Virtual Ring Privacy Preserving Scheme Based on Fog Computing for Smart Meter System
-
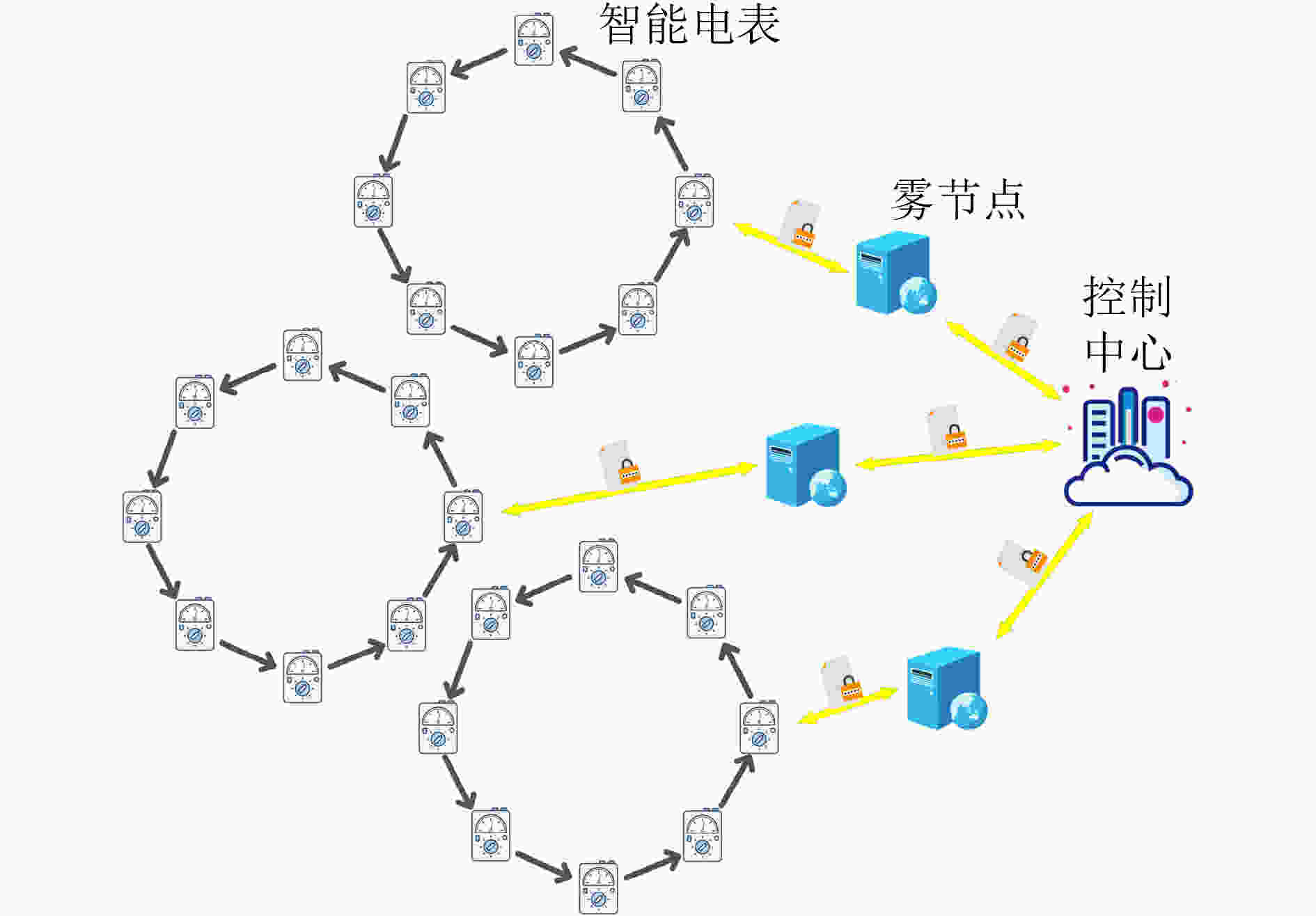
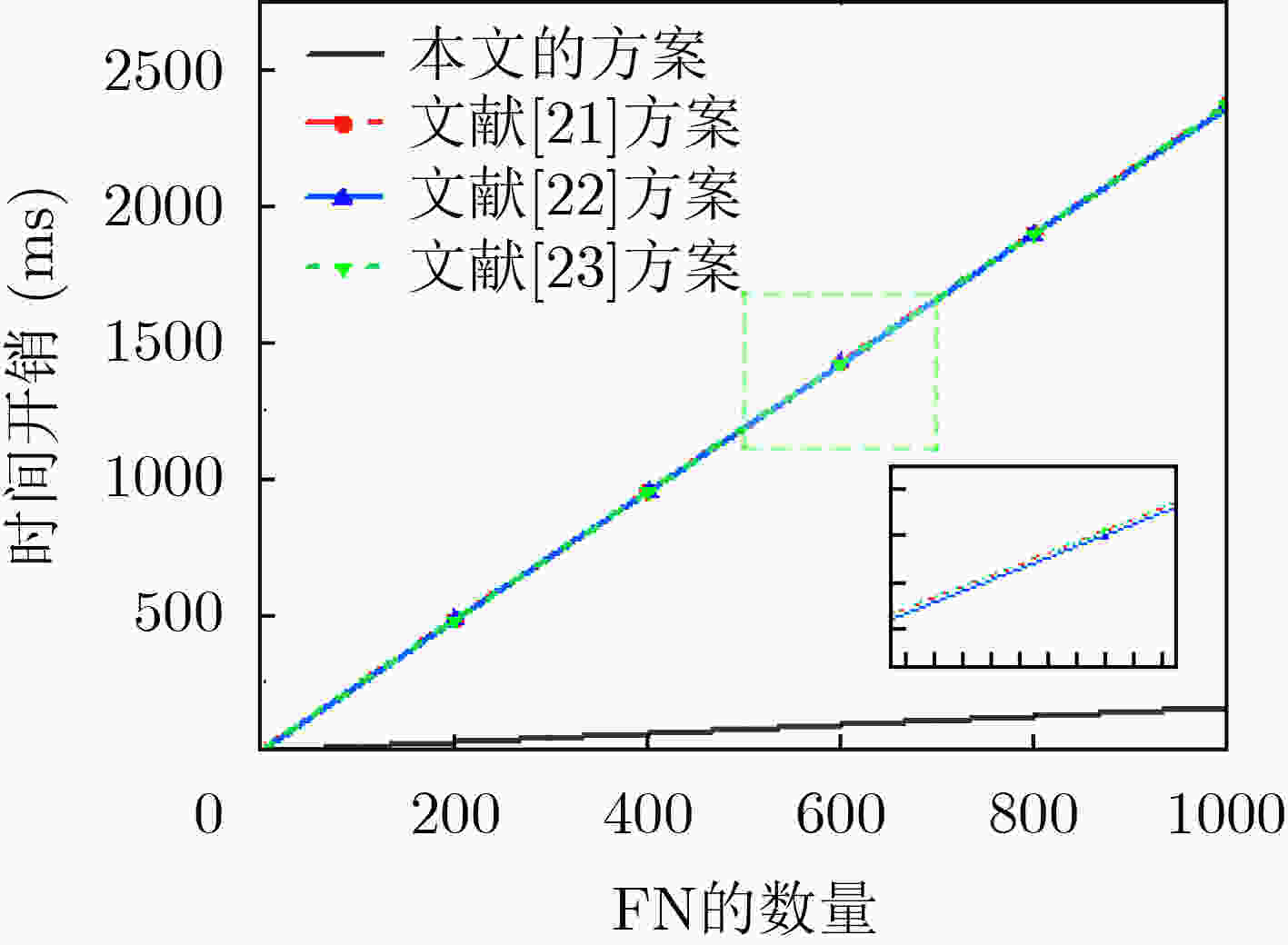
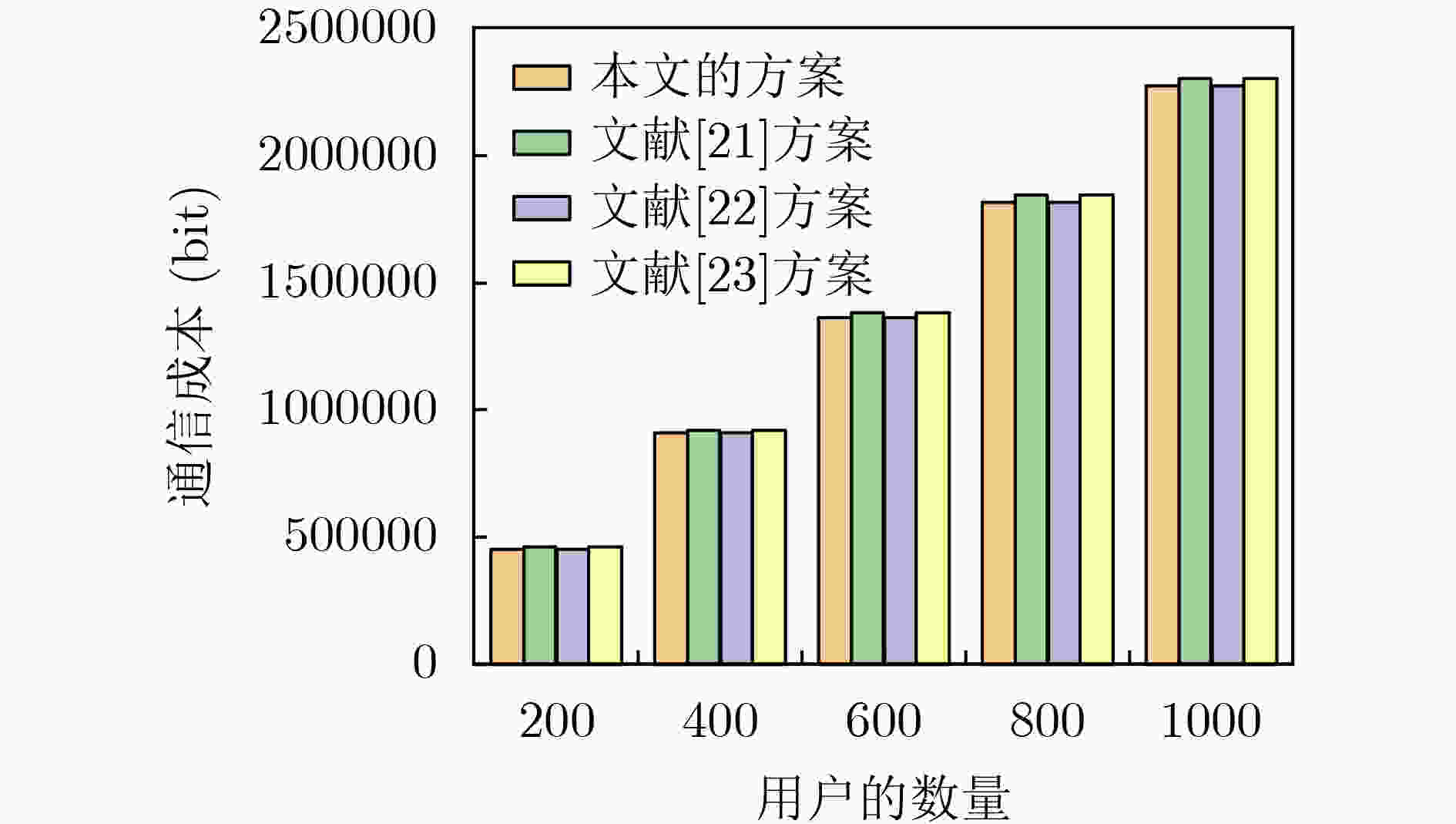
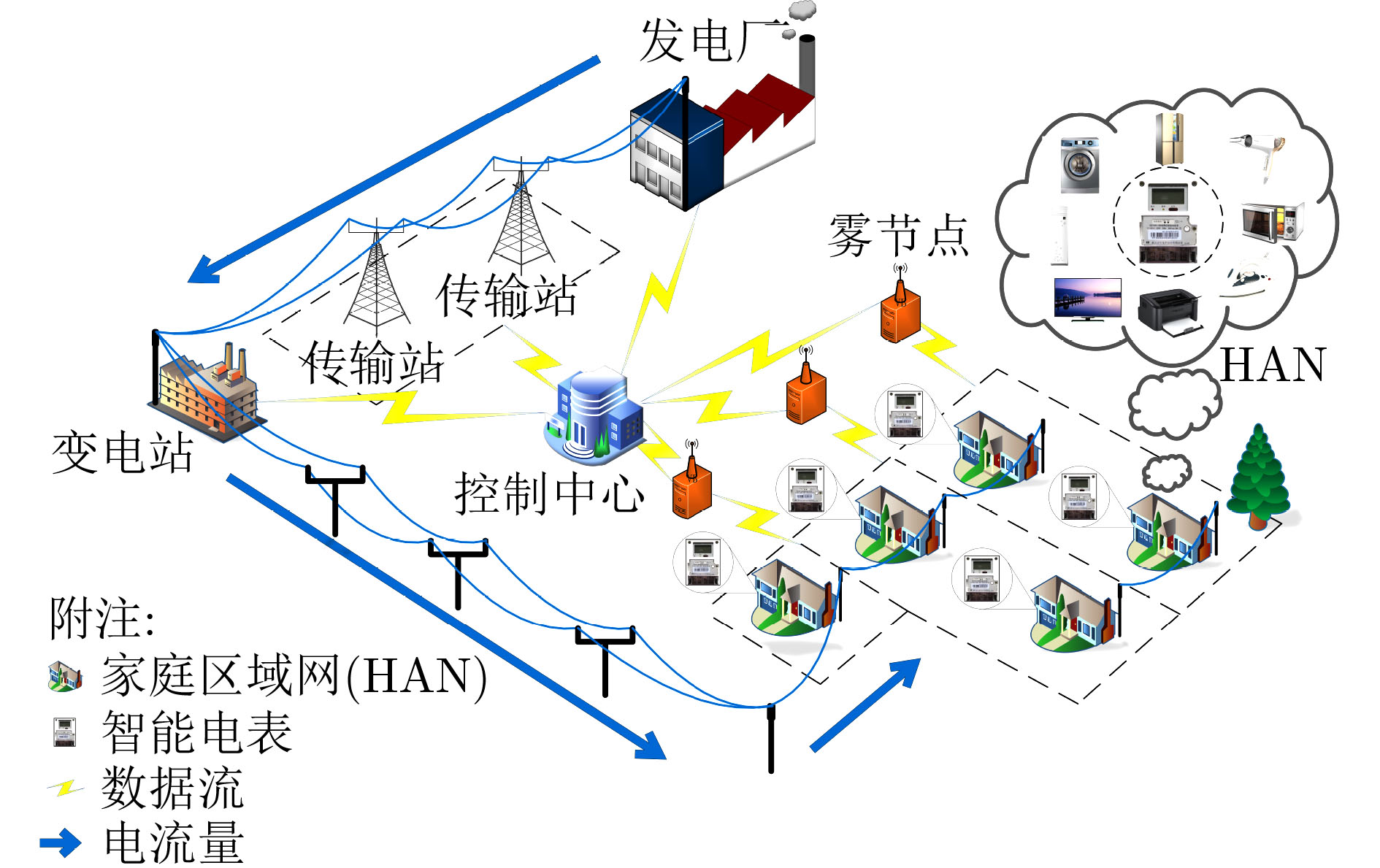
摘要: 作为智能电网的基础组件,智能电表(SMS)可以定期向电力公司报告用户的详细用电量数据。但是智能电表也带来了一些安全问题,比如用户隐私泄露。该文提出了一种基于虚拟环的隐私保护方案,可以提供用电数据和用户身份的隐私,使攻击者无法知道匹配电力数据与用户身份的关系。在所提方案中,智能电表可以利用其虚拟环成员身份对其真实身份进行匿名化,并利用非对称加密和Paillier同态系统对其获得的用电量数据生成密文数据;然后智能电表将密文数据发送给其连接的雾节点,雾节点定期采集其管理的智能电表的密文数据。同时,雾节点对这些智能电表的虚拟环身份进行验证,然后将收集到的密文数据聚合并发送给控制中心;最后控制中心对聚合后的密文进行解密,得到用电量数据。实验结果表明所提方案在计算和通信成本上具有一定的优势。Abstract: As the basic component of smart grid, Smart Meter System (SMS) can regularly report the detailed electricity consumption data of users to power companies. However, SMS also bring some security problems, such as user privacy disclosure. This paper proposes a privacy protection scheme based on virtual ring for SMS based on fog computing. This scheme can provide the privacy of power consumption data and user identity, so that the attacker can not know the relationship between matching power data and user identity. In the proposed scheme, the SMS can use its virtual ring membership to anonymize its real identity, and it can also use asymmetric encryption and Paillier homomorphic system to generate ciphertext data from its power consumption data; Then the SMS sends the ciphertext data to the connected fog node, and the fog node collects regularly the ciphertext data of the SMS it manages. At the same time, the fog node verifies the virtual ring identity of these SMS, and then aggregates the collected ciphertext data and sends it to the control center; Finally, the control center decrypts the aggregated ciphertext to obtain the power consumption data. The experimental results show that the proposed scheme has some advantages in computing and communication costs.
-
Key words:
- Privacy preserving /
- Fog computing /
- Smart Meter System (SMS) /
- Virtual Ring
-
表 1 智能电网中的网络攻击总结
表 2 符号和定义
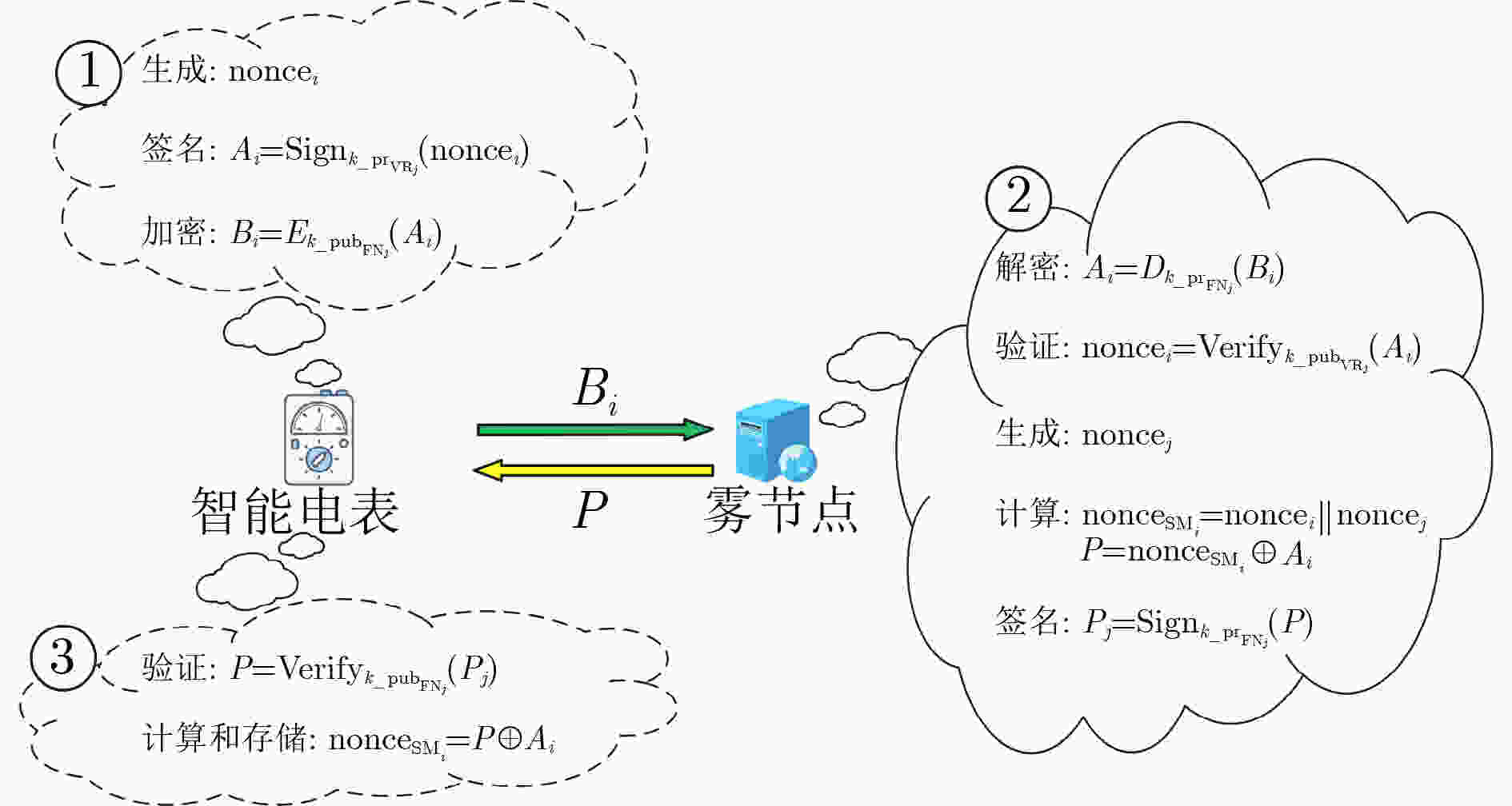
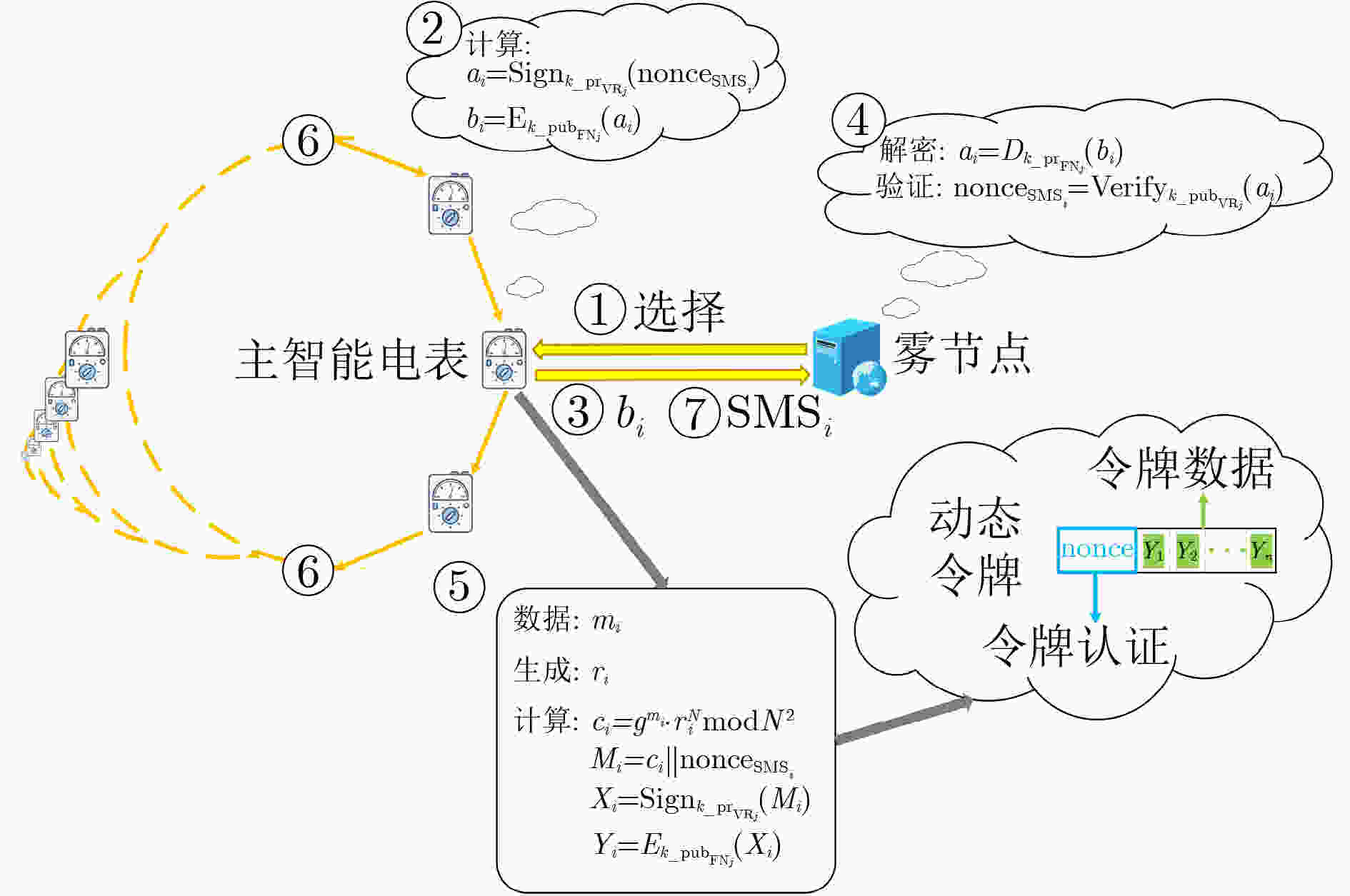
符号 定义 ${{ {{\rm{ID}}}_{ {{\rm{FN}}}_{j} } } }$ 雾节点${{\rm{FN}}}_{j}$的身份标识 ${ {{{\rm{ID}}}_{ {{\rm{VR}}}_{j} } } }$ 虚拟环${{ {{\rm{VR}}}_{j} } }$的标识符 ${k\_{\rm{pr}}}_{ {{\rm{VR}}}_{j} }$ 虚拟环${{\rm{VR}}}_{j}$的私钥 ${k\_{\rm{pub}}}_{ {{\rm{VR}}}_{j} }$ 虚拟环${{\rm{VR}}}_{j}$的公钥 ${k\_{\rm{pr}}}_{ {{\rm{FN}}}_{j} }$ 雾节点${{\rm{FN}}}_{j}$的私钥 ${k\_{\rm{pub}}}_{ {{\rm{FN}}}_{j} }$ 雾节点${{\rm{FN}}}_{j}$的公钥 ${K}_{ {{\rm{FC}}}_{j} }$ 雾节点${{\rm{FN}}}_{j}$和控制中心之间的共享密钥 $ {E}_{k}\left(\mathrm{*}\right) $ 非对称加密函数用密钥$ k $加密数据* $ {D}_{k}\left(\mathrm{*}\right) $ 非对称解密函数用密钥$ k $解密数据* ${{\rm{Sign}}}_{k}\left(\mathrm{*}\right)$ 用密钥$ k $签名数据* ${ {\rm{Verify} } }_{k}\left(\mathrm{*}\right)$ 用密钥$ k $验证签名数据* $ h(\cdot) $ 单向哈希函数 表 3 符号和定义
符号 定义 ${T}_{{\rm{enc}}}$ 公钥加密运算 ${T}_{{\rm{dec}}}$ 私钥解密运算 $ {C}_{e} $ 在$ {\mathbb{Z}}_{{N}^{2}} $上的指数运算 $ {C}_{m} $ 在$ {\mathbb{Z}}_{{N}^{2}} $上的乘法运算 ${C}_{{\rm{mg}}}$ 在$ \mathbb{G} $上的乘法运算 ${C}_{{\rm{et}}}$ 在$ {\mathbb{G}}_{T} $上的指数运算 $ {C}_{p} $ 双线性对运算 表 4 计算开销比较
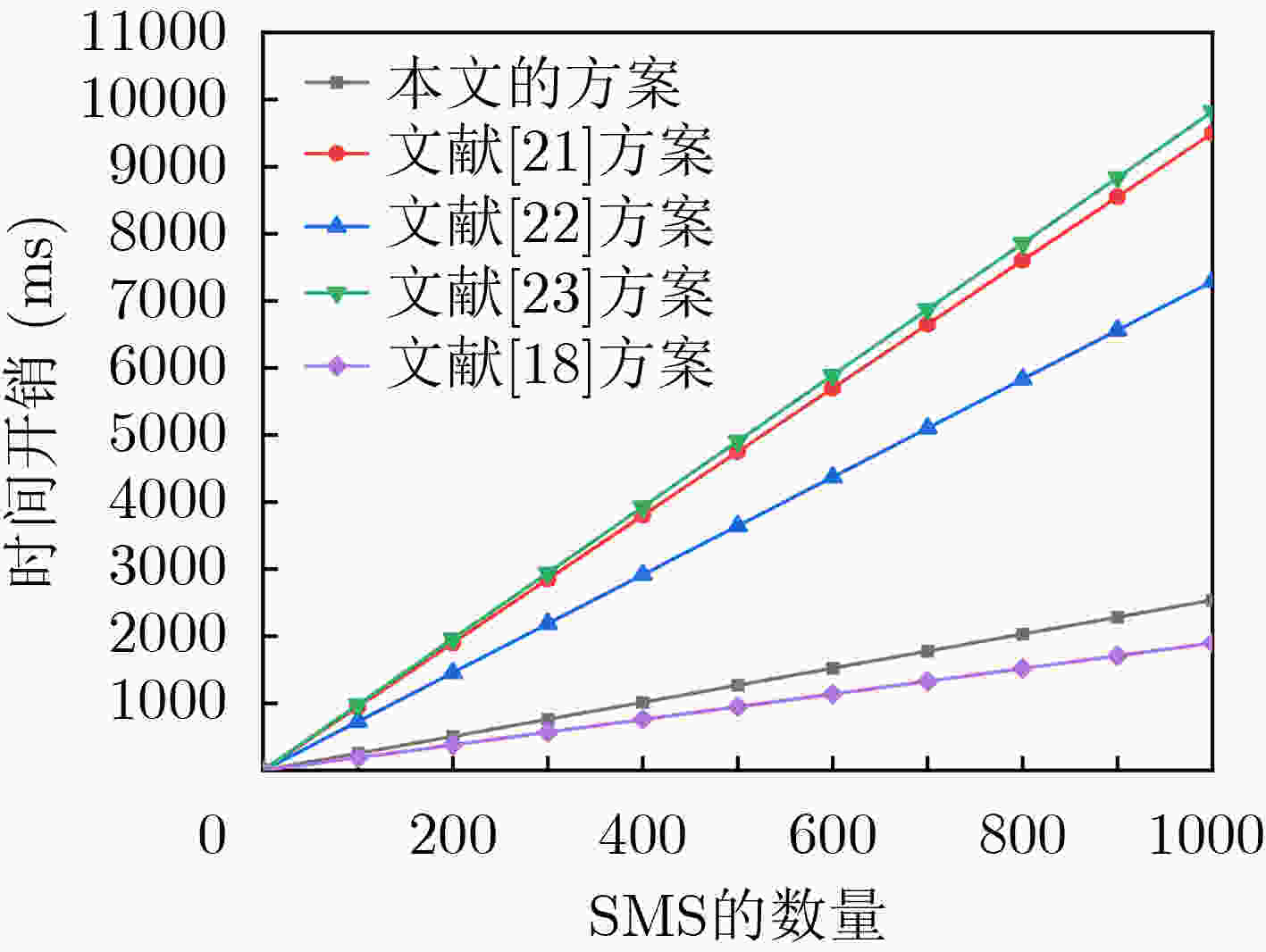
实体 本文方案 文献[21]方案 文献[22]方案 文献[23]方案 文献[18]方案 SMS $2 \cdot {C}_{{\rm{et}}}+{T}_{{\rm{enc}}}$ $2 \cdot {C}_{{\rm{et}}}+{C}_{{\rm{mgt}}}+4 \cdot {C}_{{\rm{pt}}}$ $2 \cdot {C}_{{\rm{et}}}+{C}_{{\rm{mgt}}}+3 \cdot {C}_{{\rm{pt}}}$ $3 \cdot {C}_{{\rm{et}}}+{C}_{{\rm{mgt}}}+4 \cdot {C}_{{\rm{pt}}}$ ${T}_{{\rm{enc}}}$ FN $\left(n-1\right) \cdot {C}_{m}+{T}_{{\rm{dec}}}$ $\begin{aligned} & \left(n-1\right) \cdot {C}_{m}+\left(n+3\right)\\& \cdot {C}_{{\rm{pt}}}+{C}_{{\rm{mgt}}} \end{aligned}$ $\left(n-1\right) \cdot {C}_{m}+\left(n+2\right) \cdot {C}_{pt}+{C}_{{\rm{mgt}}}$ $\begin{aligned} & \left(n-1\right) \cdot {C}_{m}+\left(n+3\right)\\& \cdot {C}_{{\rm{pt}}}+{C}_{{\rm{mgt}}}\end{aligned}$ $ - $ CC ${C}_{{\rm{et}}}$ ${C}_{{\rm{et}}}+2 \cdot {C}_{{\rm{pt}}}+4 \cdot {C}_{{\rm{mgt}}}+{C}_{{\rm{ett}}}$ $ - $ $\begin{aligned} & 2 \cdot {C}_{{\rm{et}}}+{C}_{m}+2 \cdot {C}_{{\rm{pt}}}\\& +4 \cdot {C}_{{\rm{mgt}}}+{C}_{{\rm{ett}}}\end{aligned}$ ${T}_{{\rm{dnc}}}$ -
[1] DILEEP G. A survey on smart grid technologies and applications[J]. Renewable Energy, 2020, 146: 2589–2625. doi: 10.1016/j.renene.2019.08.092 [2] ABRAHAMSEN F E, AI Y, and CHEFFENA M. Communication technologies for smart grid: A comprehensive survey[J]. Sensors, 2021, 21(23): 8087. doi: 10.3390/s21238087 [3] GUNDUZ M Z and DAS R. Cyber-security on smart grid: Threats and potential solutions[J]. Computer Networks, 2020, 169: 107094. doi: 10.1016/j.comnet.2019.107094 [4] XUE Ancheng, XU Feiyang, CHOW J H, et al. Data-driven detection for GPS spoofing attack using phasor measurements in smart grid[J]. International Journal of Electrical Power & Energy Systems, 2021, 129: 106883. doi: 10.1016/j.ijepes.2021.106883 [5] KHAN H M, KHAN A, JABEEN F, et al. Fog-enabled secure multiparty computation based aggregation scheme in smart grid[J]. Computers & Electrical Engineering, 2021, 94: 107358. doi: 10.1016/j.compeleceng.2021.107358 [6] CHAUDHRY S A, SHON T, AL-TURJMAN F, et al. Correcting design flaws: An improved and cloud assisted key agreement scheme in cyber physical systems[J]. Computer Communications, 2020, 153: 527–537. doi: 10.1016/j.comcom.2020.02.025 [7] LUO Xiaoyuan, LI Yating, Wang Xinyu, et al. Interval observer-based detection and localization against false data injection attack in smart grids[J]. IEEE Internet of Things Journal, 2021, 8(2): 657–671. doi: 10.1109/JIOT.2020.3005926 [8] BOYACI O, UMUNNAKWE A, SAHU A, et al. Graph neural networks based detection of stealth false data injection attacks in smart grids[J]. IEEE Systems Journal, 2022, 16(2): 2946–2957. doi: 10.1109/JSYST.2021.3109082 [9] WLAZLO P, SAHU A, MAO Zeyu, et al. Man-in-the-middle attacks and defense in a power system cyber-physical testbed[J]. arXiv preprint arXiv: 2102.11455, 2021. [10] QIAN Jiawei, CAO Zhenfu, DONG Xiaolei, et al. Two secure and efficient lightweight data aggregation schemes for smart grid[J]. IEEE Transactions on Smart Grid, 2021, 12(3): 2625–2637. doi: 10.1109/TSG.2020.3044916 [11] KHAZAEI J and AMINI M H. Protection of large-scale smart grids against false data injection cyberattacks leading to blackouts[J]. International Journal of Critical Infrastructure Protection, 2021, 35: 100457. doi: 10.1016/j.ijcip.2021.100457 [12] LEE A and BREWER T. Smart grid cyber security strategy and requirements[R]. DRAFT NISTIR 7628, 2009. [13] RODRIGUEZ-CALVO A, COSSENT R, and FRÍAS P. Scalability and replicability analysis of large-scale smart grid implementations: Approaches and proposals in Europe[J]. Renewable and Sustainable Energy Reviews, 2018, 93: 1–15. doi: 10.1016/j.rser.2018.03.041 [14] DONG Siliang, ZENG Zhixin, and LIU Yining. FPETD: Fault-tolerant and privacy-preserving electricity theft detection[J]. Wireless Communications and Mobile Computing, 2021, 2021: 6650784. doi: 10.1155/2021/6650784 [15] GUAN A and GUAN D J. An efficient and privacy protection communication scheme for smart grid[J]. IEEE Access, 2020, 8: 179047–179054. doi: 10.1109/ACCESS.2020.3025788 [16] LYU L, NANDAKUMAR K, RUBINSTEIN B, et al. PPFA: Privacy preserving fog-enabled aggregation in smart grid[J]. IEEE Transactions on Industrial Informatics, 2018, 14(8): 3733–3744. doi: 10.1109/TII.2018.2803782 [17] ZHANG Chuan, ZHU Liehuang, XU Chang, et al. Reliable and privacy-preserving truth discovery for mobile crowdsensing systems[J]. IEEE Transactions on Dependable and Secure Computing, 2021, 18(3): 1245–1260. doi: 10.1109/TDSC.2019.2919517 [18] BADRA M and ZEADALLY S. Design and performance analysis of a virtual ring architecture for smart grid privacy[J]. IEEE Transactions on Information Forensics and Security, 2014, 9(2): 321–329. doi: 10.1109/TIFS.2013.2296441 [19] OUAFI K and PHAN R C W. Privacy of recent RFID authentication protocols[C]. Proceedings of the 4th International Conference on Information Security Practice and Experience, Sydney, Australia, 2008: 263–277. [20] PAILLIER P. Public-key cryptosystems based on composite degree residuosity classes[C]. Proceedings of the 17th International Conference on Theory and Application of Cryptographic Techniques, Prague, Czech Republic, 1999: 223–238. [21] LU Rongxing, LIANG Xiaohui, LI Xu, et al. EPPA: An efficient and privacy-preserving aggregation scheme for secure smart grid communications[J]. IEEE Transactions on Parallel and Distributed Systems, 2012, 23(9): 1621–1631. doi: 10.1109/TPDS.2012.86 [22] CHEN Yuwen, MARTÍNEZ-ORTEGA J F, CASTILLEJO P, et al. A homomorphic-based multiple data aggregation scheme for smart grid[J]. IEEE Sensors Journal, 2019, 19(10): 3921–3929. doi: 10.1109/JSEN.2019.2895769 [23] YANG Xuhui, ZHANG Shaomin, and WANG Baoyi. Multi-data aggregation scheme based on multiple subsets to realize user privacy protection[C]. 2018 12th IEEE International Conference on Anti-counterfeiting, Security, and Identification (ASID), Xiamen, China, 2018: 61–65. -





 下载:
下载: