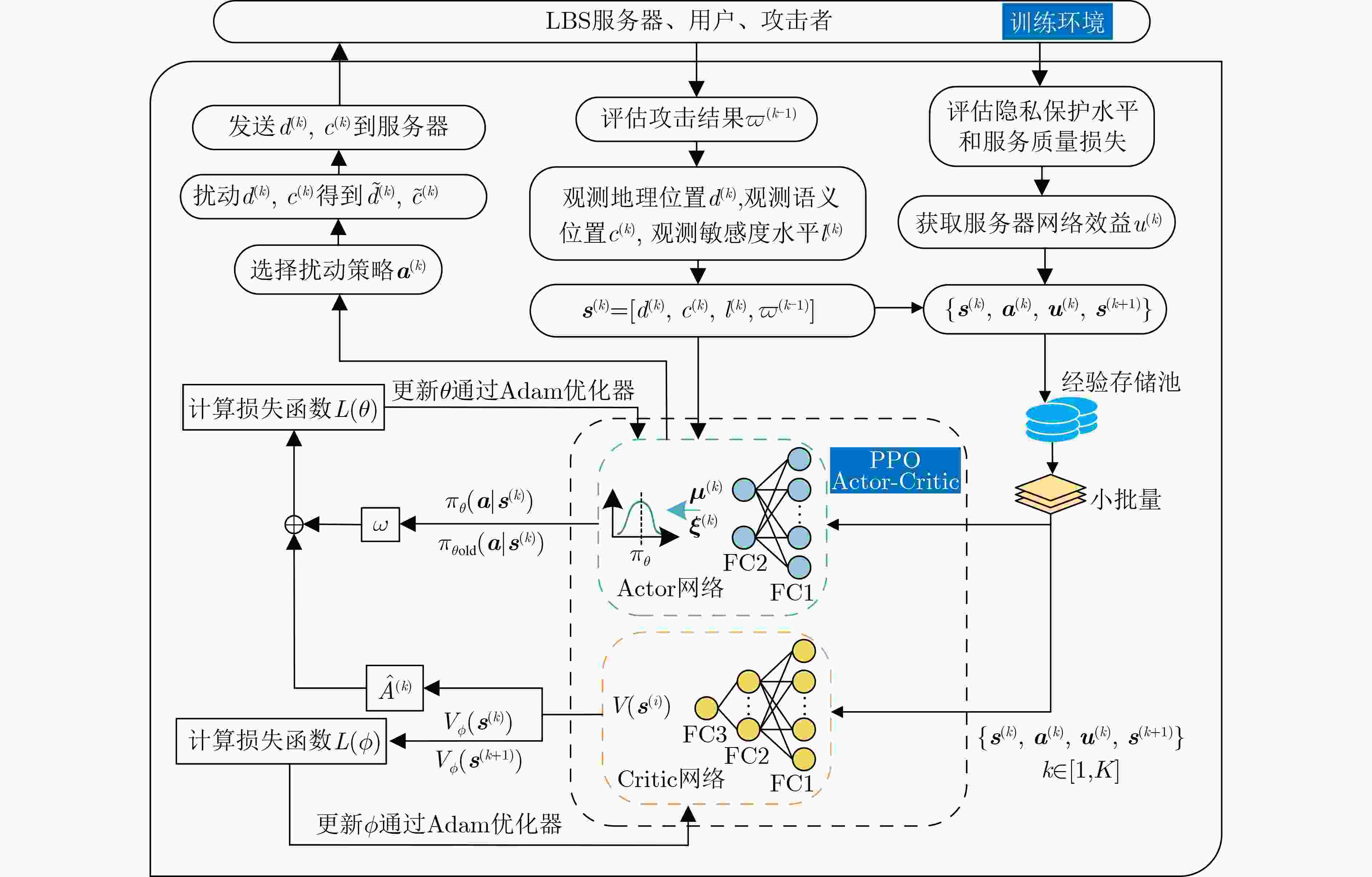
初始化系统参数和网络参数$\gamma $, $\delta $, ${d^{(1)}}$, ${c^{(1)}}$, ${l^{(1)}}$, $ {\varpi ^{(0)}} $, $ {\theta ^{(0)}} $,
$ {\phi ^{(0)}} $(1) For $k = 1,2, \cdots $do (2) 观察当前系统状态$ {s^{(k)}} = \left[ {{d^{\left( k \right)}},{c^{\left( k \right)}},{l^{\left( k \right)}},{\varpi ^{\left( {k - 1} \right)}}} \right] $ (3) 将状态$ {{\boldsymbol{s}}^{(k)}} $输入到Actor网络得到$ {\mu ^{(k)}} $和$ {\xi ^{(k)}} $ (4) 通过式(10)得到$ {\pi _\theta }({\boldsymbol{a}}|{{\boldsymbol{s}}^{(k)}}) $ (5) 根据$ {\pi _\theta }({\boldsymbol{a}}|{{\boldsymbol{s}}^{(k)}}) $选择扰动策略$ {{\boldsymbol{a}}^{(k)}} $ (6) 扰动位置的获取参考算法1中的步骤4~5 (7) 根据扰动位置$ ({\tilde d^{(k)}},{\tilde c^{(k)}}) $请求LBS (8) 通过式(7)进行效益评估 (9) 将经验序列$ {{\boldsymbol{\varPsi}} ^{(k)}} = ({{\boldsymbol{s}}^{(k)}},{{\boldsymbol{a}}^{(k)}},{u^{(k)}},{{\boldsymbol{s}}^{(k + 1)}}) $存入经验存
储池中(10) If then (11) 从经验池中抽取小批量经验值输入到Actor和Critic网络中 (12) 通过式(12)计算优势函数$ \hat A({{\boldsymbol{s}}^{(k)}},{{\boldsymbol{a}}^{(k)}}) $ (13) 通过式(13)更新Actor网络参数$ \theta $ (14) 通过式(14)更新Critic网络参数$ \phi $ (15) End (16) End 表 2 仿真过程的超参数设置
参数 PHCLP机制 PPOLP机制 学习率$ \alpha $ 0.5 0.001/0.003
(Actor/Critic)折扣因子$ \gamma $ 0.9 0.9 截断系数$ \sigma $ - 0.1 batch-size - 32 激活函数 - Adam 神经网络隐藏层数(Actor/Critic) - 2层/3层 隐藏的单元数(Actor/Critic) - 8,8/8,8,8 -
[1] 张鸿刚. 面向多情景的位置服务隐私保护算法研究与应用[D]. [硕士论文], 南京邮电大学, 2022.ZHANG Honggang. Research and application of privacy-preserving algorithms for location services in multiple scenarios[D]. [Master dissertation], Nanjing University of Posts and Telecommunications, 2022. [2] XU Chuan, DING Yingyi, CHEN Chao, et al. Personalized location privacy protection for location-based services in vehicular networks[J]. IEEE Transactions on Intelligent Transportation Systems, 2023, 24(1): 1163–1177. doi: 10.1109/TITS.2022.3182019 [3] YANG Zhigang, WANG Ruyan, WU Dapeng, et al. Local trajectory privacy protection in 5G enabled industrial intelligent logistics[J]. IEEE Transactions on Industrial Informatics, 2022, 18(4): 2868–2876. doi: 10.1109/TII.2021.3116529 [4] BOSTANIPOUR B and THEODORAKOPOULOS G. Joint obfuscation of location and its semantic information for privacy protection[J]. Computers & Security, 2021, 107: 102310. doi: 10.1016/j.cose.2021.102310 [5] ZHENG Zhirun, LI Zhetao, JIANG Hongbo, et al. Semantic-aware privacy-preserving online location trajectory data sharing[J]. IEEE Transactions on Information Forensics and Security, 2022, 17: 2256–2271. doi: 10.1109/TIFS.2022.3181855 [6] NIU Ben, LI Qinghua, WANG Hanyi, et al. A framework for personalized location privacy[J]. IEEE Transactions on Mobile Computing, 2022, 21(9): 3071–3083. doi: 10.1109/TMC.2021.3055865 [7] REN Weilong, GHAZINOUR K, and LIAN Xiang. kt-safety: Graph release via k -anonymity and t-closeness[J]. IEEE Transactions on Knowledge and Data Engineering, 2023, 35(9): 9102–9113. doi: 10.1109/TKDE.2022.3221333 [8] HOU Lei, YAO Nianmin, LU Zhimao, et al. Tracking based mix-zone location privacy evaluation in VANET[J]. IEEE Transactions on Vehicular Technology, 2021, 70(10): 10957–10969. doi: 10.1109/TVT.2021.3109065 [9] MOQURRAB S A, ANJUM A, TARIQ N, et al. Instant_Anonymity: A lightweight semantic privacy guarantee for 5G-enabled IIoT[J]. IEEE Transactions on Industrial Informatics, 2023, 19(1): 951–959. doi: 10.1109/TII.2022.3179536 [10] PERALTA-PETERSON M and KOTEVSKA O. Effectiveness of privacy techniques in smart metering systems[C]. 2021 International Conference on Computational Science and Computational Intelligence (CSCI), Las Vegas, USA, 2021: 675–678. [11] ZHU Yujia and ZHAI Lidong. Location privacy in buildings: A 3-dimensional k-anonymity model[C]. The 10th International Conference on Mobile Ad-hoc and Sensor Networks, Maui, USA, 2015: 195–200. [12] KUMAR R and DAWRA S. Simulation of 3D privacy preservation and location monitoring approach[J]. International Research Journal of Engineering and Technology (IRJET), 2016, 3(5): 1099–1103. [13] DWORK C. Differential privacy: A survey of results[C]. The 5th International Conference on Theory and Applications of Models of Computation, Xi’an, China, 2008: 1–19. [14] ZHAO Ying and CHEN Jinjun. A survey on differential privacy for unstructured data content[J]. ACM Computing Surveys, 2022, 54(10s): 207. doi: 10.1145/3490237 [15] ANDRÉS M E, BORDENABE N E, CHATZIKOKOLAKIS K, et al. Geo-indistinguishability: Differential privacy for location-based systems[C]. The 2013 ACM SIGSAC Conference on Computer & Communications Security (CCS), Berlin, Germany, 2013: 901–914. [16] ZHANG Pengfei, CHENG Xiang, SU Sen, et al. Task allocation under geo-indistinguishability via group-based noise addition[J]. IEEE Transactions on Big Data, 2023, 9(3): 860–877. doi: 10.1109/TBDATA.2022.3215467 [17] MIN Minghui, XIAO Liang, DING Jiahao, et al. 3D geo-indistinguishability for indoor location-based services[J]. IEEE Transactions on Wireless Communications, 2022, 21(7): 4682–4694. doi: 10.1109/TWC.2021.3132464 [18] ZHANG Wenjing, JIANG Bo, LI Ming, et al. Privacy-preserving aggregate mobility data release: An information-theoretic deep reinforcement learning approach[J]. IEEE Transactions on Information Forensics and Security, 2022, 17: 849–864. doi: 10.1109/TIFS.2022.3152361 [19] LIU Bo, ZHOU Wanlei, ZHU Tianqing, et al. Location privacy and its applications: A systematic study[J]. IEEE Access, 2018, 6: 17606–17624. doi: 10.1109/ACCESS.2018.2822260 [20] MIN Minghui, WANG Weihang, XIAO Liang, et al. Reinforcement learning-based sensitive semantic location privacy protection for VANETs[J]. China Communications, 2021, 18(6): 244–260. doi: 10.23919/JCC.2021.06.019 [21] VEGA F and YU Wen. Smartphone based structural health monitoring using deep neural networks[J]. Sensors and Actuators A:Physical, 2022, 346: 113820. doi: 10.1016/j.sna.2022.113820 [22] SHANKAR N, BHAT G S, and PANAHI I M S. Real-time single-channel deep neural network-based speech enhancement on edge devices[C]. The Interspeech 2020, 21st Annual Conference of the International Speech Communication Association, Shanghai, China, 2020: 3281–3285. [23] MIN Minghui, XIAO Liang, XIE Caixia, et al. Defense against advanced persistent threats in dynamic cloud storage: A colonel blotto game approach[J]. IEEE Internet of Things Journal, 2018, 5(6): 4250–4261. doi: 10.1109/JIOT.2018.2844878 [24] SCHULMAN J, WOLSKI F, DHARIWAL P, et al. Proximal policy optimization algorithms[J]. arXiv preprint arXiv: 1707.06347, 2017. [25] FERNANDES N, DRAS M, and MCIVER A. Generalised differential privacy for text document processing[C]. The 8th International Conference on Principles of Security and Trust, Prague, Czech Republic, 2019: 123–148. [26] FATHALIZADEH A, MOGHTADAIEE V, and ALISHAHI M. Indoor geo-indistinguishability: Adopting differential privacy for indoor location data protection[J]. IEEE Transactions on Emerging Topics in Computing, 2023: 1–13. [27] 李玉柏, 孙迅. 基于迁移学习提高WiFi室内定位中信道状态信息指纹库的鲁棒性[J]. 电子与信息学报, 2023, 45(10): 3657–3666. doi: 10.11999/JEIT221160LI Yubai and SUN Xun. A highly robust indoor location algorithm using WiFi channel state information based on transfer learning reinforcement[J]. Journal of Electronics & Information Technology, 2023, 45(10): 3657–3666. doi: 10.11999/JEIT221160 [28] GÖTZ M, NATH S, and GEHRKE J. MaskIt: Privately releasing user context streams for personalized mobile applications[C]. The 2012 ACM SIGMOD International Conference on Management of Data, Scottsdale, USA, 2012: 289–300. [29] CHENG Hao, XIA Yili, HUANG Yongming, et al. Improper Gaussian signaling for downlink NOMA systems with imperfect successive interference cancellation[J]. IEEE Transactions on Wireless Communications, 2022, 21(9): 7753–7763. doi: 10.1109/TWC.2022.3161379 [30] KUMAR H, KOPPEL A, and RIBEIRO A. On the sample complexity of actor-critic method for reinforcement learning with function approximation[J]. Machine Learning, 2023, 112(7): 2433–2467. doi: 10.1007/s10994-023-06303-2 [31] YANG Helin, XIONG Zehui, ZHAO Jun, et al. Intelligent reflecting surface assisted anti-jamming communications: A fast reinforcement learning approach[J]. IEEE Transactions on Wireless Communications, 2021, 20(3): 1963–1974. doi: 10.1109/TWC.2020.3037767 [32] XIAO Liang, HONG Siyuan, XU Shiyu, et al. IRS-aided energy-efficient secure WBAN transmission based on deep reinforcement learning[J]. IEEE Transactions On Communications, 2022, 70(6): 4162–4174. doi: 10.1109/TCOMM.2022.3169813 [33] XIONG Jinbo, MA Rong, CHEN Lei, et al. A personalized privacy protection framework for mobile crowdsensing in IIoT[J]. IEEE Transactions on Industrial Informatics, 2020, 16(6): 4231–4241. doi: 10.1109/TII.2019.2948068 -





 下载:
下载: