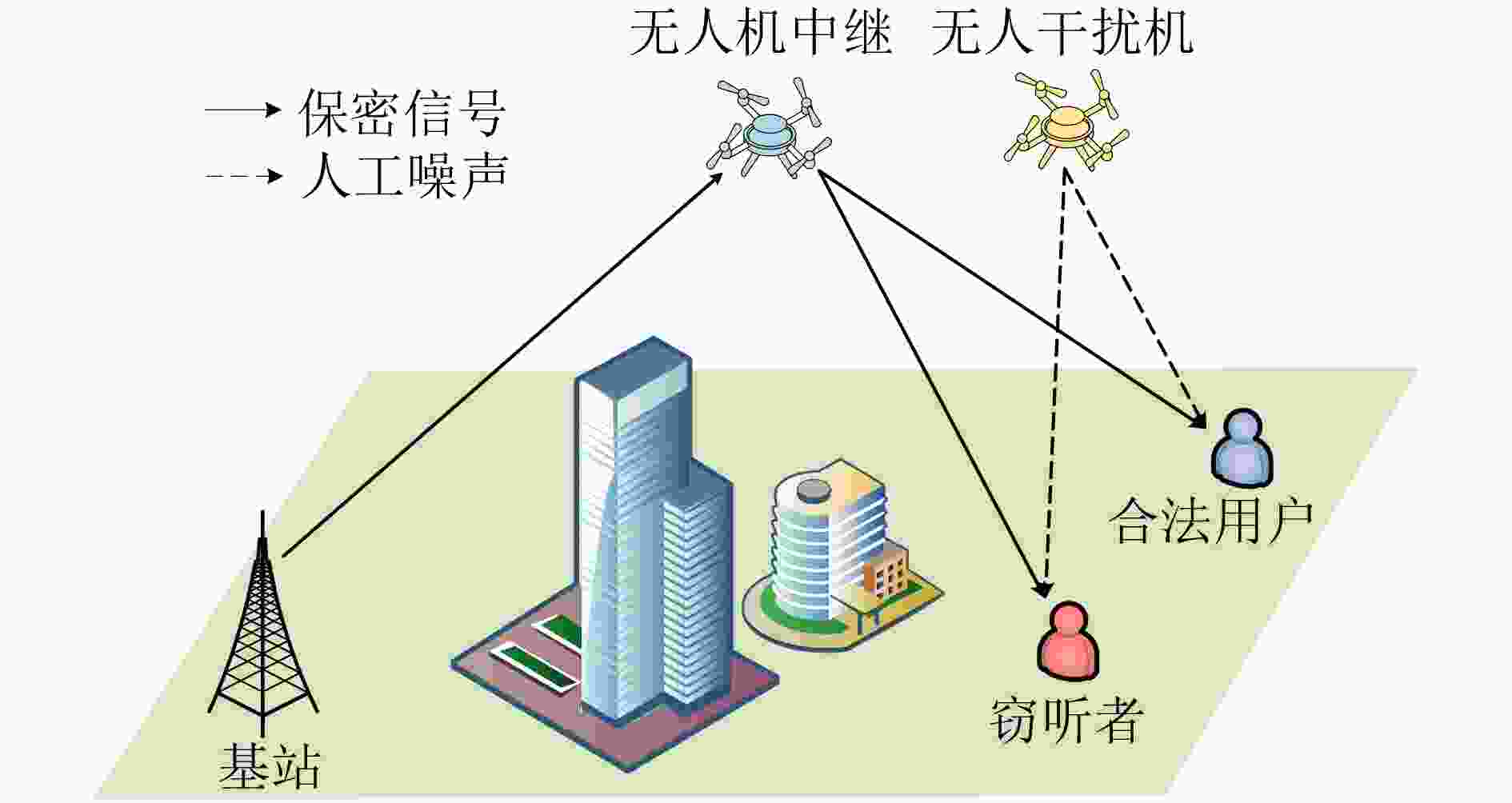
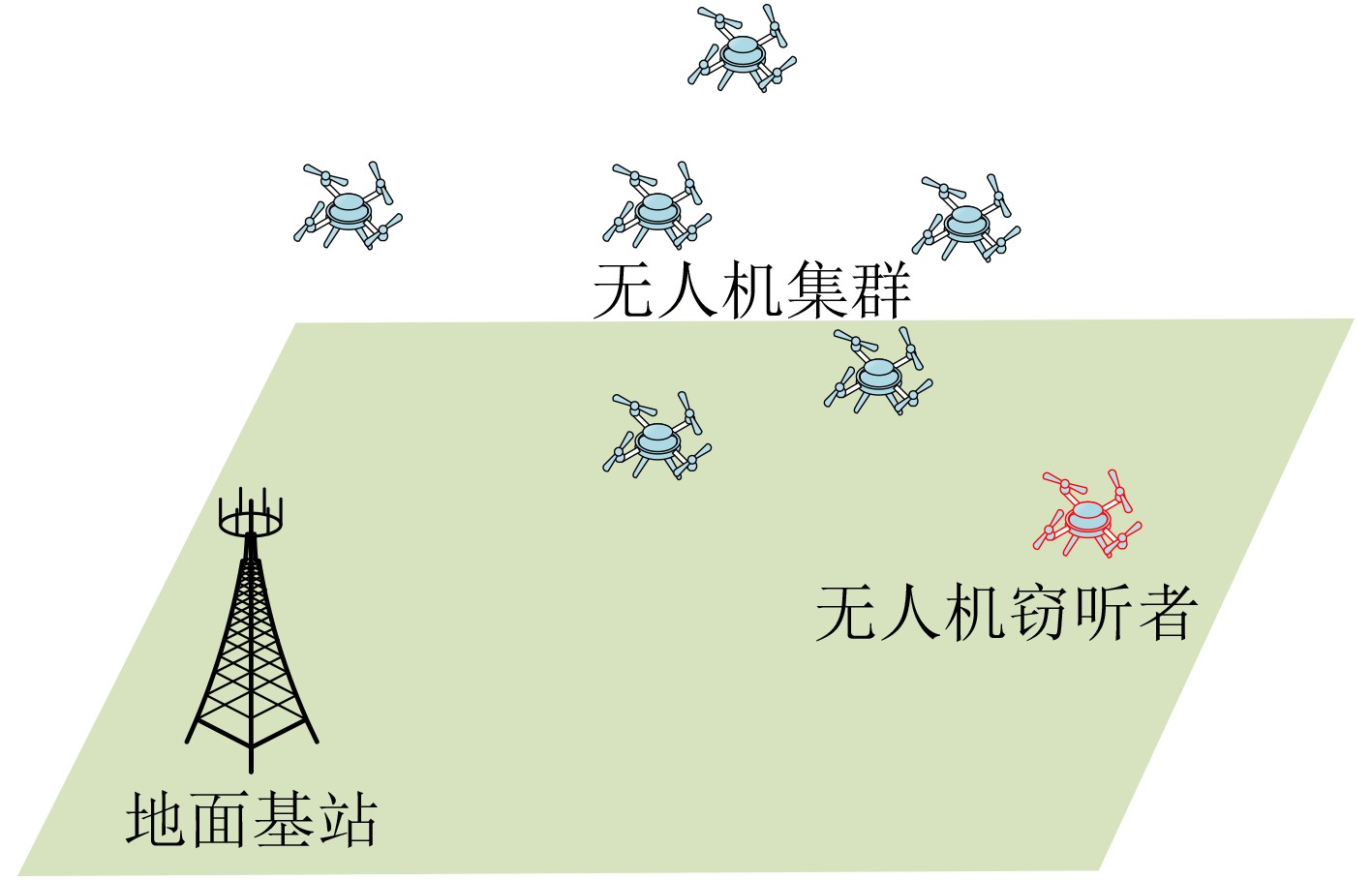
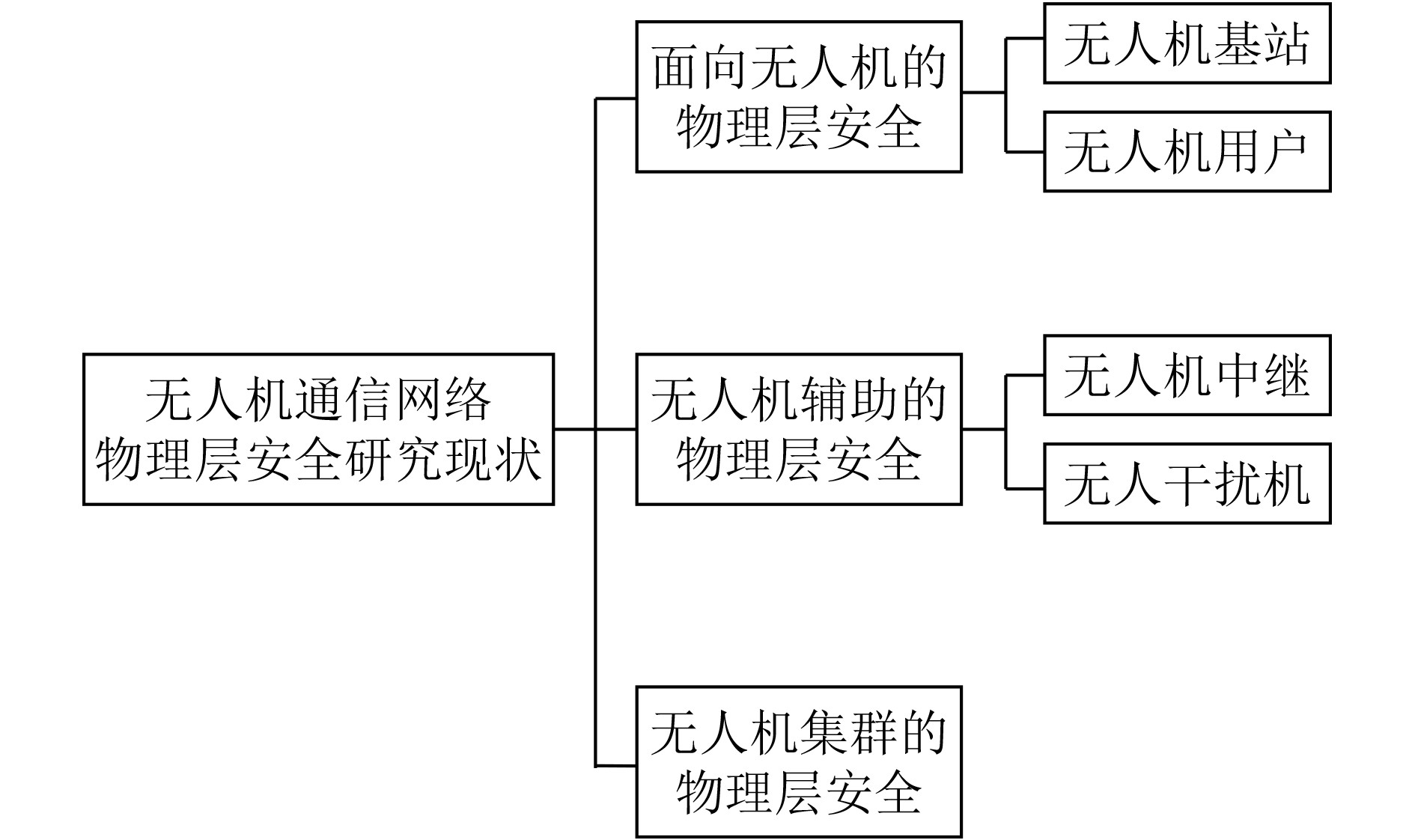
| [1] |
IMT-2020(5G)推进组. 5G无人机应用白皮书[R]. 2018.
|
| [2] |
王祥科, 刘志宏, 丛一睿, 等. 小型固定翼无人机集群综述和未来发展[J]. 航空学报, 2020, 41(4): 15–40. doi: 10.7527/S1000-6893.2019.23732WANG Xiangke, LIU Zhihong, CONG Yirui, et al. Miniature fixed-wing UAV swarms: Review and outlook[J]. Acta Aeronautica et Astronautica Sinica, 2020, 41(4): 15–40. doi: 10.7527/S1000-6893.2019.23732
|
| [3] |
ZHAO Nan, CHENG Fen, YU F R, et al. Caching UAV assisted secure transmission in hyper-dense networks based on interference alignment[J]. IEEE Transactions on Communications, 2018, 66(5): 2281–2294. doi: 10.1109/TCOMM.2018.2792014
|
| [4] |
MOZAFFARI M, SAAD W, BENNIS M, et al. A tutorial on UAVs for wireless networks: Applications, challenges, and open problems[J]. IEEE Communications Surveys & Tutorials, 2019, 21(3): 2334–2360. doi: 10.1109/COMST.2019.2902862
|
| [5] |
ZENG Yong, LYU J, and ZHANG Rui. Cellular-connected UAV: Potential, challenges, and promising technologies[J]. IEEE Wireless Communications, 2019, 26(1): 120–127. doi: 10.1109/MWC.2018.1800023
|
| [6] |
ZENG Yong, WU Qingqing, and ZHANG Rui. Accessing from the sky: A tutorial on UAV communications for 5G and beyond[J]. Proceedings of the IEEE, 2019, 107(12): 2327–2375. doi: 10.1109/JPROC.2019.2952892
|
| [7] |
SUN Xiaofang, NG D W K, DING Zhiguo, et al. Physical layer security in UAV systems: Challenges and opportunities[J]. IEEE Wireless Communications, 2019, 26(5): 40–47. doi: 10.1109/MWC.001.1900028
|
| [8] |
WU Qingqing, MEI Weidong, and ZHANG Rui. Safeguarding wireless network with UAVs: A physical layer security perspective[J]. IEEE Wireless Communications, 2019, 26(5): 12–18. doi: 10.1109/MWC.001.1900050
|
| [9] |
LI Bin, FEI Zesong, ZHANG Yan, et al. Secure UAV communication networks over 5G[J]. IEEE Wireless Communications, 2019, 26(5): 114–120. doi: 10.1109/MWC.2019.1800458
|
| [10] |
黄开枝, 王少禹, 许晓明, 等. 毫米波下行多用户系统安全混合波束成形算法[J]. 电子与信息学报, 2019, 41(4): 952–958. doi: 10.11999/jeit180713HUANG Kaizhi, WANG Shaoyu, XU Xiaoming, et al. Security hybrid beamforming algorithm for millimeter wave downlink multiuser system[J]. Journal of Electronics &Information Technology, 2019, 41(4): 952–958. doi: 10.11999/jeit180713
|
| [11] |
CAO Kunrui, WANG Buhong, DING Haiyang, et al. Improving physical layer security of uplink NOMA via energy harvesting jammers[J]. IEEE Transactions on Information Forensics and Security, 2021, 16: 786–799. doi: 10.1109/TIFS.2020.3023277
|
| [12] |
CAO Kunrui, WANG Buhong, DING Haiyang, et al. On the security enhancement of uplink NOMA systems with jammer selection[J]. IEEE Transactions on Communications, 2020, 68(9): 5747–5763. doi: 10.1109/TCOMM.2020.3003665
|
| [13] |
LIN Zhi, LIN Min, ZHU Weiping, et al. Robust secure beamforming for wireless powered cognitive satellite-terrestrial networks[J]. IEEE Transactions on Cognitive Communications and Networking, 2021, 7(2): 567–580. doi: 10.1109/TCCN.2020.3016096
|
| [14] |
黄开枝, 金梁, 陈亚军, 等. 无线物理层密钥生成技术发展及新的挑战[J]. 电子与信息学报, 2020, 42(10): 2330–2341. doi: 10.11999/JEIT200002HUANG Kaizhi, JIN Liang, CHEN Yajun, et al. Development of wireless physical layer key generation technology and new challenges[J]. Journal of Electronics &Information Technology, 2020, 42(10): 2330–2341. doi: 10.11999/JEIT200002
|
| [15] |
MAMAGHANI M T and HONG Yi. Joint trajectory and power allocation design for secure artificial noise aided UAV communications[J]. IEEE Transactions on Vehicular Technology, 2021, 70(3): 2850–2855. doi: 10.1109/TVT.2021.3057397
|
| [16] |
LI Sixian, DUO Bin, DI RENZO M, et al. Robust secure UAV communications with the aid of reconfigurable intelligent surfaces[J]. IEEE Transactions on Wireless Communications, 2021, 20(10): 6402–6417. doi: 10.1109/TWC.2021.3073746
|
| [17] |
CUI Miao, ZHANG Guangchi, WU Qingqing, et al. Robust trajectory and transmit power design for secure UAV communications[J]. IEEE Transactions on Vehicular Technology, 2018, 67(9): 9042–9046. doi: 10.1109/TVT.2018.2849644
|
| [18] |
ZHU Yongxu, ZHENG Gan, and FITCH M. Secrecy rate analysis of UAV-enabled mmWave networks using matérn hardcore point processes[J]. IEEE Journal on Selected Areas in Communications, 2018, 36(7): 1397–1409. doi: 10.1109/JSAC.2018.2825158
|
| [19] |
YE Jia, ZHANG Chao, LEI Hongjiang, et al. Secure UAV-to-UAV systems with spatially random UAVs[J]. IEEE Wireless Communications Letters, 2019, 8(2): 564–567. doi: 10.1109/LWC.2018.2879842
|
| [20] |
黄开枝, 金梁, 钟州. 5G物理层安全技术——以通信促安全[J]. 中兴通讯技术, 2019, 25(4): 43–49. doi: 10.12142/ZTETJ.201904008HUANG Kaizhi, JIN Liang, and ZHONG Zhou. 5G physical layer security technology: Enhancing security by communication[J]. ZTE Technology Journal, 2019, 25(4): 43–49. doi: 10.12142/ZTETJ.201904008
|
| [21] |
WYNER A D. The wire-tap channel[J]. The Bell System Technical Journal, 1975, 54(8): 1355–1387. doi: 10.1002/j.1538-7305.1975.tb02040.x
|
| [22] |
GERBRACHT S, SCHEUNERT C, and JORSWIECK E A. Secrecy outage in MISO systems with partial channel information[J]. IEEE Transactions on Information Forensics and Security, 2012, 7(2): 704–716. doi: 10.1109/TIFS.2011.2181946
|
| [23] |
GOEL S and NEGI R. Guaranteeing secrecy using artificial noise[J]. IEEE Transactions on Wireless Communications, 2008, 7(6): 2180–2189. doi: 10.1109/TWC.2008.060848
|
| [24] |
LV Lu, DING Zhiguo, NI Qiang, et al. Secure MISO-NOMA transmission with artificial noise[J]. IEEE Transactions on Vehicular Technology, 2018, 67(7): 6700–6705. doi: 10.1109/TVT.2018.2811733
|
| [25] |
HUANG Yuzhen, WANG Jinlong, ZHONG Caijun, et al. Secure transmission in cooperative relaying networks with multiple antennas[J]. IEEE Transactions on Wireless Communications, 2016, 15(10): 6843–6856. doi: 10.1109/TWC.2016.2591940
|
| [26] |
任品毅, 唐晓. 面向5G的物理层安全技术综述[J]. 北京邮电大学学报, 2018, 41(5): 69–77. doi: 10.13190/j.jbupt.2018-205REN Pinyi and TANG Xiao. A review on physical layer security techniques for 5G[J]. Journal of Beijing University of Posts and Telecommunications, 2018, 41(5): 69–77. doi: 10.13190/j.jbupt.2018-205
|
| [27] |
WANG Ning, WANG P, ALIPOUR-FANID A, et al. Physical-layer security of 5G wireless networks for IoT: Challenges and opportunities[J]. IEEE Internet of Things Journal, 2019, 6(5): 8169–8181. doi: 10.1109/JIOT.2019.2927379
|
| [28] |
WU Yongpeng, KHISTI A, XIAO Chengshan, et al. A survey of physical layer security techniques for 5G wireless networks and challenges ahead[J]. IEEE Journal on Selected Areas in Communications, 2018, 36(4): 679–695. doi: 10.1109/JSAC.2018.2825560
|
| [29] |
TIAN Xiaowen, LIU Qian, WANG Zihuan, et al. Secure hybrid beamformers design in mmWave MIMO wiretap systems[J]. IEEE Systems Journal, 2020, 14(1): 548–559. doi: 10.1109/JSYST.2019.2923819
|
| [30] |
CAO Kunrui, WANG Buhong, DING Haiyang, et al. Secure transmission designs for NOMA systems against internal and external eavesdropping[J]. IEEE Transactions on Information Forensics and Security, 2020, 15: 2930–2943. doi: 10.1109/TIFS.2020.2980202
|
| [31] |
LI Xinrui, WANG Wei, ZHANG Miao, et al. Robust secure beamforming for SWIPT-aided relay systems with full-duplex receiver and imperfect CSI[J]. IEEE Transactions on Vehicular Technology, 2020, 69(2): 1867–1878. doi: 10.1109/TVT.2019.2961449
|
| [32] |
CAO Kunrui, WANG Buhong, DING Haiyang, et al. Achieving reliable and secure communications in wireless-powered NOMA systems[J]. IEEE Transactions on Vehicular Technology, 2021, 70(2): 1978–1983. doi: 10.1109/TVT.2021.3053093
|
| [33] |
LI Yupeng, ZHANG Rongqing, ZHANG Jianhua, et al. Cooperative jamming via spectrum sharing for secure UAV communications[J]. IEEE Wireless Communications Letters, 2020, 9(3): 326–330. doi: 10.1109/LWC.2019.2953725
|
| [34] |
SUN Xiaoli, YANG Weiwei, CAI Yueming, et al. Secure MmWave UAV-enabled SWIPT networks based on random frequency diverse arrays[J]. IEEE Internet of Things Journal, 2021, 8(1): 528–540. doi: 10.1109/JIOT.2020.3005984
|
| [35] |
WANG Wei, TANG Jie, ZHAO Nan, et al. Joint precoding optimization for secure SWIPT in UAV-Aided NOMA networks[J]. IEEE Transactions on Communications, 2020, 68(8): 5028–5040. doi: 10.1109/TCOMM.2020.2990994
|
| [36] |
SUN Xiaoli, YANG Weiwei, and CAI Yueming. Secure communication in NOMA- assisted millimeter- wave SWIPT UAV networks[J]. IEEE Internet of Things Journal, 2020, 7(3): 1884–1897. doi: 10.1109/JIOT.2019.2957021
|
| [37] |
FANG Sisai, CHEN Gaojie, and LI Yonghui. Joint optimization for secure intelligent reflecting surface assisted UAV networks[J]. IEEE Wireless Communications Letters, 2021, 10(2): 276–280. doi: 10.1109/LWC.2020.3027969
|
| [38] |
GUO Xufeng, CHEN Yuanbin, and WANG Ying. Learning-based robust and secure transmission for reconfigurable intelligent surface aided millimeter wave UAV communications[J]. IEEE Wireless Communications Letters, 2021, 10(8): 1795–1799. doi: 10.1109/LWC.2021.3081464
|
| [39] |
GAO Ying, TANG Hongying, LI Baoqing, et al. Joint trajectory and power design for UAV-enabled secure communications with No-Fly zone constraints[J]. IEEE Access, 2019, 7: 44459–44470. doi: 10.1109/ACCESS.2019.2908407
|
| [40] |
XU Dongfang, SUN Yan, NG D W K, et al. Multiuser MISO UAV communications in uncertain environments with No-Fly Zones: Robust trajectory and resource allocation design[J]. IEEE Transactions on Communications, 2020, 68(5): 3153–3172. doi: 10.1109/TCOMM.2020.2970043
|
| [41] |
CAI Yunlong, CUI Fangyu, SHI Qingjiang, et al. Dual-UAV-enabled secure communications: Joint trajectory design and user scheduling[J]. IEEE Journal on Selected Areas in Communications, 2018, 36(9): 1972–1985. doi: 10.1109/JSAC.2018.2864424
|
| [42] |
HUA Meng, WANG Yi, WU Qingqing, et al. Energy-efficient cooperative secure transmission in multi-UAV-enabled wireless networks[J]. IEEE Transactions on Vehicular Technology, 2019, 68(8): 7761–7775. doi: 10.1109/TVT.2019.2924180
|
| [43] |
GAO Ying, TANG Hongying, LI Baoqing, et al. Securing energy-constrained UAV communications against both internal and external eavesdropping[J]. IEEE Communications Letters, 2021, 25(3): 749–753. doi: 10.1109/LCOMM.2020.3036457
|
| [44] |
ZHOU Xiaobo, WU Qingqing, YAN Shihao, et al. UAV-enabled secure communications: Joint trajectory and transmit power optimization[J]. IEEE Transactions on Vehicular Technology, 2019, 68(4): 4069–4073. doi: 10.1109/TVT.2019.2900157
|
| [45] |
WANG Huiming and ZHANG Xu. UAV secure downlink NOMA transmissions: A secure users oriented perspective[J]. IEEE Transactions on Communications, 2020, 68(9): 5732–5746. doi: 10.1109/TCOMM.2020.3002268
|
| [46] |
ZHAO Nan, LI Yanxin, ZHANG Shun, et al. Security enhancement for NOMA-UAV networks[J]. IEEE Transactions on Vehicular Technology, 2020, 69(4): 3994–4005. doi: 10.1109/TVT.2020.2972617
|
| [47] |
MAMAGHANI M T and HONG Yi. Improving PHY-security of UAV-enabled transmission with wireless energy harvesting: Robust trajectory design and communications resource allocation[J]. IEEE Transactions on Vehicular Technology, 2020, 69(8): 8586–8600. doi: 10.1109/TVT.2020.2998060
|
| [48] |
CAI Yuanxin, WEI Zhiqiang, LI Ruide, et al. Joint trajectory and resource allocation design for energy-efficient secure UAV communication systems[J]. IEEE Transactions on Communications, 2020, 68(7): 4536–4553. doi: 10.1109/TCOMM.2020.2982152
|
| [49] |
LI An and ZHANG Wenjing. Mobile jammer-aided secure UAV communications via trajectory design and power control[J]. China Communications, 2018, 15(8): 141–151. doi: 10.1109/CC.2018.8438280
|
| [50] |
LI Ruide, WEI Zhiqiang, YANG Lei, et al. Resource allocation for secure multi-UAV communication systems with multi-eavesdropper[J]. IEEE Transactions on Communications, 2020, 68(7): 4490–4506. doi: 10.1109/TCOMM.2020.2983040
|
| [51] |
MIAO Jiansong and ZHENG Ziyuan. Cooperative jamming for secure UAV-enabled mobile relay system[J]. IEEE Access, 2020, 8: 48943–48957. doi: 10.1109/ACCESS.2020.2980242
|
| [52] |
XIAO Lin, XU Yu, YANG Dingcheng, et al. Secrecy energy efficiency maximization for UAV-enabled mobile relaying[J]. IEEE Transactions on Green Communications and Networking, 2020, 4(1): 180–193. doi: 10.1109/TGCN.2019.2949802
|
| [53] |
SUN Xiaoli, YANG Weiwei, CAI Yueming, et al. Physical layer security in millimeter wave SWIPT UAV-based relay networks[J]. IEEE Access, 2019, 7: 35851–35862. doi: 10.1109/ACCESS.2019.2904856
|
| [54] |
XIAO Liang, LU Xiaozhen, XU Dongjin, et al. UAV relay in VANETs against smart jamming with reinforcement learning[J]. IEEE Transactions on Vehicular Technology, 2018, 67(5): 4087–4097. doi: 10.1109/TVT.2018.2789466
|
| [55] |
TUAN V P, SANG N Q, and KONG H Y. Secrecy capacity maximization for untrusted UAV-assisted cooperative communications with wireless information and power transfer[J]. Wireless Networks, 2020, 26(4): 2999–3010. doi: 10.1007/s11276-020-02255-w
|
| [56] |
SUN Xiaoli, YANG Weiwei, CAI Yueming, et al. Secure transmissions in millimeter wave SWIPT UAV-based relay networks[J]. IEEE Wireless Communications Letters, 2019, 8(3): 785–788. doi: 10.1109/LWC.2019.2892771
|
| [57] |
BAO Tingnan, YANG Hongchuan, and HASNA M O. Secrecy performance analysis of UAV-assisted relaying communication systems[J]. IEEE Transactions on Vehicular Technology, 2020, 69(1): 1122–1126. doi: 10.1109/TVT.2019.2952525
|
| [58] |
YUAN Quansheng, HU Yongjiang, WANG Changlong, et al. Joint 3D beamforming and trajectory design for UAV-enabled mobile relaying system[J]. IEEE Access, 2019, 7: 26488–26496. doi: 10.1109/ACCESS.2019.2898995
|
| [59] |
DONG Runze, WANG Buhong, CAO Kunrui, et al. Securing transmission for UAV swarm-enabled communication network[J]. IEEE Systems Journal, To be published.
|
| [60] |
DONG Runze, WANG Buhong, and CAO Kunrui. Security enhancement of UAV swarm enabled relaying systems with joint beamforming and resource allocation[J]. China Communications, 2021, 18(9): 71–87. doi: 10.23919/JCC.2021.09.007
|
| [61] |
YAO Jianping and XU Jie. Joint 3D maneuver and power adaptation for secure UAV communication with CoMP reception[J]. IEEE Transactions on Wireless Communications, 2020, 19(10): 6992–7006. doi: 10.1109/TWC.2020.3007648
|
| [62] |
WANG Xuanxuan, FENG Wei, CHEN Yunfei, et al. UAV swarm-enabled aerial CoMP: A physical layer security perspective[J]. IEEE Access, 2019, 7: 120901–120916. doi: 10.1109/ACCESS.2019.2936680
|
| [63] |
LIU Hongwu, YOO S J, and KWAK K S. Opportunistic relaying for low-altitude UAV swarm secure communications with multiple eavesdroppers[J]. Journal of Communications and Networks, 2018, 20(5): 496–508. doi: 10.1109/JCN.2018.000074
|
| [64] |
XU Yifan, REN Guochun, CHEN Jin, et al. A one-leader multi-follower bayesian-stackelberg game for anti-jamming transmission in UAV communication networks[J]. IEEE Access, 2018, 6: 21697–21709. doi: 10.1109/ACCESS.2018.2828033
|
| [65] |
WANG Wei, LI Xinrui, ZHANG Miao, et al. Energy-constrained UAV-assisted secure communications with position optimization and cooperative jamming[J]. IEEE Transactions on Communications, 2020, 68(7): 4476–4489. doi: 10.1109/TCOMM.2020.2989462
|
| [66] |
SUN Guen, LI Na, TAO Xiaofeng, et al. Power allocation in UAV-enabled relaying systems for secure communications[J]. IEEE Access, 2019, 7: 119009–119017. doi: 10.1109/ACCESS.2019.2932780
|
| [67] |
ZHOU Yifan, ZHOU Fuhui, ZHOU Huilin, et al. Robust trajectory and transmit power optimization for secure UAV-enabled cognitive radio networks[J]. IEEE Transactions on Communications, 2020, 68(7): 4022–4034. doi: 10.1109/TCOMM.2020.2979977
|
| [68] |
DONG Runze, WANG Buhong, and CAO Kunrui. Deep learning driven 3D robust beamforming for secure communication of UAV systems[J]. IEEE Wireless Communications Letters, 2021, 10(8): 1643–1647. doi: 10.1109/LWC.2021.3075996
|
| [69] |
WU Huici, WEN Yang, ZHANG Jiazhen, et al. Energy-efficient and secure air-to-ground communication with jittering UAV[J]. IEEE Transactions on Vehicular Technology, 2020, 69(4): 3954–3967. doi: 10.1109/TVT.2020.2971520
|
| [70] |
ZHOU Yi, YEOH P L, CHEN He, et al. Improving physical layer security via a UAV friendly jammer for unknown eavesdropper location[J]. IEEE Transactions on Vehicular Technology, 2018, 67(11): 11280–11284. doi: 10.1109/TVT.2018.2868944
|
| [71] |
SUN Yan, XU Dongfang, NG D W K, et al. Optimal 3D-trajectory design and resource allocation for solar-powered UAV communication systems[J]. IEEE Transactions on Communications, 2019, 67(6): 4281–4298. doi: 10.1109/TCOMM.2019.2900630
|
| [72] |
CHALLITA U, SAAD W, and BETTSTETTER C. Interference management for cellular-connected UAVs: A deep reinforcement learning approach[J]. IEEE Transactions on Wireless Communications, 2019, 18(4): 2125–2140. doi: 10.1109/TWC.2019.2900035
|
| [73] |
郝万明, 孙继威, 孙钢灿, 等. 基于非正交多址接入的移动边缘计算安全节能联合资源分配[J]. 电子与信息学报, 2021, 43(12): 3580–3587. doi: 10.11999/JEIT200872HAO Wanming, SUN Jiwei, SUN Gangcan, et al. Secure energy-efficient resource allocation in mobile edge computing based on non-orthogonal multiple access[J]. Journal of Electronics &Information Technology, 2021, 43(12): 3580–3587. doi: 10.11999/JEIT200872
|
| [74] |
ZHOU Yi, PAN Cunhua, YEOH P L, et al. Secure communications for UAV-enabled mobile edge computing systems[J]. IEEE Transactions on Communications, 2020, 68(1): 376–388. doi: 10.1109/TCOMM.2019.2947921
|
| [75] |
WANG Wen, TIAN Hui, and NI Wanli. Secrecy performance analysis of IRS-aided UAV relay system[J]. IEEE Wireless Communications Letters, 2021, 10(12): 2693–2697. doi: 10.1109/LWC.2021.3112752
|
| [76] |
WANG Qian, CHEN Zhi, MEI Weidong, et al. Improving physical layer security using UAV-enabled mobile relaying[J]. IEEE Wireless Communications Letters, 2017, 6(3): 310–313. doi: 10.1109/LWC.2017.2680449
|
| [77] |
YE Hao, LI G Y, and JUANG B H. Power of deep learning for channel estimation and signal detection in OFDM systems[J]. IEEE Wireless Communications Letters, 2018, 7(1): 114–117. doi: 10.1109/LWC.2017.2757490
|
| [78] |
ZENG Yong, XU Xiaoli, JIN Shi, et al. Simultaneous navigation and radio mapping for cellular-connected UAV with deep reinforcement learning[J]. IEEE Transactions on Wireless Communications, 2021, 20(7): 4205–4220. doi: 10.1109/TWC.2021.3056573
|
| [79] |
FENG Keming, WANG Qisheng, LI Xiao, et al. Deep reinforcement learning based intelligent reflecting surface optimization for MISO communication systems[J]. IEEE Wireless Communications Letters, 2020, 9(5): 745–749. doi: 10.1109/LWC.2020.2969167
|
| [80] |
MISMAR F B, EVANS B L, and ALKHATEEB A. Deep reinforcement learning for 5G networks: Joint beamforming, power control, and interference coordination[J]. IEEE Transactions on Communications, 2020, 68(3): 1581–1592. doi: 10.1109/TCOMM.2019.2961332
|
| [81] |
ZHANG Shun, LI Muye, JIAN Mengnan, et al. AIRIS: Artificial intelligence enhanced signal processing in reconfigurable intelligent surface communications[J]. China Communications, 2021, 18(7): 158–171. doi: 10.23919/JCC.2021.07.013
|
| [82] |
ZHANG Yu, MOU Zhiyu, GAO Feifei, et al. UAV-enabled secure communications by multi-agent deep reinforcement learning[J]. IEEE Transactions on Vehicular Technology, 2020, 69(10): 11599–11611. doi: 10.1109/TVT.2020.3014788
|





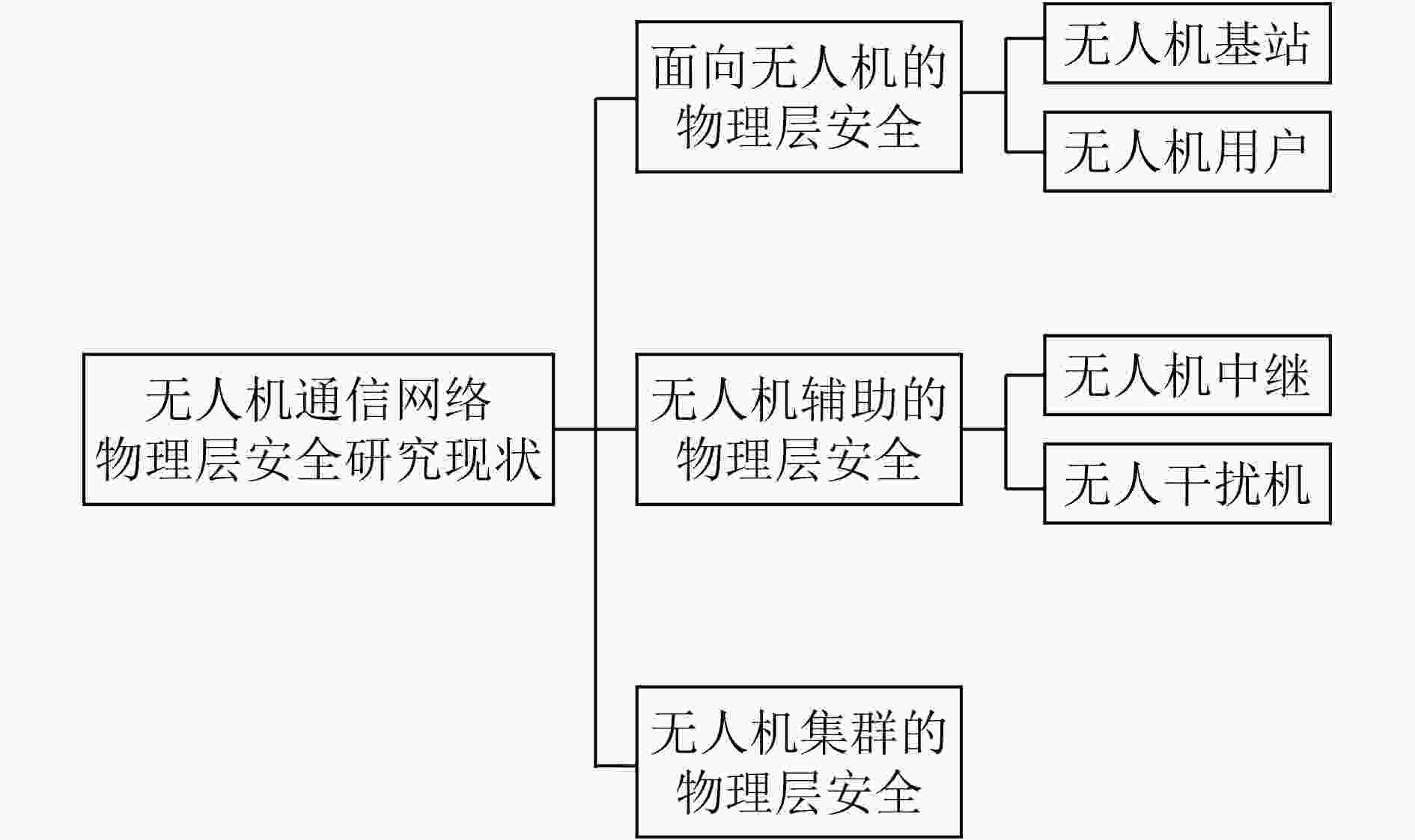
 下载:
下载: