Access Control Policy Generation Method Based on Access Control Logs
-
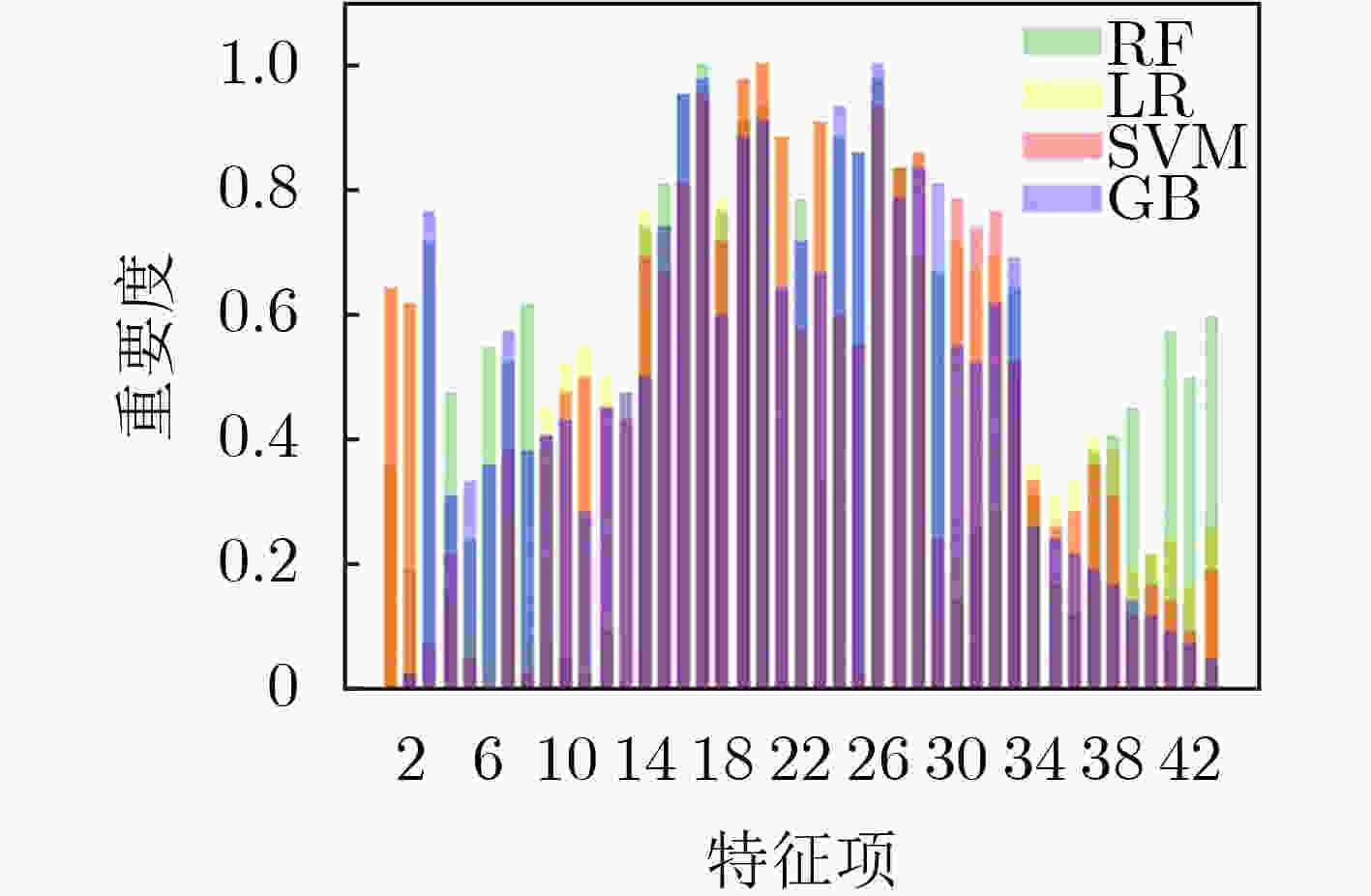
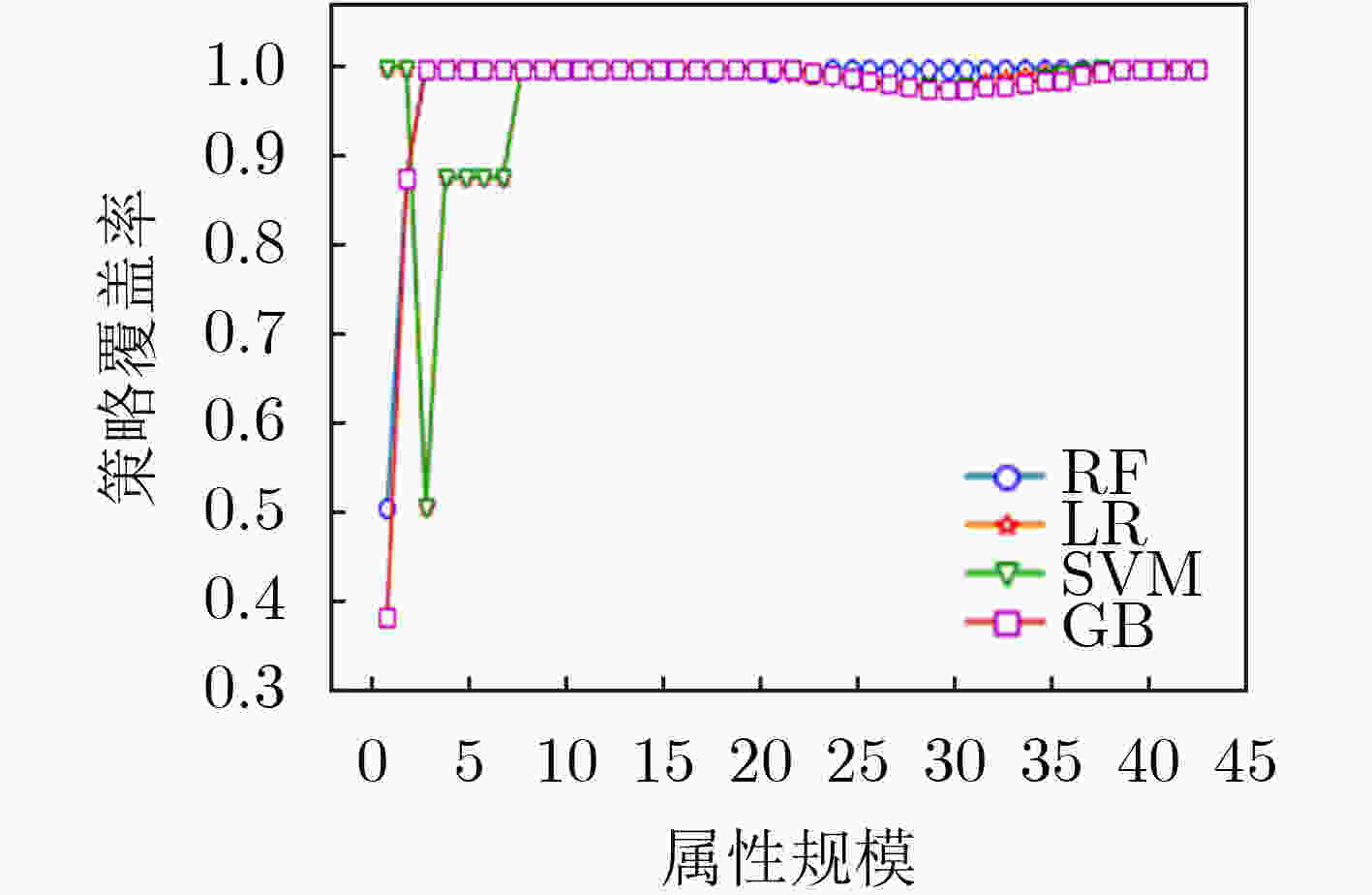
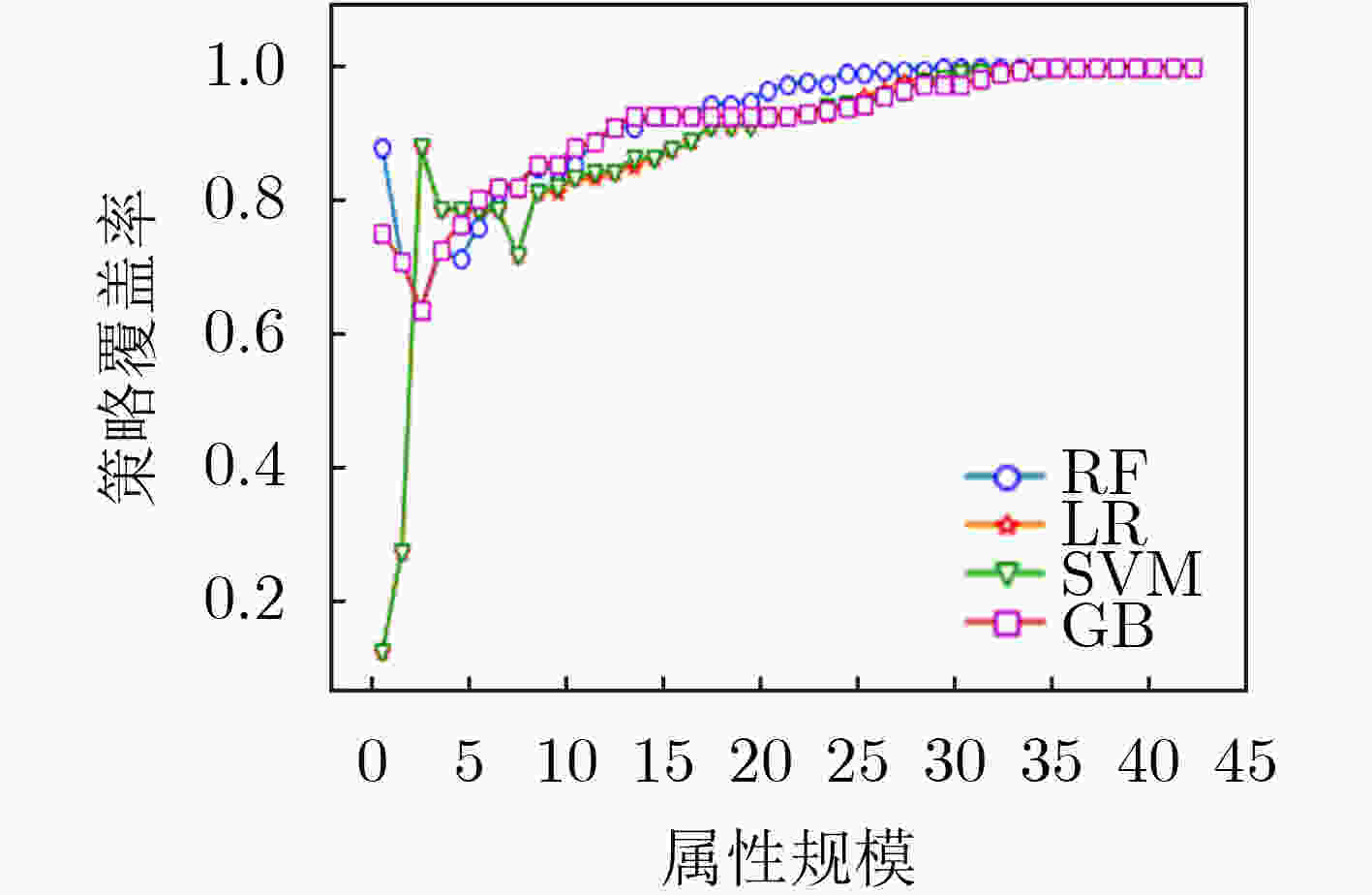
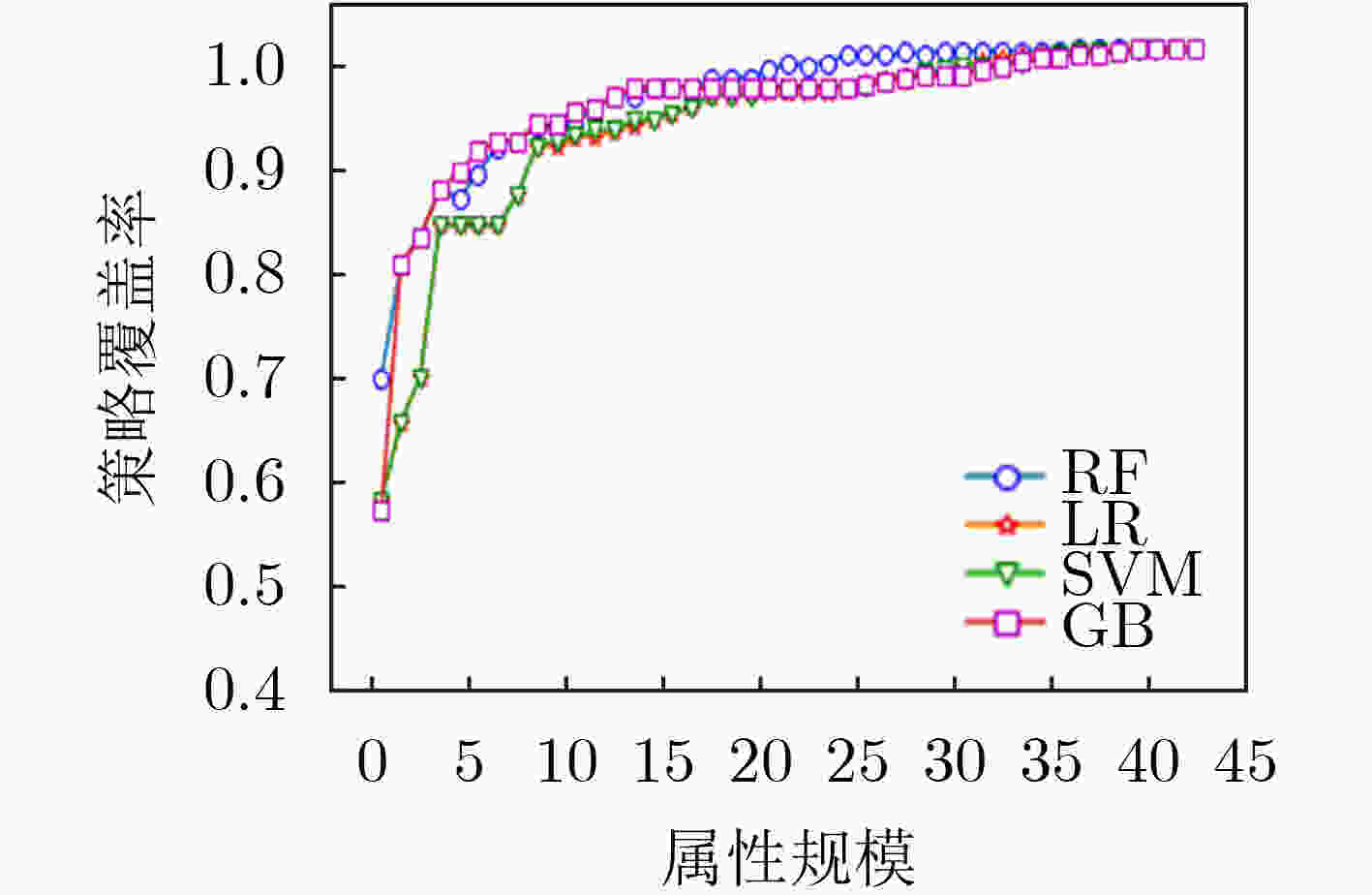
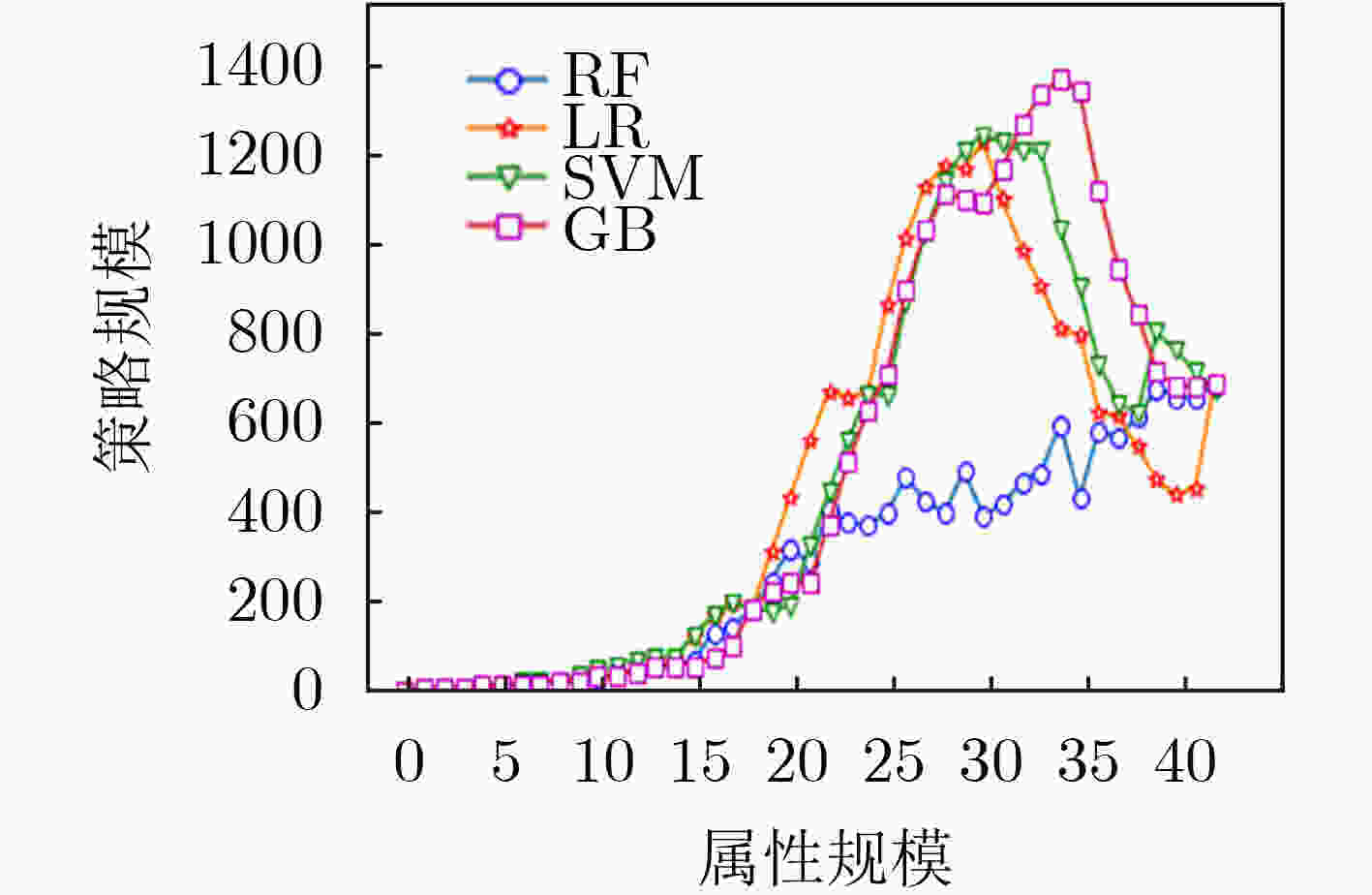
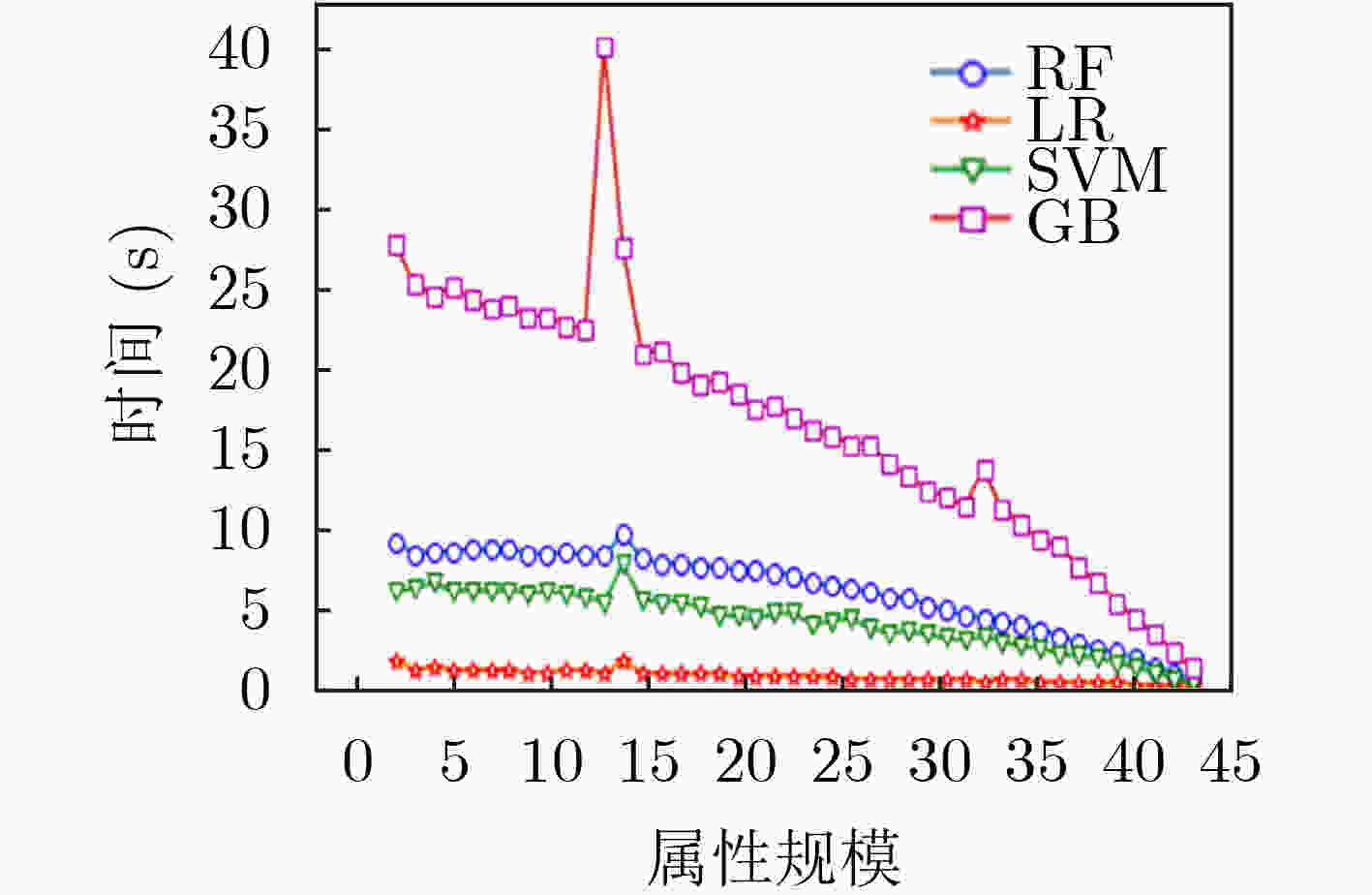
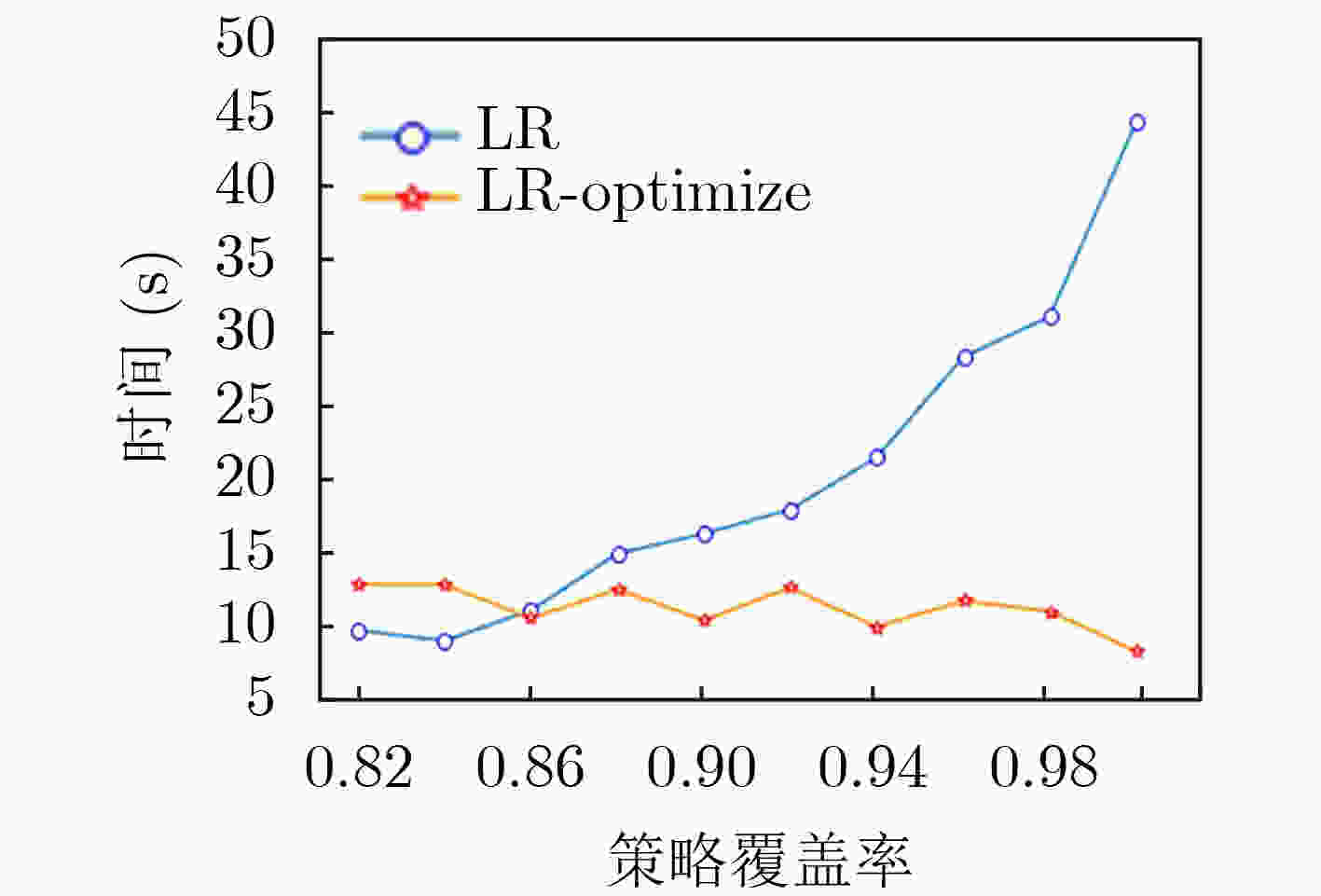
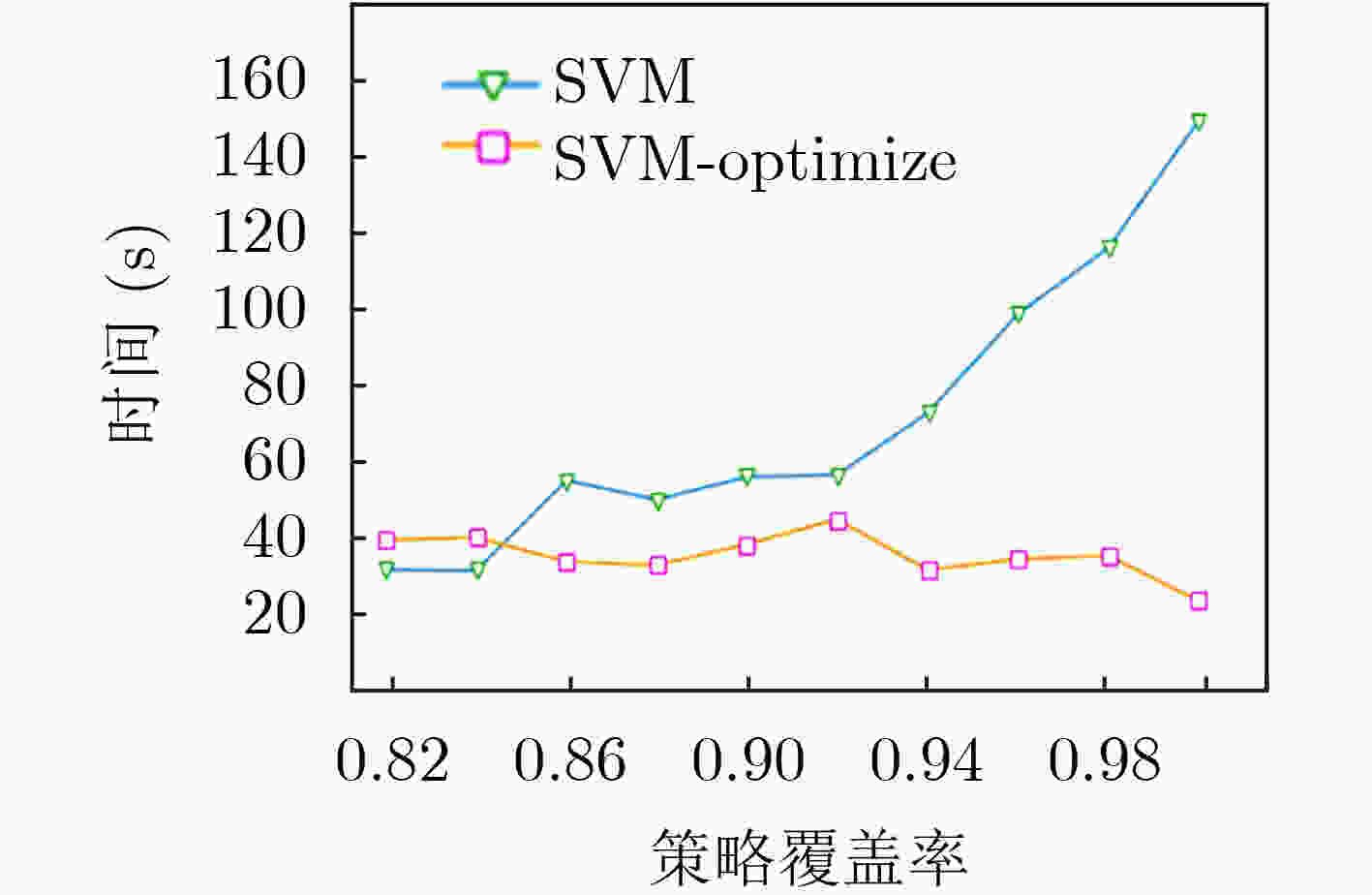
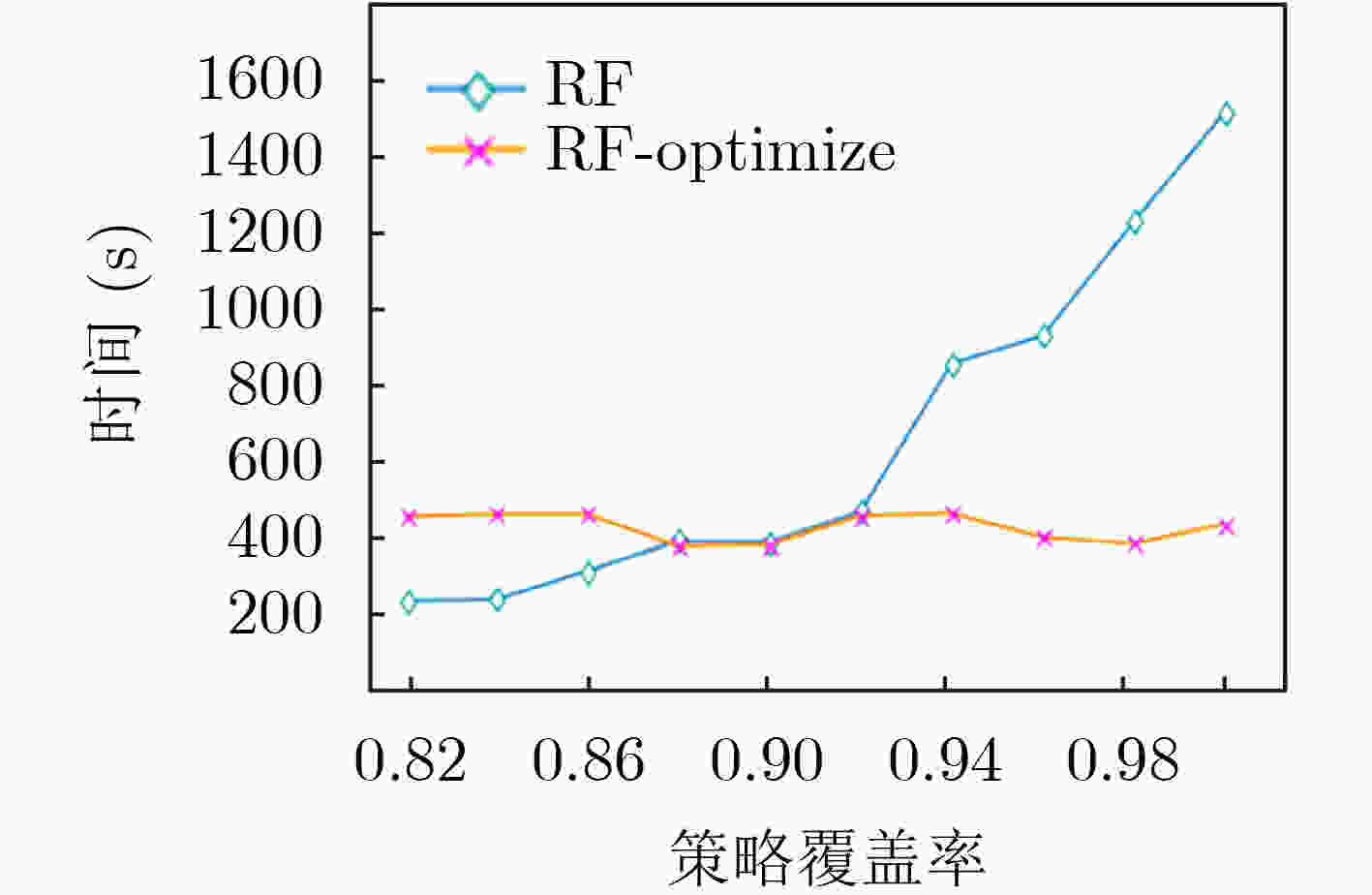
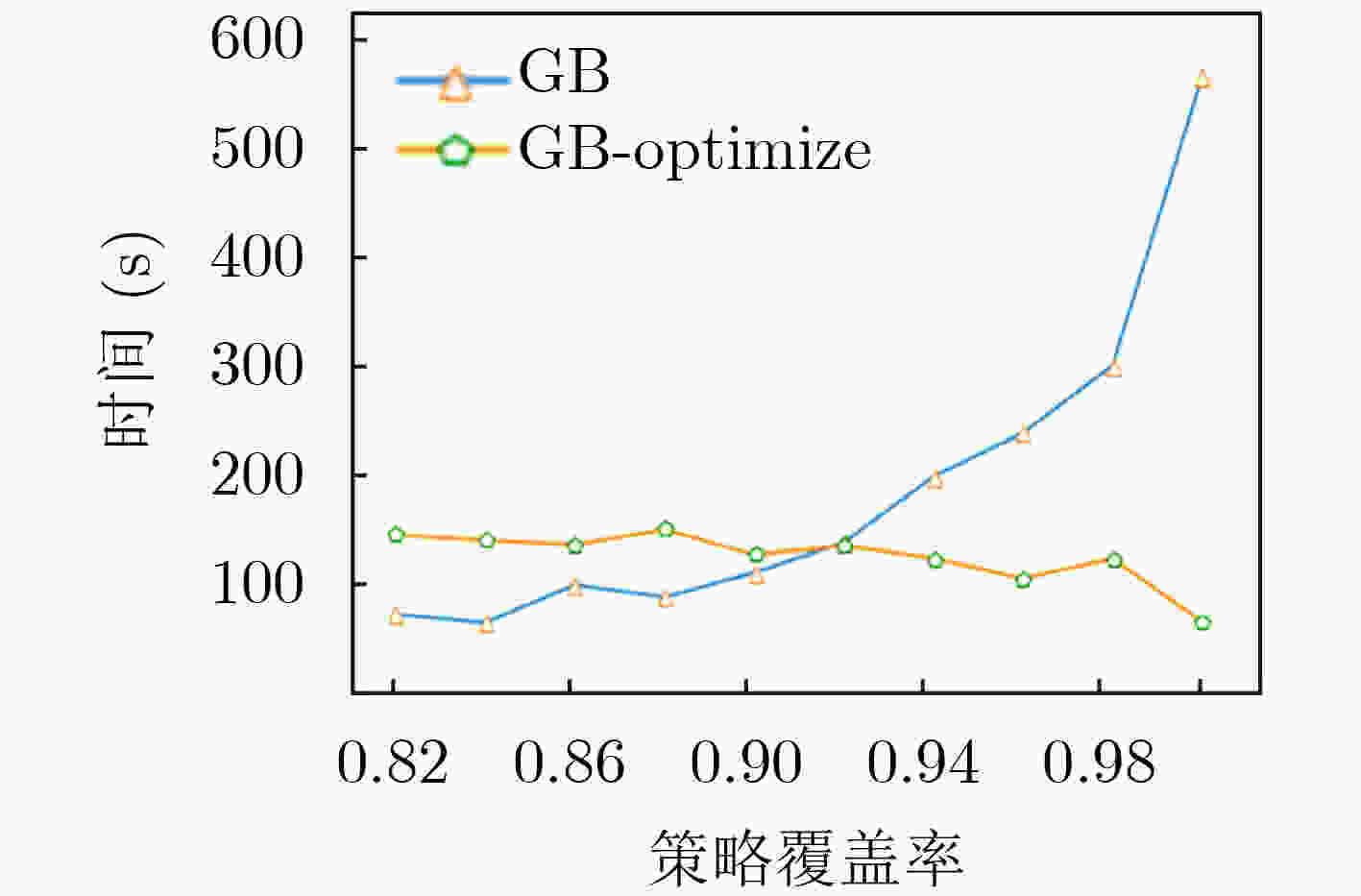
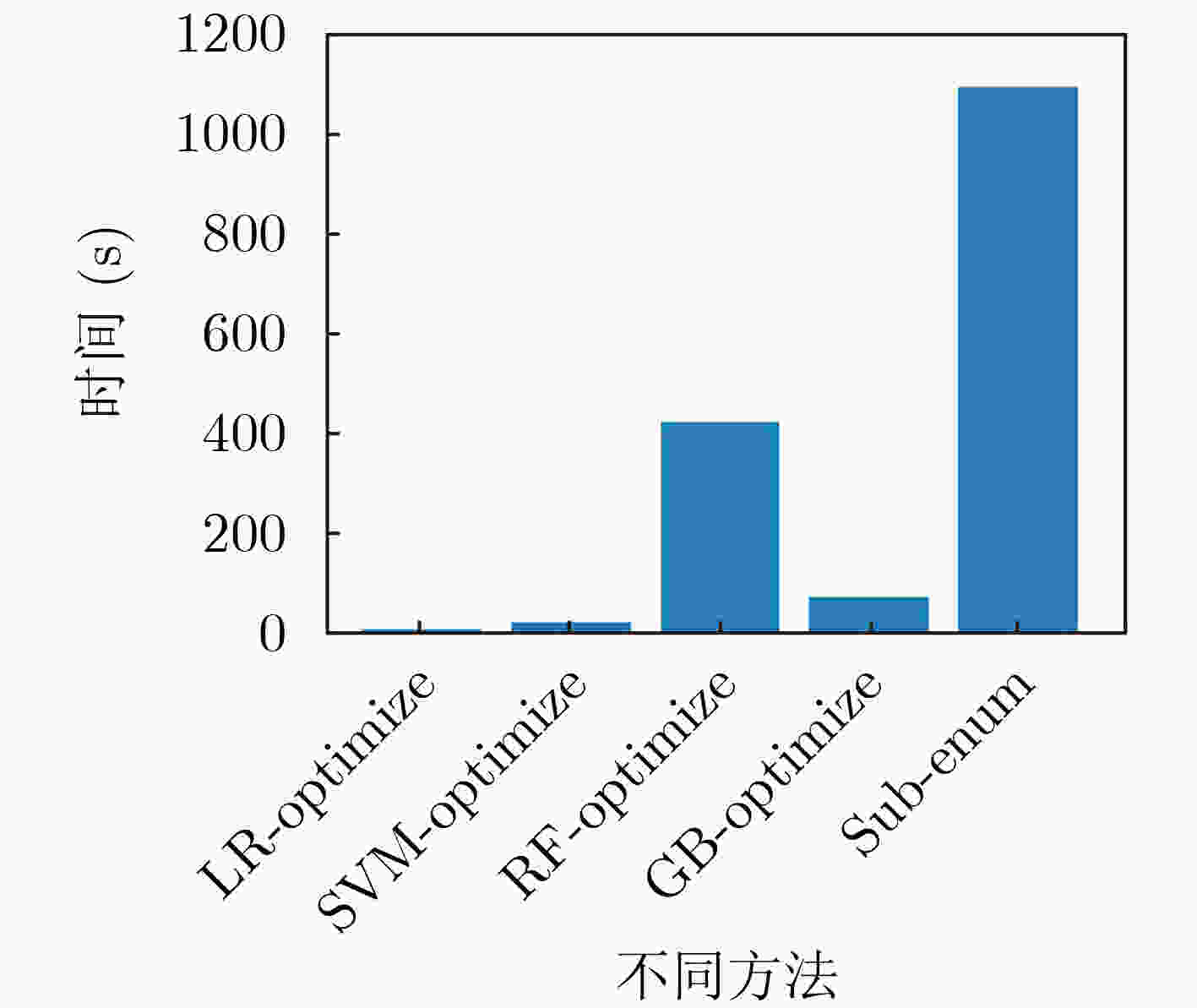
摘要: 为解决其他访问控制机制向基于属性的访问控制机制迁移过程中所面临的策略生成问题,该文提出一种基于访问控制日志的访问控制策略生成方法,利用基于机器学习分类器的递归属性消除法实现策略属性的选择,基于信息不纯度从日志记录中提炼出蕴含的属性-权限关系,结合实体属性选择的结果,构建策略结构树,实现基于属性的访问控制(ABAC)策略的生成,并设计了基于二分搜索的策略生成优化算法实现对最优策略生成结果的快速计算。实验结果表明,只需原始实体属性集中32.56%的属性信息即可实现对日志中95%的策略覆盖,并且能够将策略规模压缩为原有规模的33.33%,证实了该方案的有效性,能够为ABAC策略管理提供有力支撑。Abstract: To overcome the policy generation problem faced by other access control mechanism in the process of migration to attribution-based access control mechanism, an access control policy generation method based on access control log is proposed. The recursive attribute elimination method is utilized to implement attribute selection. Based on information impurity, the attribute-permission relationship is extracted from the access control logs, and the result of entity attribute selection is combined to build the policy structure tree, so as to realize the policy generation of Attribute-Based Access Control (ABAC). In addition, an optimization algorithm based on binary search is designed to calculate quickly the parameters of the optimal policy generation. The experimental results show that only 32.56% of the attribute information in the original entity attribute set can be used to cover 95% of the permission in the log. The size of the policies is also reduced to 33.33% of the original size. The effectiveness of the scheme is proved.
-
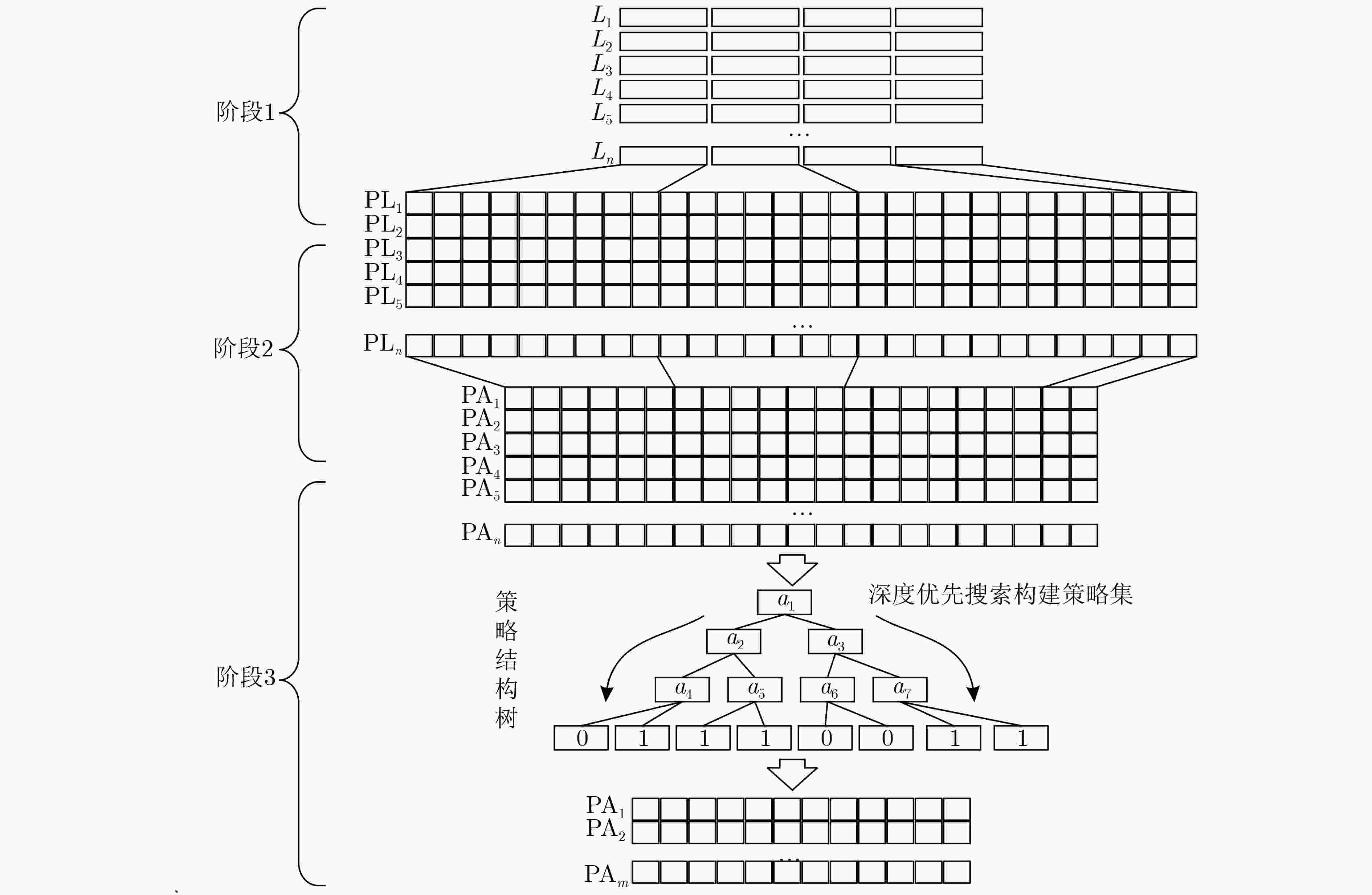
表 1 属性选择算法
输入:C={c1, c2, ···, cm} //候选属性集,n //目标属性值L={l1,
l2, ···, ln} //访问控制日志集, classifier//分类器输出:A*={a1, a2, ···, an} //访问控制策略生成属性集 (1) A*={}, Score = dict() (2) uncovAttr=C.copy() (3) while (uncovAttr is not Empty) (4) M=train(C, L, classifier)//基于分类训练日志数据 (5) I = sort(M)//对训练模型中使用的属性进行排序 (6) c*=Get_worst(I)//得到分量最低的属性 (7) uncovAttr= uncovAttr.delete{ c*}//从uncovAttr中删
除属性(8) Score[c*] = c*.score//在字典Score中删除属性对应的分值 (9) end while (10) A* = Generate_n_attribute(Score, n)//从Score中挑选出
分值最高的n个属性(11)//A is composed of n candidate attributes with the highest
score in Score(12) return A* 表 2 策略生成算法
输入: P0={p1, p2, ···, pm} //日志原始策略集A={a1, a2, ···, an}
//访问控制策略生成属性集输出: PolicyTree //以属性node为节点的策略树 (1) node = Choose(A), PolicyTree = Init()//生成属性节点node,
初始化策略树(2) if result(P0, node) is same then //若node对应所有P0判决结
果相同(3) node.type = val; return (4) //将node标记为val类型叶节点 (5) end if (6) if A = null or value(P0) is same on A then //若P0中判决结
果相同(7) node.type = valmax; return (8) // valmax是P0中数量最多的类 (9) end if (10) $A' $ = SelectBest(A) //从A中选择最优属性子集 (11) for ai in $A' $ do (12) nodebranch=Generate(ai), $P' $= subset(P0, ai) (13) //生成分支节点和分支节点对应的策略子集 (14) if $P' $ = null then (15) nodebranch.type = valmax; (16) else (17) nodebranch= PTG-DT($P' $, A\{$A' $}); (18) end if (19)end for (20)return PolicyTree 表 3 策略生成优化算法
输入:P0={p1, p2, ···, pm} //日志原始策略集, classifier//分类
器C={c1, c2, ···, cm} //候选属性集, Target //目标策略覆盖率输出:FinalPolicySet //最终策略集 (1) begin=0, end=len(C) //计算候选属性数目, FinalPolicySet
={}(2) mid=(begin+end)/2 (3) A=AG-RFE(C, L, classifier, mid) //计算属性集 (4) PT=PTG-DT(P0, A) //生成策略结构树 (5) if coverage(PT, P0) > Target then (6) end=mid (7) mid=(begin+mid)/2 (8) PQO-BS(mid) (9) else (10) begin=mid (11) mid=(mid+end)/2 (12) PQO-BS(mid) (13) end if (14) FinalPolicySet=Transfer(PT)//PT中由根节点到每个叶节
点路径上的所有属性构成基于属性的访问控制策略(15) return FinalPolicySet -
[1] 房梁, 殷丽华, 郭云川, 等. 基于属性的访问控制关键技术研究综述[J]. 计算机学报, 2017, 40(7): 1680–1698. doi: 10.11897/SP.J.1016.2017.01680FANG Liang, YIN Lihua, GUO Yunchuan, et al. A survey of key technologies in attribute-based access control scheme[J]. Chinese Journal of Computers, 2017, 40(7): 1680–1698. doi: 10.11897/SP.J.1016.2017.01680 [2] 刘敖迪, 杜学绘, 王娜, 等. 基于区块链的大数据访问控制机制[J]. 软件学报, 2019, 30(9): 2636–2654.LIU Aodi, DU Xuehui, WANG Na, et al. Blockchain-based access control mechanism for big data[J]. Journal of Software, 2019, 30(9): 2636–2654. [3] XU Zhongyuan and STOLLER S D. Mining attribute-based access control policies[J]. IEEE Transactions on Dependable and Secure Computing, 2015, 12(5): 533–545. doi: 10.1109/TDSC.2014.2369048 [4] Guide to Attribute Based Access Control (ABAC) Definition and Considerations[EB/OL]. NIST Special Publication 800–162. http://www.nist.gov/manuscript-publication-search.cfm?pub_id=915660,2014. [5] Market Trends: Cloud-based security services market[EB/OL]. https://www.gartner.com/doc/2607617, 2013. [6] LIU Aodi, DU Xuehui, and WANG Na. Access control role evolution mechanism for open computing environment[J]. Electronics, 2020, 9(3): 517. doi: 10.3390/electronics9030517 [7] BLUNDO C, CIMATO S, and SINISCALCHI L. PRUCC-RM: Permission-role-usage cardinality constrained role mining[C]. 2017 IEEE 41st Annual Computer Software and Applications Conference (COMPSAC), Turin, Italy, 2017: 149–154. [8] DONG Lijun, WANG Yi, LIU Ran, et al. Toward edge minability for role mining in bipartite networks[J]. Physica A:Statistical Mechanics and its Applications, 2016, 462: 274–286. doi: 10.1016/j.physa.2016.06.068 [9] VAVILIS S, EGNER A I, PETKOVIĆ M, et al. Role mining with missing values[C]. 2016 11th International Conference on Availability, Reliability and Security (ARES), Salzburg, Austria, 2016: 167–176. [10] MITRA B, SURAL S, VAIDYA J, et al. Mining temporal roles using many-valued concepts[J]. Computers & Security, 2016, 60: 79–94. [11] 周超, 任志宇, 毋文超. 基于形式概念分析的语义角色挖掘算法[J]. 计算机科学, 2018, 45(12): 117–122,129.ZHOU Chao, REN Zhiyu, and WU Wenchao. Semantic roles mining algorithms based on formal concept analysis[J]. Computer Science, 2018, 45(12): 117–122,129. [12] MEDVET E, BARTOLI A, CARMINATI B, et al. Evolutionary inference of attribute-based access control policies[C]. 8th International Conference on Evolutionary Multi-Criterion Optimization, Guimarães, Portugal, 2015: 351–365. [13] KARIMI L and JOSHI J. An unsupervised learning based approach for mining attribute based access control policies[C]. 2018 IEEE International Conference on Big Data (Big Data), Seattle, USA, 2018: 1427–1436. [14] IYER P and MASOUMZADEH A. Mining positive and negative attribute-based access control policy rules[C]. The 23nd ACM on Symposium on Access Control Models and Technologies, Indiana, USA, 2018: 161–172. [15] MOCANU D, TURKMEN F, and LIOTTA A. Towards ABAC policy mining from logs with deep learning[C]. The 18th International Multiconference, Slovenia, 2015. [16] NAROUEI M, KHANPOUR H, and TAKABI H. Identification of access control policy sentences from natural language policy documents[C]. 31st IFIP Annual Conference on Data and Applications Security and Privacy, Philadelphia, USA, 2017: 82–100. [17] NAROUEI M, KHANPOUR H, TAKABI H, et al. Towards a top-down policy engineering framework for attribute-based access control[C]. The 22nd ACM on Symposium on Access Control Models and Technologies, Indiana, USA, 2017: 103–114. [18] ALOHALY M, TAKABI H, and BLANCO E. A deep learning approach for extracting attributes of ABAC policies[C]. The 23nd ACM on Symposium on Access Control Models and Technologies, Indiana, USA, 2018: 137–148. [19] HUANG Xiaojuan, ZHANG Li, WANG Bangjun, et al. Feature clustering based support vector machine recursive feature elimination for gene selection[J]. Applied Intelligence, 2018, 48(3): 594–607. doi: 10.1007/s10489-017-0992-2 [20] RAO Haidi, SHI Xianzhang, RODRIGUE A K, et al. Feature selection based on artificial bee colony and gradient boosting decision tree[J]. Applied Soft Computing, 2019, 74: 634–642. doi: 10.1016/j.asoc.2018.10.036 [21] KUANG Wei, CHAN Y L, TSANG S H, et al. Machine learning-based fast intra mode decision for HEVC screen content coding via decision trees[J]. IEEE Transactions on Circuits and Systems for Video Technology, 2020, 30(5): 1481–1496. doi: 10.1109/TCSVT.2019.2903547 -





 下载:
下载: