Core Link Aware Survivable Virtual Network Link Protection Method
-
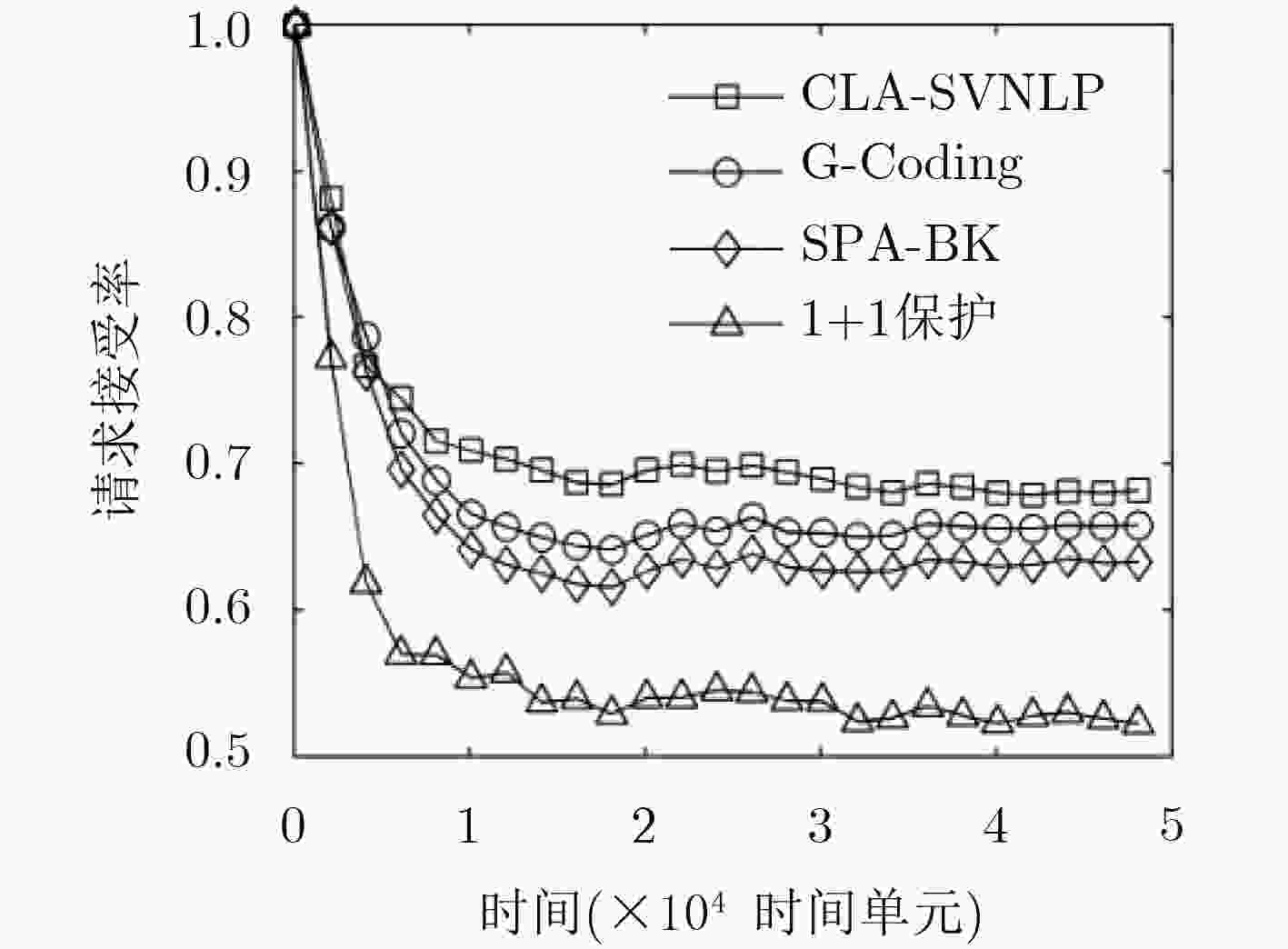
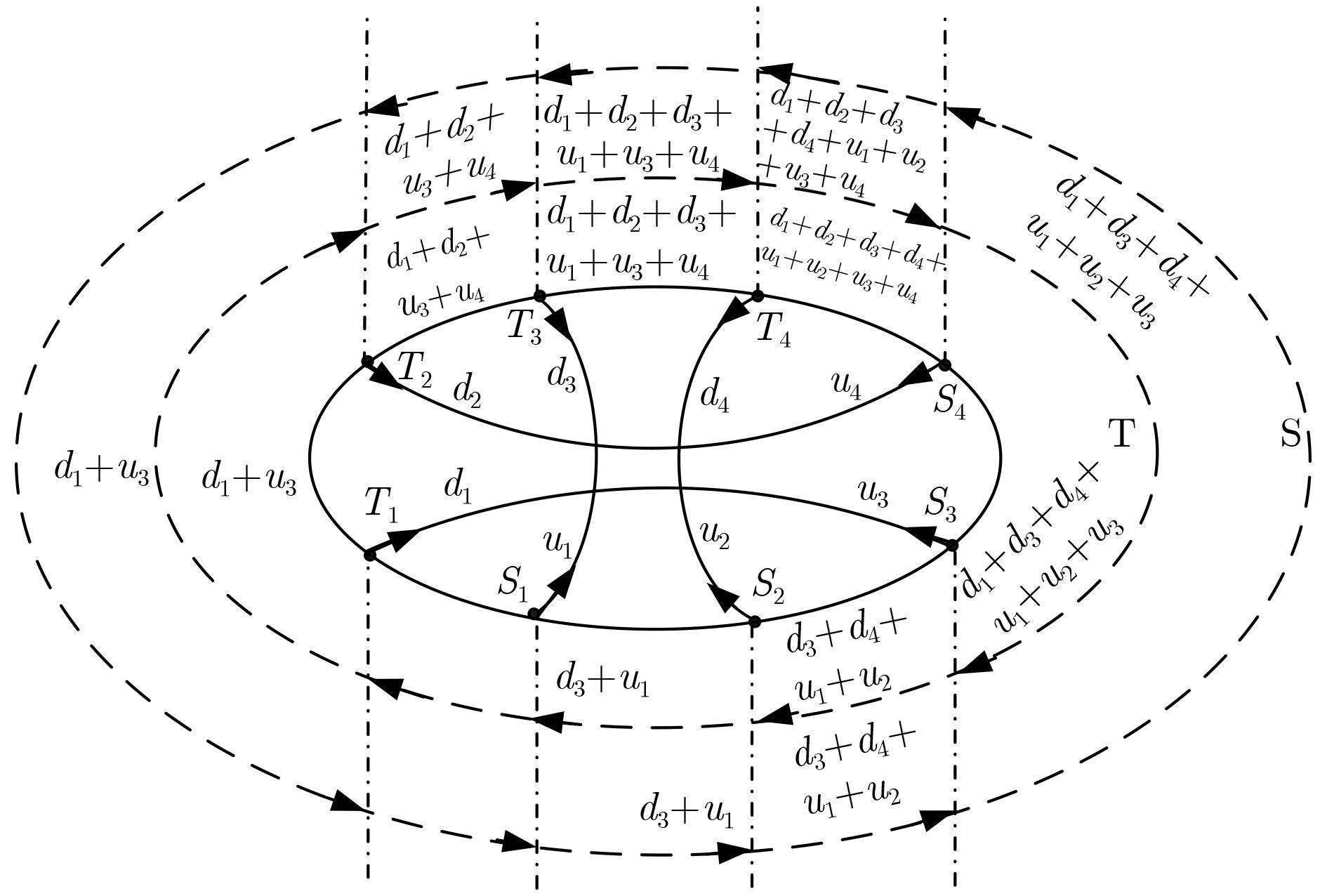
摘要: 针对现有可生存虚拟网络链路保护方法无差别对待所有虚拟链路、备份资源消耗多且故障后网络恢复时延长的问题,该文提出一种核心链路感知的可生存虚拟网络链路保护(CLA-SVNLP)方法。首先,综合考虑虚拟链路动态和静态两方面因素构建虚拟链路核心度度量模型,依据虚拟网络生存性需求,对核心度较高的虚拟链路进行备份保护;其次,将p圈引入可生存虚拟网络链路保护,依据虚拟网络特点构建p圈,为核心虚拟链路提供1:N保护,即每条核心虚拟链路平均消耗1/N条的备份链路带宽资源以减少备份链路资源消耗,并将单物理链路保护问题转化为多个p圈内的单虚拟链路保护问题;最后网络编码技术与p圈结合,将备份链路对核心虚拟链路提供的1:N保护转化为1+N保护,避免了故障后定位、检测及数据重传。仿真结果表明,该方法提高了备份资源利用率且缩短了故障后的网络恢复时延。Abstract: In order to solve the problems of all virtual links take without discrimination, high backup resource consumption and long network recovery delay after failures in existing survivable virtual network link protection methods, a Core Link Aware Survivable Virtual Network Link Protection (CLA-SVNLP) method is proposed. At first, the core degree metric model of virtual link is constructed by considering virtual link dynamic and static factors. According to virtual network survivable needs, virtual links with high core degrees are protected by backup resources. Then the p-cycle is introduced into survivable virtual network link protection and the p-cycle is constructed based on the characteristics of virtual network to provide 1:N protection for core virtual links. That means each core virtual link consumes 1/N backup link bandwidth resources and the backup link resource consumption is reduced. It also transforms the single physical link protection into single virtual link protection in multiple p-cycles. At last, the network coding and p-cycle are both used to transform the 1:N protection into 1+N protection for core virtual links which avoids fault location, detection and data retransmission after failures. Simulation results show that the proposed method can improve the utilization of backup resource and shorten the network recovery delay after failures.
-
Key words:
- Survivable virtual network /
- Link protection /
- Core link aware /
- P-cycle /
- Network coding
-
表 1 方法比较
-
LI Defang, HONG Peilin, XUE Kaiping, et al. Virtual network function placement considering resource optimization and SFC requests in cloud datacenter[J]. IEEE Transactions on Parallel and Distributed Systems, 2018, 29(7): 1664–1677. doi: 10.1109/TPDS.2018.2802518 MIJUMBI R, SERRAT J, GORRICHO J L, et al. Network function virtualization: State-of-the-art and research challenges[J]. IEEE Communications Surveys & Tutorials, 2016, 18(1): 236–262. doi: 10.1109/COMST.2015.2477041 赵志远, 孟相如, 苏玉泽, 等. 基于节点邻近感知与路径综合评估的虚拟网络映射算法[J]. 电子与信息学报, 2017, 39(8): 1979–1985. doi: 10.11999/JEIT161252ZHAO Zhiyuan, MENG Xiangru, SU Yuze, et al. Virtual network mapping algorithm based on node adjacent-awareness and path comprehensive evaluation[J]. Journal of Electronics &Information Technology, 2017, 39(8): 1979–1985. doi: 10.11999/JEIT161252 江逸茗, 马海龙, 卜佑军, 等. 面向收益最大化的虚拟网跨域映射策略[J]. 工程科学与技术, 2018, 50(2): 118–125. doi: 10.15961/j.jsuese.201601266JIANG Yiming, MA Hailong, BU Youjun, et al. Inter-domain virtual network embedding policy for revenue maximization[J]. Advanced Engineering Sciences, 2018, 50(2): 118–125. doi: 10.15961/j.jsuese.201601266 MARKOPOULOU A, IANNACCONE G, BHATTACHARYYA S, et al. Characterization of failures in an operational IP backbone network[J]. IEEE/ACM Transactions on Networking, 2008, 16(4): 749–762. doi: 10.1109/TNET.2007.902727 SHAHRIAR N, CHOWDHURY S R, AHMED R, et al. Virtual network survivability through joint spare capacity allocation and embedding[J]. IEEE Journal on Selected Areas in Communications, 2018, 36(3): 502–518. doi: 10.1109/JSAC.2018.2815430 KAMAL A E and AL-KOFAHI O. Efficient and agile 1+N protection[J]. IEEE Transactions on Communications, 2011, 59(1): 169–180. doi: 10.1109/TCOMM.2011.102910.090178 RAHMAN M R and BOUTABA R. SVNE: Survivable virtual network embedding algorithms for network virtualization[J]. IEEE Transactions on Network and Service Management, 2013, 10(2): 105–118. doi: 10.1109/TNSM.2013.013013.110202 GUO Tao, WANG Ning, MOESSNER K, et al. Shared backup network provision for virtual network embedding[C]. Proceedings of 2011 IEEE International Conference on Communications, Kyoto, Japan, 2011: 1–5. doi: 10.1109/icc.2011.5963301. LI Bin, LU Chao, QI Bing, et al. P-cycle based protection scheme with cycle multiplexing and capacity balance for multicast service in substation communication network[J]. International Journal of Electrical Power & Energy Systems, 2018, 102: 340–348. doi: 10.1016/j.ijepes.2018.04.038 JARRAY A and KARMOUCH A. Cost-efficient mapping for fault-tolerant virtual networks[J]. IEEE Transactions on Computers, 2015, 64(3): 668–681. doi: 10.1109/TC.2013.2295612 KAFAIE S, AHMED M H, CHEN Yuanzhu, et al. Performance analysis of network coding with IEEE 802.11 DCF in multi-hop wireless networks[J]. IEEE Transactions on Mobile Computing, 2018, 17(5): 1148–1161. doi: 10.1109/TMC.2017.2737422 HAI D T. On optimal designs of transparent WDM networks with 1+1 protection leveraged by all-optical XOR network coding schemes[J]. Optical Fiber Technology, 2018, 40: 93–100. doi: 10.1016/j.yofte.2017.11.009 WANG Zhiming, WU Jiangxing, and CHENG Dongnian. Coding-aware virtual network mapping for surviving single link failure[C]. Proceedings of 2014 IEEE International Conference on Communications, Sydney, Australia, 2014: 3025–3030. doi: 10.1109/ICC.2014.6883785. 梁宁宁, 兰巨龙, 张震. 基于拓扑感知的可重构服务承载网动态重构算法[J]. 通信学报, 2016, 37(2): 72–79. doi: 10.11959/j.issn.1000-436x.2016032LIANG Ningning, LAN Julong, and ZHANG Zhen. Dynamic topology awareness-based reconfigurable service carrying network reconfiguration[J]. Journal on Communications, 2016, 37(2): 72–79. doi: 10.11959/j.issn.1000-436x.2016032 苏玉泽, 孟相如, 孟庆微, 等. 环境自适应的拓扑联合感知虚拟网映射算法[J]. 电子与信息学报, 2018, 40(1): 79–86. doi: 10.11999/JEIT170325SU Yuze, MENG Xiangru, MENG Qingwei, et al. Environment adaptive and joint topology aware virtual network embedding algorithm[J]. Journal of Electronics &Information Technology, 2018, 40(1): 79–86. doi: 10.11999/JEIT170325 -






 下载:
下载: