Speech Information Hiding Method Based on Random Position Selection and Matrix Coding
-
摘要:
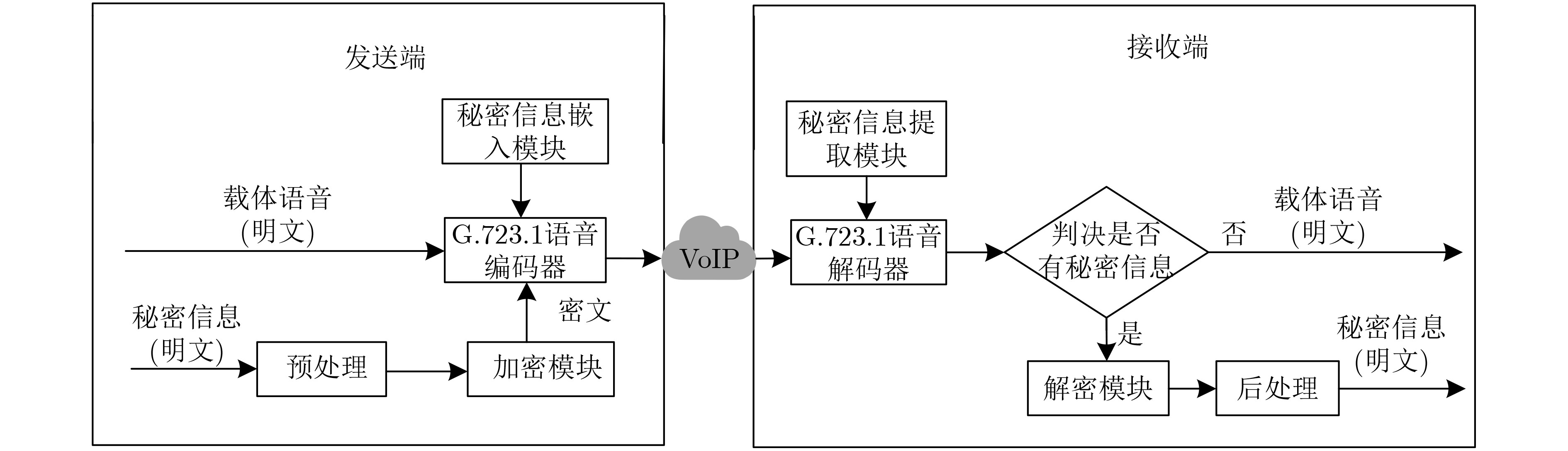
针对低速率语音编码问题,该文提出基于G.723.1编码标准的信息隐藏算法。在基音预测编码过程中,通过控制闭环基音周期(自适应码本)的搜索范围,该文结合随机位置选择方法(RPS)和矩阵编码方法(MCM),实现秘密信息的嵌入,在语音编码过程中实现了信息的隐藏。RPS方法的采用降低了载体码字之间的关联性,MCM方法的采用降低了载体的改变率。实验结果证明,该文算法下PESQ恶化率平均值最大为1.63%,隐蔽性良好。
-
关键词:
- 低速率语音编码 /
- G.723.1编码标准 /
- 基音预测 /
- 闭环基音周期
Abstract:For the low-rate speech encoding problem, an information hidden algorithm based on the G.723.1 coding standard is proposed. In the pitch prediction coding process, by controlling the search range of the closed-loop pitch period (adaptive codebook), combined with the Random Position Selection (RPS) method and the Matrix Coding Method (MCM), the secret information is embedded, which is implemented in the speech coding process. The adoption of the RPS method reduces the correlation between the carrier code-words, and the adoption of the MCM method reduces the rate of change of the carrier. The experimental results show that the average PESQ (Perceptual Evaluation of Speech Quality) deterioration rate under the algorithm is 1.63%, and the concealment is good.
-
表 1 发送方、接收方台式PC配置情况
处理器 内存 声卡 系统 Intel(R) Core(TM) i5-4590 CPU @ 3.30 GHz 4 GB Realtek High Definition Audio Windows 7专业版 Service Pack 1 表 2 本文隐藏算法的PESQ统计值
载密语音样本 未载密语音样本 PESQ改变率(%) 3 s语音样本 CSM CSW ESM ESW CSM CSW ESM ESW CSM CSW ESM ESW 平均值 3.4237 3.3440 3.4165 3.4750 3.4429 3.3995 3.4259 3.5193 –0.55 –1.63 –0.27 –1.20 最大值 3.8999 3.7815 4.0995 4.1015 3.8262 3.7406 3.8863 3.9458 1.93 1.09 5.49 3.94 最小值 2.9756 2.9615 2.9756 2.9022 3.0930 3.1701 3.1160 3.1265 –3.80 –6.58 –4.51 –7.17 10 s语音样本 CSM CSW ESM ESW CSM CSW ESM ESW CSM CSW ESM ESW 平均值 3.4095 3.3528 3.3990 3.3822 3.4218 3.3900 3.4102 3.4362 –0.37 –1.09 –0.33 –1.50 最大值 3.7954 3.7102 3.7614 3.8714 3.7406 3.6783 3.7406 3.8632 1.47 0.87 2.12 0.21 最小值 2.9965 2.9113 3.1003 2.9965 3.0590 3.0180 3.1123 3.0590 –2.00 –3.53 –1.20 –2.00 表 3 隐藏算法的PESQ统计对比(%)
表 4 语音帧处理时间统计对比(ms)
表 5 在满嵌入率下两种隐藏算法检测率(%)
隐藏方法 语音种类 样本时长(s) 0.1 0.2 0.3 0.4 0.5 0.6 0.7 0.8 0.9 1.0 2.0 3.0 4.0 5.0 6.0 文献[10]隐藏算法 英文 85.40 88.00 88.50 89.25 90.10 91.45 91.40 92.40 92.95 93.70 96.20 96.95 97.15 97.65 97.35 中文 86.80 88.65 90.20 90.50 91.20 92.25 93.10 94.25 94.70 94.05 96.80 97.20 98.15 97.75 97.95 文献[11]隐藏算法 英文 87.65 90.11 90.81 91.65 92.89 94.00 94.15 95.01 95.20 96.64 97.20 98.70 100.00 100.00 100.00 中文 90.70 92.95 94.00 94.55 95.79 96.83 97.16 98.22 98.30 98.89 99.16 99.99 100.00 100.00 100.00 本文隐藏算法 英文 43.20 46.43 46.95 47.33 48.39 49.51 49.44 50.36 51.64 51.93 54.67 55.68 55.92 56.04 55.94 中文 45.51 46.91 47.56 47.48 48.72 49.70 49.53 52.14 52.37 52.87 55.06 55.86 56.09 56.35 55.63 表 6 在不同嵌入率下3种隐藏算法检测率(%)
隐藏方法 语音种类 嵌入率(%) 10 20 30 40 50 60 70 80 90 100 文献[10]隐藏算法 英文 50.61 57.64 75.53 80.29 82.81 85.63 86.35 90.58 94.32 97.35 中文 51.93 58.49 75.28 80.56 82.49 85.27 87.92 92.56 95.63 97.95 文献[11]隐藏算法 英文 53.94 60.89 78.66 83.49 85.91 88.69 89.35 93.74 97.25 100.00 中文 54.53 61.67 79.55 84.88 86.77 89.55 91.83 95.66 98.55 100.00 本文隐藏算法 英文 16.32 17.52 30.87 39.48 41.16 44.15 45.62 48.12 52.61 55.94 中文 15.22 17.35 30.56 39.52 41.74 44.16 44.59 49.31 52.38 55.63 -
PETITCOLAS F A P, ANDERSON R J, and KUHN M G. Information hiding - a survey[J]. The IEEE, 1999, 87(7): 1062–1078. doi: 10.1109/5.771065 丁琦, 平西建. 基于脉冲位置参数统计特征的压缩域语音隐写分析[J]. 计算机科学, 2011, 38(1): 217–220. doi: 10.3969/j.issn.1002-137X.2011.01.051DING Qi and PING Xijian. Steganalysis of compressed speech based on statistics of pulse position parameters[J]. Computer Science, 2011, 38(1): 217–220. doi: 10.3969/j.issn.1002-137X.2011.01.051 DITTMANN J, HESSE D, and HILLERT R. Steganography and steganalysis in voice-over IP scenarios: Operational aspects and first experiences with a new steganalysis tool set[J]. SPIE, 2005, 5681: 607–618. TIAN Hui, SUN Jun, CHANG C C, et al. Detecting bitrate modulation-based covert voice-over-IP communication[J]. IEEE Communications Letters, 2018, 22(6): 1196–1199. doi: 10.1109/LCOMM.2018.2822804 TIAN Hui, SUN Jun, CHANG C C, et al. Hiding information into voice-over-IP streams using adaptive bitrate modulation[J]. IEEE Communications Letters, 2017, 21(4): 749–752. doi: 10.1109/LCOMM.2017.2659718 XIAO Bo, HUANG Yongfeng, and TANG Shanyu. An approach to information hiding in low bit-rate speech stream[C]. 2008 IEEE Global Telecommunications Conference, New Orleans, USA, 2008: 1–5. TIAN Hui, LIU Jin, and LI Songbin. Improving security of quantization-index-modulation steganography in low bit-rate speech streams[J]. Multimedia Systems, 2014, 20(2): 143–154. doi: 10.1007/s00530-013-0302-8 CHIANG Y K, TSAI P, and HUANG Fenglong. Codebook partition based steganography without member restriction[J]. Fundamenta Informaticae, 2008, 82(1/2): 15–27. LI Songbin, JIA Yizhen, and KUO C C J. Steganalysis of QIM steganography in low-bit-rate speech signals[J]. IEEE/ACM Transactions on Audio, Speech, and Language Processing, 2017, 25(5): 1011–1022. doi: 10.1109/TASLP.2017.2676356 HUANG Yongfeng, LIU Chenghao, TANG Shanyu, et al. Steganography integration into a low-bit rate speech codec[J]. IEEE Transactions on Information Forensics and Security, 2012, 7(6): 1865–1875. doi: 10.1109/TIFS.2012.2218599 LIU C, BAI S, and HUANG Y. An information hiding algorithm in G. 729a based on pith prediction[C]. The 10th National Academic Conference on Information Hiding and Multimedia Information Security, Beijing, China, 2012: 15–18. LIN Zinan, HUANG Yongfeng, and WANG Jilong. RNN-SM: Fast steganalysis of VoIP streams using recurrent neural network[J]. IEEE Transactions on Information Forensics and Security, 2018, 13(7): 1854–1868. doi: 10.1109/TIFS.2018.2806741 YANG Wanxia, TANG Shanyu, LI Miaoqi, et al. Steganalysis of low embedding rates LSB speech based on histogram moments in frequency domain[J]. Chinese Journal of Electronics, 2107, 26(6): 1254–1260. doi: 10.1049/cje.2017.09.026 WU Zhijun, Gao Wei, and YANG Wei. LPC parameters substitution for speech information hiding[J]. The Journal of China Universities of Posts and Telecommunications, 2009, 16(6): 103–112. doi: 10.1016/S1005-8885(08)60295-2 HUANG Yongfeng, TANG Shanyu, and YUAN Jian. Steganography in inactive frames of VoIP streams encoded by source codec[J]. IEEE Transactions on Information Forensics and Security, 2011, 6(2): 296–307. doi: 10.1109/TIFS.2011.2108649 李松斌, 贾已真, 付江云, 等. 基于码书关联网络的基音调制信息隐藏检测[J]. 计算机学报, 2014, 37(10): 2107–2117. doi: 10.3724/SP.J.1016.2014.02107LI Songbin, JIA Yizhen, FU Jiangyun, et al. Detection of pitch modulation information hiding based on codebook correlation network[J]. Chinese Journal of Computers, 2014, 37(10): 2107–2117. doi: 10.3724/SP.J.1016.2014.02107 TIAN Hui, JIANG Hong, ZHOU Ke, et al. Transparency-orientated encoding strategies for voice-over-IP steganography[J]. The Computer Journal, 2012, 55(6): 702–716. doi: 10.1093/comjnl/bxr111 WESTFELD A. F5-A steganographic algorithm: High capacity despite better steganalysis[C]. The 4th International Workshop on Information Hiding, Pittsburgh, USA, 2001: 289–302. ITU-T. ITU-T P.862 Perceptual evaluation of speech quality (PESQ): An objective method for end-to-end speech quality assessment of narrow-band telephone networks and speech codecs[S]. Geneva, Switzerland: International Telecommunications Union, 2001. -






 下载:
下载: